Newly discovered supply-chain vulnerabilities in common communication stacks can be exploited to take full remote control of connected devices, putting at risk millions of devices around the globe. Security researchers from Forescout and JSOF Research Labs have discovered nine vulnerabilities in four widely-used TCP/IP stacks affecting Domain Name Systems (DNS) implementations.
Dubbed NAME:WRECK due to the fact that parsing of domain names can break (i.e., “wreck”) DNS implementations in TCP/IP stacks, the vulnerabilities were discovered as part of Project Memoria to study the security of widely-used communication stacks that are incorporated by various vendors in their firmware.
This new set of vulnerabilities can be added to a growing list of TCP/IP stack vulnerabilities that includes Ripple20, Amnesia:33, Urgent/11 and others. They impact hundreds of millions of connected devices through complex software supply chains.
NAME:WRECK’s Potential Impact
These nine vulnerabilities are remotely exploitable, and once successfully exploited, could enable the following:
- Remote code execution(RCE), which essentially takes full control over the device. The result is a direct risk to component/device functionality and ultimately to the safety of its users
- Threat actors could exfiltrate data, potentially risking the privacy of device users
- Denial of service (DoS), directly affecting the functionality of devices/machines and potentially risking user safety
Affected TCP/IP Stacks
- FreeBSD – A stack found in open-source Unix-based OSs used in computers, printers and networking devices. It is affected by CVE-2020-7461, which can enable an attacker on the local network to remotely execute malicious/arbitrary code on the system, causing a heap-based buffer overflow. It has a high CVSS e score (7.7).
- IPNet – A popular stack by IPNet Solutions, geared for enterprise and telecom markets. It is used in unsupported versions of VxWorks (versions 6.5–7), as well as OSE, Integrity, ThreadX, ITRON and ZebOS, popular RTOS run by many IoT products. It is affected by CVE-2016-20009 and has a CVSS base score of 9.8 that can cause a DNS client stack-based buffer overflow on the message decompression function, resulting in remote code execution (RCE).
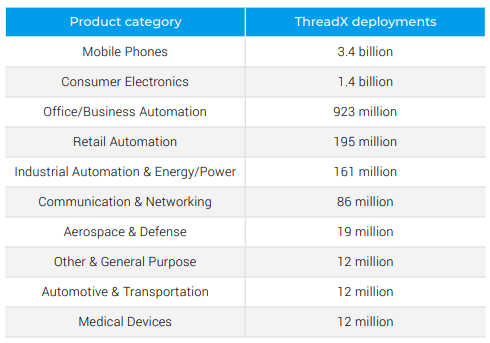
- NetX – commonly run by the ThreadX RTOS. The stack is used in mobile phones, consumer electronics, business automation solutions, in devices such as printers, smart clocks, systems-on-a-chip, and energy & power equipment in Industrial Control Systems (ICS) and even in the Automotive industry.

Source: Businesswire 2017In the DNS resolver component, functions _nx_dns_name_string_unencode and _nx_dns_resource_name_real_size_calculate do not check that the compression pointer does not equal the same offset currently being parsed, which could lead to an infinite loop. In the function _nx_dns_resource_name_real_size_calculate the pointer can also point forward and there is no out-of-bounds check on the packet buffer. The vulnerability can cause DoS and it has not yet been assigned a CVE number. It has a CVSS base score of 6.5.
- Nucleus NET – Part of Nucleus RTOS, and deployed in over 3 billion devices. Commonly used in building automation, OT, VoIP, as well as medical devices, storage systems, and aerospace systems. It is affected by six of the nine NAME:WRECK CVEs discovered:
-
- CVE-2020-15795 and CVE-2020-27009 – both have a CVSS base score of 8.1 and can enable an attacker with elevated privileges to execute malicious code and cause DoS.
- CVE-2020-27736 and CVE-2020-27737- have a CVSS base score of 6.5 and can cause DoS.
- CVE-2020-27738 – has a CVSS base score of 6.5. Malicious actors with elevated
- privileges can exploit this vulnerability to cause DoS.
CVE-2021- 25677 – has CVSS base score of 5.3 and can result in cache poisoning and spoofing attacks.
- CVE-2020-15795 and CVE-2020-27009 – both have a CVSS base score of 8.1 and can enable an attacker with elevated privileges to execute malicious code and cause DoS.
NAME:WRECK Variants
Siemens has issued additional advisories for variants of the NAME:WRECK vulnerabilities:
- ICSA-21-103-14 – A remotely exploitable vulnerability with a CVSS score of 5.3 that affects Siemens Nucleus products by enabling a threat actor to spoof DNS resolving or poison the DNS cache
- ICSA-21-103-05 – Another two remotely exploitable vulnerabilities that can cause DoS with a CVSS score of 7.5 that affect the following Siemens products: Nucleus 4, Nucleus NET, Nucleus ReadyStart, Nucleus Source Code, VSTAR
Recommendations
- Check your software asset inventory and the composition of each asset to understand which connected devices may be affected by this set of vulnerabilities.
- Knowing the software-bill-of-materials (S-BOM) is a good start to assess the relevance of this severe issue on your devices, but not enough. A deep understanding of the configuration and other mechanisms of the device are required.
- It’s also recommended to keep a watchful eye on security notifications provided by vendors that address these vulnerabilities.
How Can we Help
Cybellum enables OEMs and their suppliers to develop and maintain secure products. Our Cyber Digital Twins provides comprehensive visibility into device firmware, revealing their composition, characteristics and the context in which they operate. All from binary files, no source code needed.
Armed with a deep understanding of product software, Cybellum automates vulnerability management, compliance validation, continuous monitoring and incident response, minimizing risk to your customers and your organization.
We provide your product security and incident response teams with the visibility, context and automation needed to focus on the most relevant and pressing cyber threats, trace their origin across the supply chain and quickly mitigate them, pre and post-development.
Cybellum can help by eliminating doubts if vulnerabilities such as those described in this post impact your products. We can also expose how vulnerable you are by proactively presenting you with what is affected, what the real risk to your business is and how to remediate it.
If you have any questions or concerns, please don’t hesitate to contact us.
Other Helpful Resources
- https://www.forescout.com/company/resources/namewreck-breaking-and-fixing-dns-implementations/
- https://new.siemens.com/global/en/products/services/cert.html#SecurityPublications
- https://thehackernews.com/2020/12/amnesia33-critical-tcpip-flaws-affect.htm