A guest blog by Mr. Tetsuya Mikami, Senior Manager at Deloitte Tohmatsu Consulting LLC.
Part 1 of this two blog series can be found here.
Getting Ready to Handle Cyber Incidents
Incident response requires speed and prompt decision making. Although the majority of companies in Japan are enforcing their incident response by forming a PSIRT (Product Security Incident Response Team), you need a security organization with a CISO (Chief Information Security Officer) in place, coupled with an escalation scheme to allow for prompt decision making and ensure accountability which will surely be required.
In the near future, I would expect cyber incidents to become a reimbursement or compensation issue, just like a recall or market claim caused by failure of a vehicle part. Thus, reimbursement / compensation for cyber incidents also needs to be in place.
In the US or Europe, most of the contract terms & conditions state the obligation for insurance coverage, and obligation terms for cyber insurance will be added in near future.
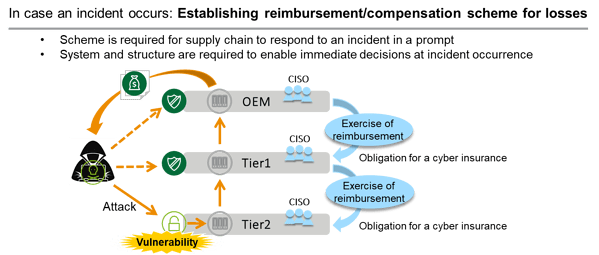
Figure 6: Getting Ready for Incident Occurrence
The calculation method for cyber incident reimbursement / compensation costs will be different from those related to parts or design failure. The cost could exceed the development cost of parts or the net order amount price, since it will need to compensate for the losses or damages caused by an incident.
For example, the price of a regular credit card data is around 20 to 50 USD in the DarkWeb. Suppose 100,000 vehicles were hacked fleet-wide by a ransomware, the ransom could possibly reach $5 million. At this point, prompt decision must be made to pay the ransom or to compensate for the actual losses.
The reason that only few cyber incidents have been reported in the news is because organizations (regardless of industry in which they operate) simply choose to pay the ransom.
If cyber threat prevention fails and breaches do happen, making the right decisions that will minimize losses is critical to the organization.
Global Trends in Automotive Cybersecurity
Around 5 years ago, various approaches to cyber risk measures were examined as the automotive industry started to pay more attention to cybersecurity. Companies thought they should address every cyber threat they could think of, and a lot of OEMs showed interest in V-SOC (Vehicle Security Operation Center) and IDS/IPS (Intrusion Detection and Prevention Systems).
However, at an early stage, the approach to focus on underlying risk assessment became the mainstream in the US and Europe. It is considered wise to take measures against risks that may actually cause loss or damage to the company or the organization.
The automotive cybersecurity market is growing at a CAGR (compound average growth rate) of 21.4 % and the market is expected to expand to $5.56 billion by 2025. As previously mentioned, in-vehicle software is growing and connected features are becoming more complex. Accordingly, cyber risk measures towards the growing volume of data and towards data exchanged from the vehicles are becoming more and more important, although priorities vary between countries or regions, where safety is a prioritized first in some regions while financial assets are most important in others.
“Assets” undergo risk assessment in order to be protected. There is a “process”, along with ”resources & organizations” to ensure the security throughout the product lifecycle. There is also a ”process” and ”resources & organizations” to address incidents immediately and accurately as well as “technology” to support, optimize and accelerate process execution.
In the US and Europe, risk mitigation matures as the CISO-backed decision scheme is implemented, and contractual terms & conditions and reimbursement / compensation scheme for incident handling are being defined and established.
These all help to mitigate the impact of cyber risks. In terms of process and technology, realization of timely and nimble vulnerability management is gaining a lot of attention, and vulnerability management programs and tools are established quickly.
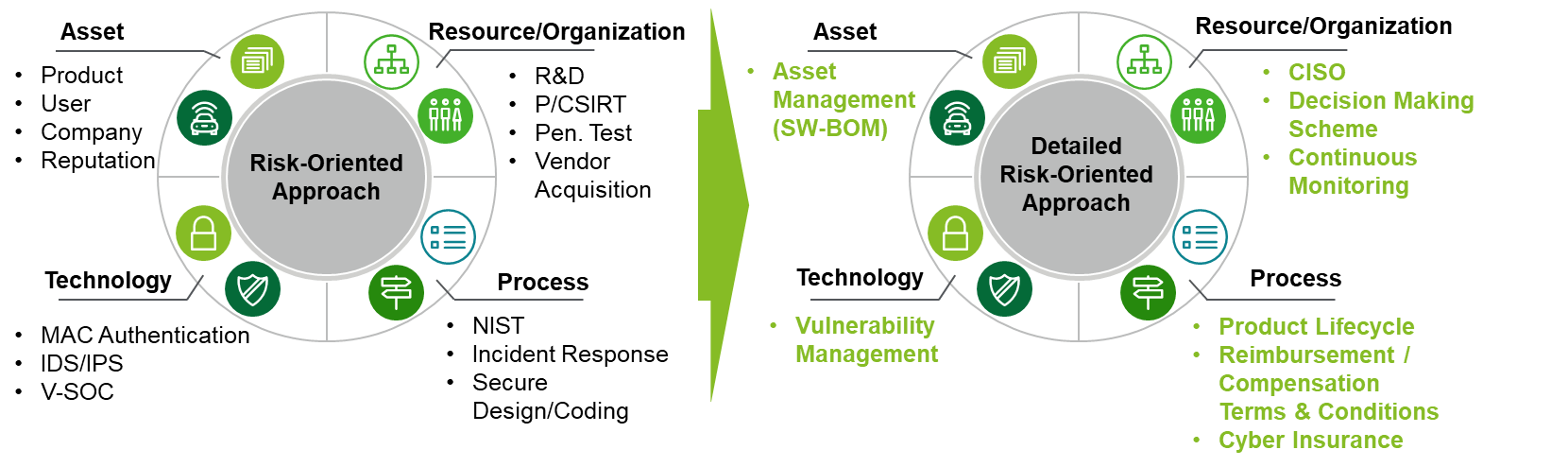
Figure 7: Evolution of Risk Oriented Cyber Security Countermeasures
Looking at real world cyber risks, the time allowed from discovery of vulnerabilities to taking measures to protect the entire product line is just one month. I would expect this time-frame to become even shorter. In the real world today, the risk of attacks by exploits will increase after a month.
Take smartphones for example, minor OS updates are scheduled almost every month and it only takes a week from planning to distribution for applications. This smartphone time-frame is also signalling that one month will be the goal to update functions via Over-the-Air (OTA) updates, to match the user’s expectations (consumers see the time-frame of smartphone updates as a base-line).
In-vehicle software changes or extensions are also part of vulnerability management, meaning that “1 month” is also a target time-frame to complete the process.
Automotive Cybersecurity Requirements
Considering the fact that cyber attacks start from discovering vulnerabilities and upcoming regulations require vulnerabilities to be managed, vulnerability management should become the basis for automotive cybersecurity measures.
In order to have vulnerability management in place, the following actions must be iterated continuously:
- Monitor vulnerabilities occurring every few hours
- Impact analysis for all product lines
- Develop and evaluate a patch (if impacted)
- Distribute and apply a patch to applicable product or specifications (if needed) using OTA
For many Japanese companies, I will assume point #2 would be the bottleneck. To execute impact analysis in a timely manner, software configuration for all variations or specifications must be visible and accessible throughout the entire product line.
However, from my personal experience, not many Japanese OEMs have software management schemes organized in a way to have configuration information available and accessible immediately in one place.
If the software configuration for the entire product line is not visible or accessible, there will be an increased risk to miss some specifications or models that needs patching. In turn, it may lead to a lack of evaluations on patch development, and in the worst case scenario, it may result in a market defect.
The importance or purpose of software configuration management is not only to prevent cyber incidents, but also to improve incident responses.
Whenever an unfortunate cyber incident occurs, vehicles with the specifications similar to the affected vehicle have the same risk, meaning that points #2 to #4 above must be executed promptly and the software configuration must be visible and accessible to do so.
In order to execute all steps in an adequate time-frame, software configuration management scheme, continuous vulnerability management process, and organization structure and resources are mandatory. However speaking of time-frame, technology will be a big help.
Cybellum’s Product Security Platform has a globally established reputation for enabling timely and speedy vulnerability management. Product Security Assessment running on the platform mirrors the configuration management environment enabling #1 and #2, which will highly contribute to identifying vulnerabilities that will impact the product line in an instant and constant manner.
Although tools will highly contribute to enhancing cybersecurity measures, cybersecurity is not just a story of tools. Cybersecurity measures must be based on the cyber risk to one’s company or organization. Cybersecurity measures should cover risks to systems, resource, role and responsibilities, processes, policies, standards and so on. Figure 8 below summarizes the cybersecurity measures companies or organizations need to be ready for.
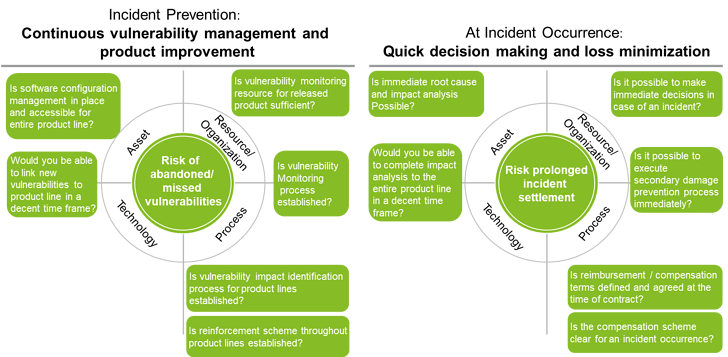
Figure 8: Cybersecurity Requirements Based on Risk Assessment
Now, to how many questions in Figure 8 would you answer “Yes” ?
I assume many companies are now working on being compliant with UNECE WP.29, however, this isn’t the only goal. I would highly recommend building measures and getting ready to handle cyber risks. Unfortunately, the automotive industry is already full of cyber threats which are gaining momentum every moment.