NUCLEUS:13 is the latest in a long line of TCP/IP stack vulnerabilities that includes NAME:WRECK, Ripple20 and many others. The vulnerabilities have been discovered in the Nucleus TCP/IP stack owned by Siemens, and used in billions of devices.
What Is NUCLEUS:13?
NUCLEUS:13 is a set of 13 vulnerabilities that affect Nucleus NET, the TCP/IP stack included with Nucleus, a real-time operating system (RTOS). The stack and the RTOS were originally developed by Accelerated Technology, Inc. (ATI) in 1993, then acquired by Mentor Graphics in 2002 and finally by Siemens in 2017.
Since its original release 28 years ago, Nucleus has been deployed in many industries and devices including medical devices / IoMT, vehicles, Industrial PLCs, IoT equipment and many more.
Why Is NUCLEUS:13 So Threatening?
The NUCLEUS:13 vulnerabilities can be used to take over, crash, or leak information from devices that run older versions of the Nucleus RTOS. Because of its wide use in over three billion devices, the potential attack surface of devices affected by these vulnerabilities is huge.
The new vulnerabilities allow for Remote Code Execution (RCE) or Denial of Service (DoS), with three of the thirteen new vulnerabilities being critical and having CVSS scores of either 9.8 or 8.8. The most concerning of these vulnerabilities and the easiest to exploit is CVE-2021-31886, a buffer overflow vulnerability that may enable RCE, that received a rare 9.8 out of 10 rating.
If a device with one of the NUCLEUS:13 vulnerabilities is exploited, attackers may be able to gain unauthorized access to a device or a network, remotely execute malicious code or launch a denial-of-service attack.
| CVE | Affected Component | Potential Impact | CVSSv3 |
| CVE-2021-31886 | FTP Server | RCE | 9.8 |
| CVE-2021-31884 | DHCP Client | DoS, Out-of-bound reads/writes. Impact depends on how the client is implemented. | 8.8 |
| CVE-2021-31887 | FTP Server | RCE | 8.8 |
| CVE-2021-31888 | FTP Server | RCE | 8.8 |
| CVE-2021-31346 | IP/ICMP | Information leak/DoS | 8.2 |
| CVE-2021-31889 | TCP Server | DoS | 7.5 |
| CVE-2021-31890 | TCP Server | Dos | 7.5 |
| CVE-2021-31885 | TFTP Server | Information Leak | 7.5 |
| CVE-2021-31345 | UDP | DoS, Information leak. Impact depends on how UDP is implemented. | 7.5 |
| CVE-2021-31881 | DHCP Client | DoS | 7.1 |
| CVE-2021-31883 | DHCP Client | DoS | 7.1 |
| CVE-2021-31882 | DHCP Client | DoS | 6.5 |
| CVE-2021-31344 | ICMP | Confused Deputy | 5.3 |
How to Mitigate the NUCLEUS:13 Threat?
Siemens, the owner of Nucleus, has released patches for all of these vulnerabilities. Device manufacturers who have implemented the TCP/IP stack or RTOS will have to release updates to their customers for the affected products.
But before moving on to patching, consider the following steps to make sure you address all impacted devices in your portfolio:
STEP 1 – ASSESS IMPACT
First you’ll need to check if your devices/products are indeed impacted by Nucleus:13. It would be really beneficial to have a repository of your product Software Bill-of-Materials (SBOM) and other product characteristics that also maps affecting vulnerabilities.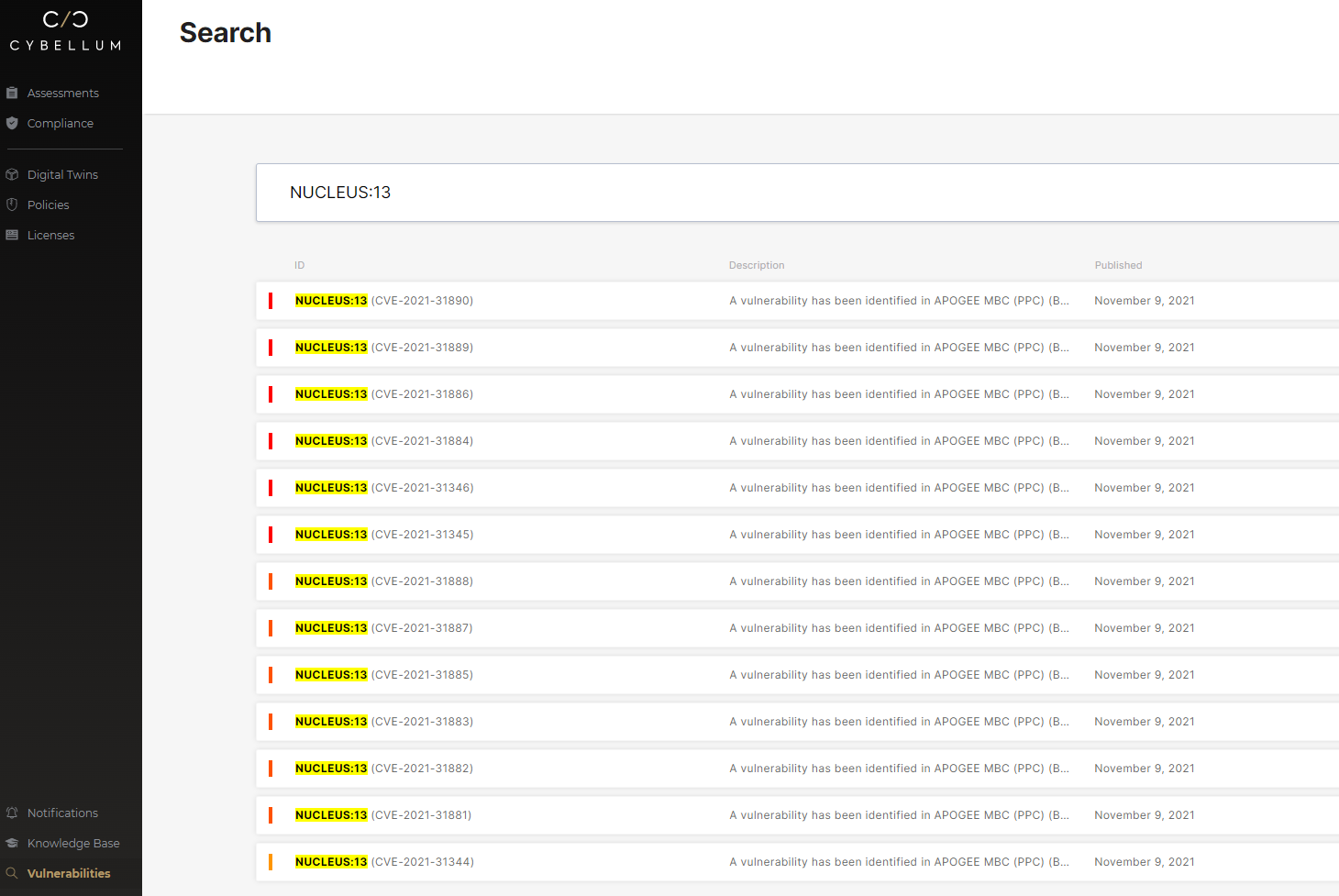
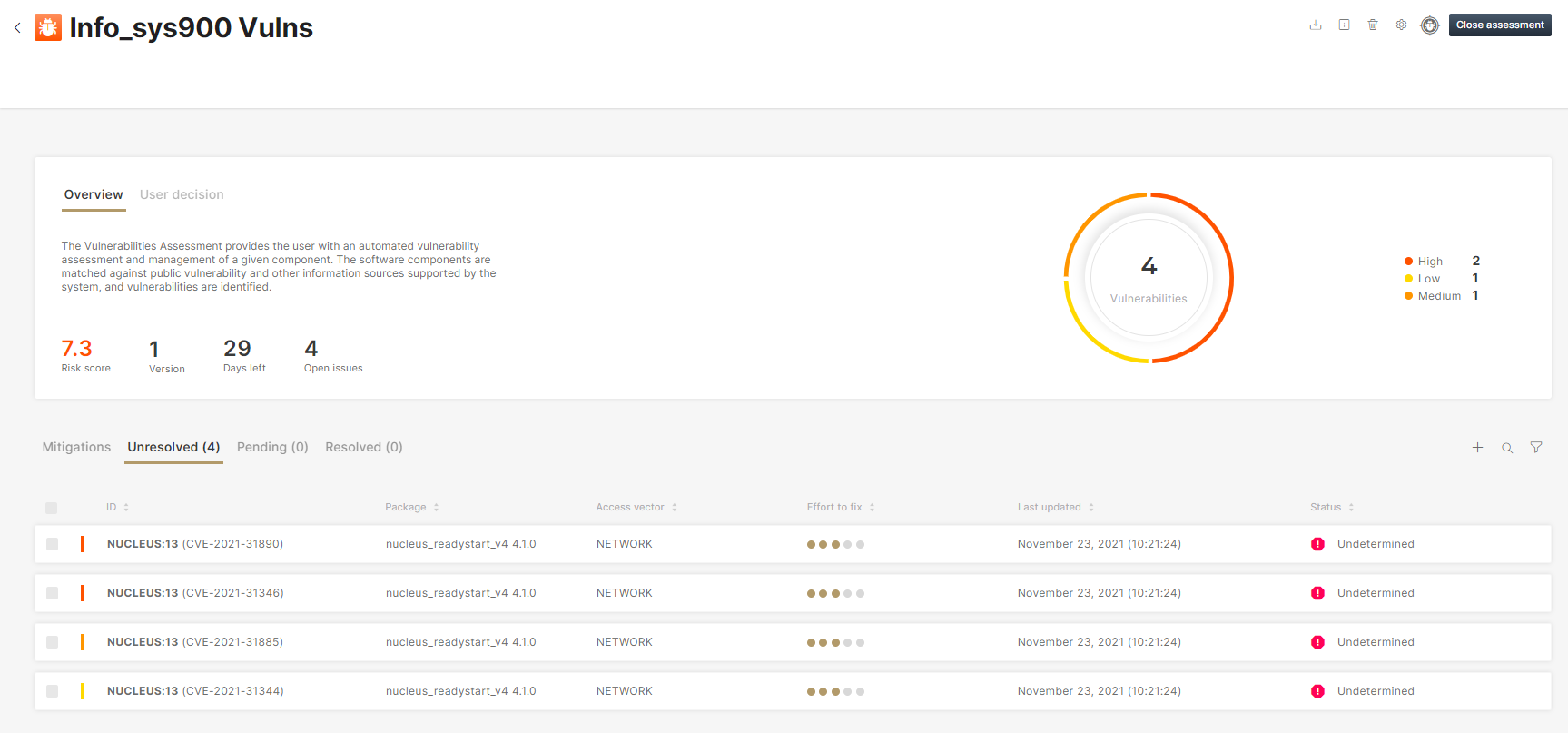
Once all affected products/devices have been identified you can move to the next step.
STEP 2 – MITIGATE THE RISK
While patching may be difficult, it is still the number one action to take. Siemens Security Advisory SSA-044112 contains patching and remediation information.
It’s important to note that while that long term patch application process plays out, users of the device, such as utilities or hospitals, will still need to secure devices affected by NUCLEUS:13.
Device OEMs can help them in the interim by reconfiguring devices to minimize risk, for example, by disabling support for unused protocols.
STEP 3 – KEEP MONITORING
It is common that, after a major vulnerability has been discovered, hackers find new ways of exploiting it or find similar (or related) security holes that could further compromise products.
Therefore, it is recommended that you monitor threats over time to ensure that the vulnerability has been removed.
How Can Cybellum Help?
Third-party software of an open-source or commercial nature pose a variety of software supply chain security challenges to connected device manufacturers. Nucleus:13 is yet another painful example.
Cybellum’s Product Security platform secures your software supply chain, with SBOMs and monitoring that validates the security of your device’s software from design through post-production.
Our experts can show you how. Talk to us or schedule a demo.




