FVulnerability overview: The potential impact on OEMs
A new denial of service vulnerability, recently reported by Qualcomm, is having a direct impact on automotive products. The vulnerability has not yet been detailed on either the official NVD or MITRE web pages.
The vulnerability (CVE-2022-33216) which affects several Qualcomm components and products, was defined as “a transient Denial-of-Service in Automotive due to improper input validation while parsing an ELF file”. The access vector is local and the security rating was defined as ‘High’. It also received a CVSS score of 6.0 but, as we know, the actual severity may differ based on the exploitability and relevance of the vulnerability to specific vehicle or component functionalities.
The affected product list is as followed:
QAM8295P, QCA6574A, QCA6574AU, QCA6595, QCA6595AU, QCA6696, SA6145P, SA6150P, SA6155, SA6155P, SA8145P, SA8150P, SA8155, SA8155P, SA8195P, SA8295P, SA8540P, SA9000P.
Identifying which products are affected
The discovery of CVE-2022-33216 and the lack of details surrounding it raises the question of which exact products are affected.
Most vehicle components are a complex mix of open-source and proprietary code, making it a challenge to manually detect which products are affected. Even if an SBOM exists, PSIRT teams must check that it is a living SBOM with all updated software components listed for each deployed version.
Using Cybellum’s automated Incident Response engine, teams can quickly discover which products or components are affected, as well as discover other critical vulnerabilities for that same component, as seen below:
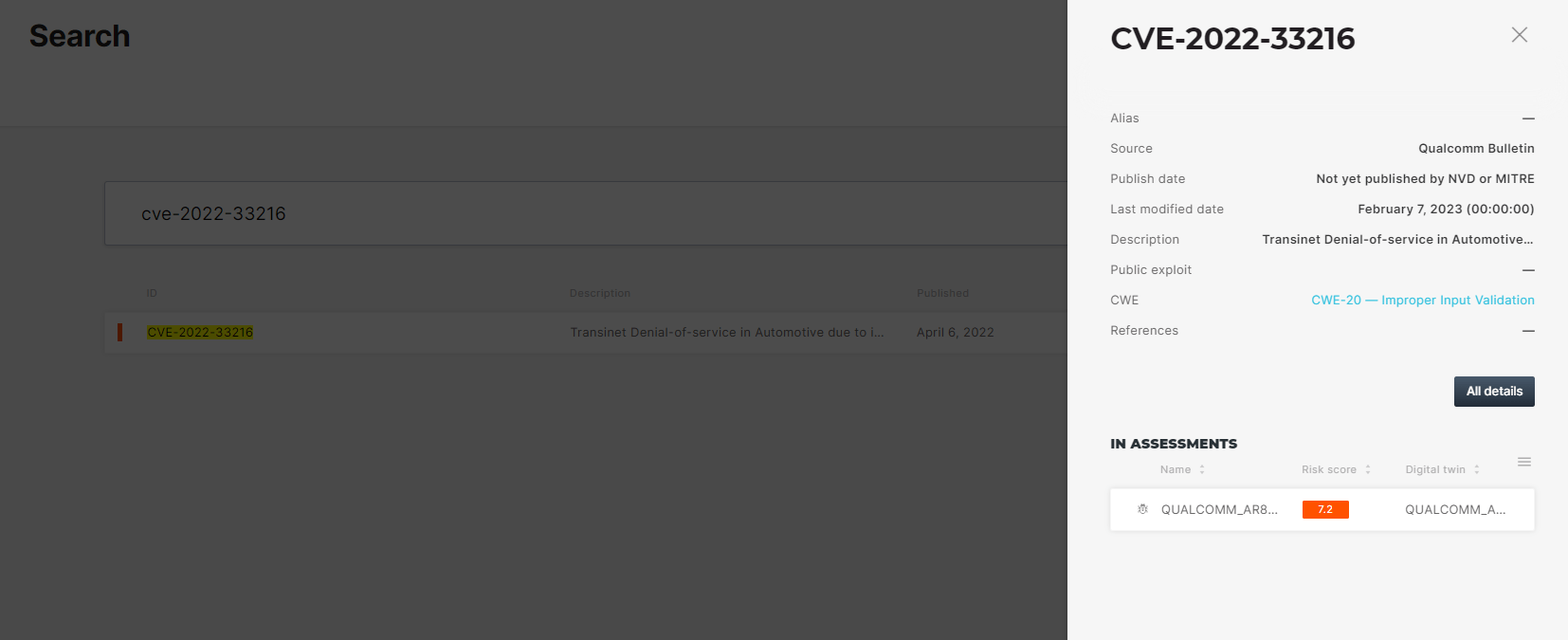
Finding which products are affected using Cybellum’s Product Security Platform
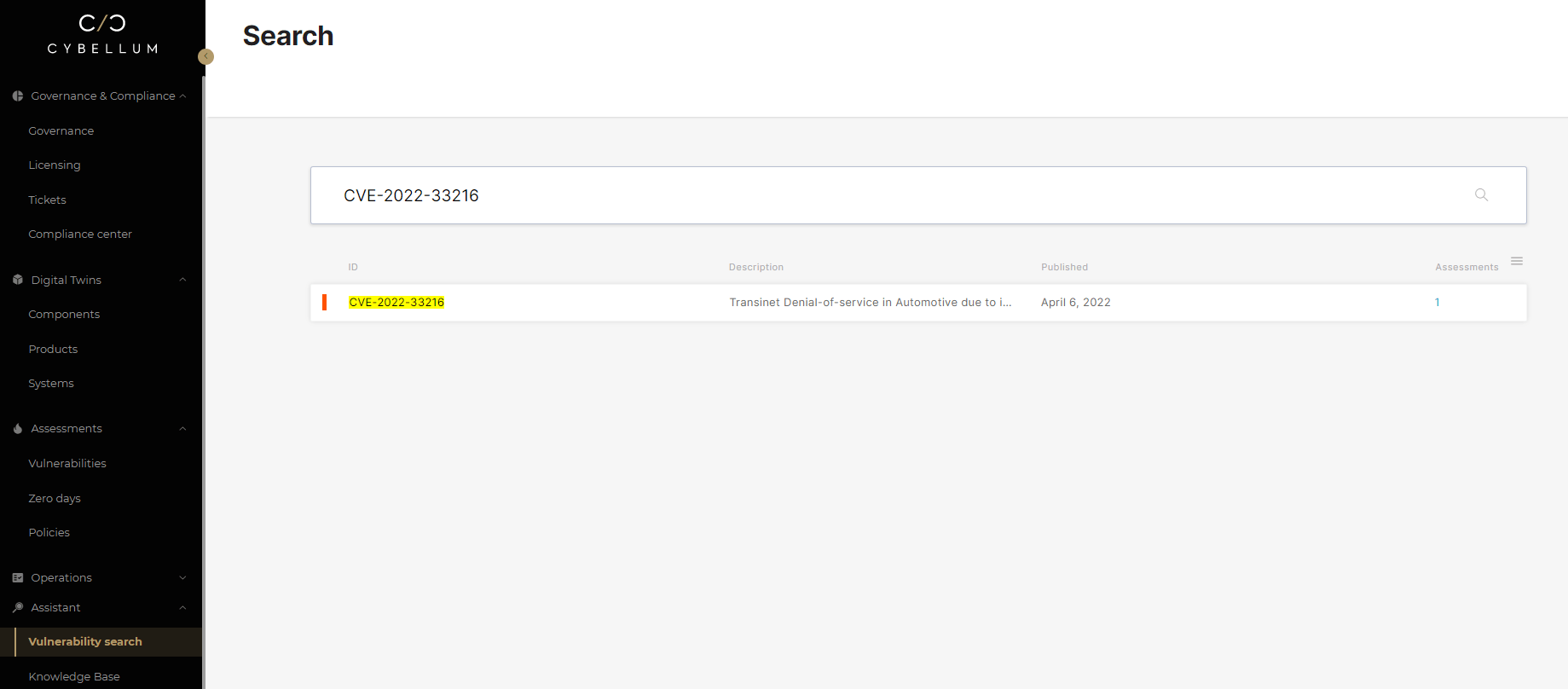
Extracting relevant information about the vulnerability
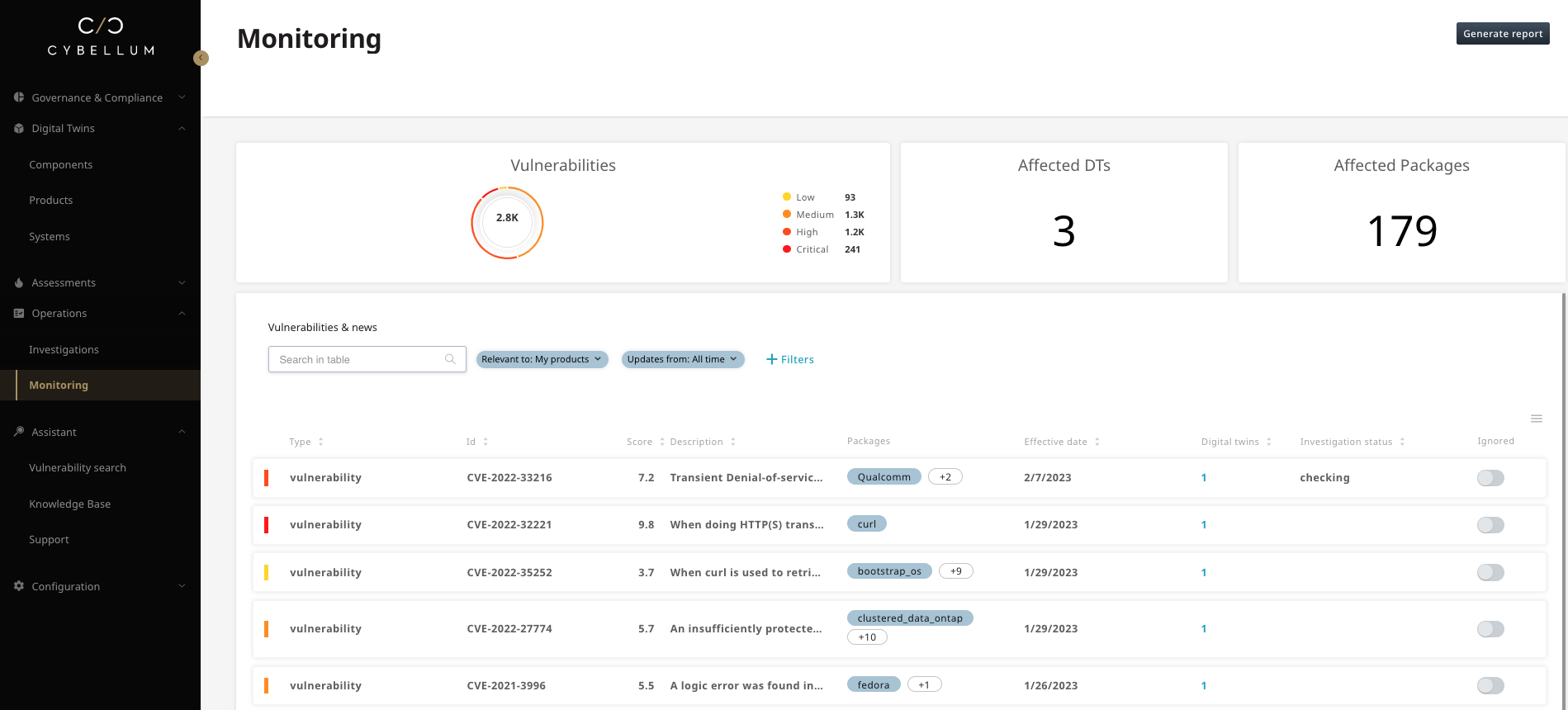
Monitoring for additional critical vulnerabilities for the same component
This is just one example of such an analysis, as the exact information per OEM requires an analysis of the specific SBOMs and product software of each specific product portfolio.
Executing continuous monitoring and incident response
This kind of event is yet another example of how critical timely incident response is for Automotive manufacturers and suppliers. By quickly identifying which products are affected by a new vulnerability the moment it is reported, PSIRT and product security teams can decide how critical it is, and mitigate accordingly. Cybellum’s Product Security Platform, specifically its Product Incident Response engine, enables that exact workflow, allowing teams to discover new vulnerabilities, even before they’re published on public sources such as the NVD. It then allows those teams to quickly identify affected products, get mitigation recommendations, and take action accordingly. By using automated VEX generation, teams can also extract the actual exploitability of each vulnerability in the context of their specific devices. To learn more about this capability, contact us.




