It hasn’t been an easy year for cybersecurity pros in the automotive industry.
Hackers are increasingly setting their sites on connected automotive products – David Colombo’s much-publicized ethical Tesla hack, a ransomware attack against Honda, and a suspected attack on a local Toyota supplier are only a few examples from the rapidly evolving threat landscape.
Supply chain security risks continue to rise, resulting in an increased reliance on complex software supply chains for connected vehicles. To compound the problem, recent supply chain shortages and breakdowns have pushed the automotive industry to rely on new and often un-vetted suppliers.
While the regulatory requirement for SBOMs is one of the ways to address supply chain security, many teams are still struggling to find a way to generate a compliant SBOM that provides a complete system view, covering proprietary, third party, and open source code without slowing down production.
We published our latest State of Automotive Cybersecurity Report 2022 to provide the automotive product security community with insights and information on the current state of automotive cybersecurity, a look at the challenges to becoming WP.29 compliant, and provide insights and best practices for achieving cybersecurity.
Here is our quick rundown of the reports insights, the main automotive cybersecurity challenges facing products security teams today, and how to best address them.
Supply Chain Security: Achieving Complete Visibility
A little over a year ago, the White House addressed the alarming rise in attacks on supply chains and issued the Executive Order on Improving Cybersecurity, accelerating the need for software developers and suppliers to generate up-to-date SBOMs containing all of their software components.
SBOMs help teams monitor their software for outdated and vulnerable components and mitigate risks as soon as they are found. Looking at the data, it’s clear that continuously generated SBOMs throughout the product lifecycle are critical for ensuring updated and vulnerability-free products.
As software continues to take over the automotive industry, managing software supply chain security is more important than ever. Our research shows that the top 10 most popular components in use in automotive products in the past year were open source.

While open source components help developers speed up processes by using software libraries created and maintained by a trusted community of developers, they also come with their own set of security risks.
What Do We Know About the Open Source Components Driving Our Connected Cars?
When it comes to open source, traditional security testing tools aren’t applicable. It’s up to developers to track the security updates and advisories published across the open source community, and then make sure they quickly mitigate any vulnerabilities found in the open source software that they are using.
Our research shows that the most common CVEs detected in automotive components were in extremely popular open source components. It’s also worth noting that most of the vulnerabilities are not new. The list consists of vulnerabilities from 2017, 2019, and 2020. Looking at the data, it’s clear that the chances are high your developers are using at least a few vulnerable software versions.
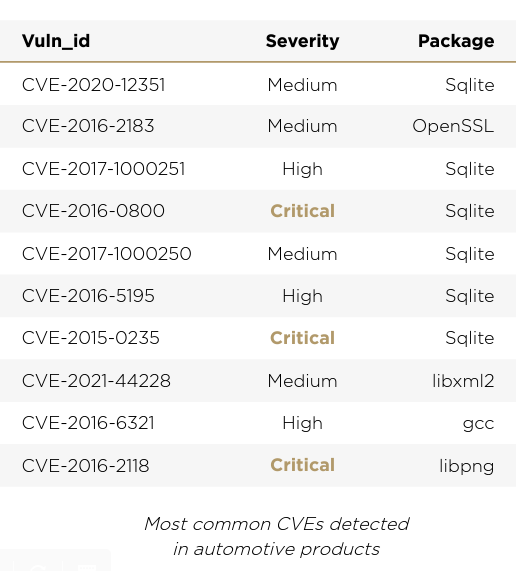
Keep Calm and Update Your Software Components
Cyber attacks on connected devices are no longer a rare occurrence, and a public CVE provides hackers with a recipe and roadmap for exploits. We took a closer look at the most common vulnerabilities in automotive products, and checked the amount of outdated software versions in use.
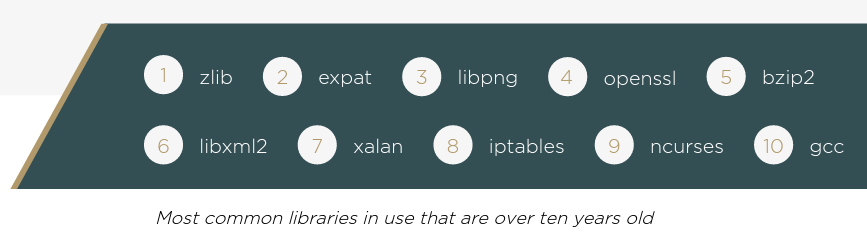
Results show that 24% of connected automotive products contain software versions that are older than 10 years. Looking at the most common libraries in use that are over ten years old, we once again found that open source software is often neglected by product security teams.
Outdated and vulnerable versions in automotive products present one of the biggest challenges to the automotive industry, since they might affect vehicles that are already on the road. As both regulation and threats evolve, it’s critical that product security teams put tools and processes in place to ensure that this type of risk is mitigated as soon as possible.
Prioritization: Mitigating the Vulnerabilities that Matter Most
Detection is an important first step towards securing software – but then security and development teams must focus on the most critical issues, and mitigate them as quickly as possible. We looked at the different types of published vulnerabilities to see how teams can speed up and scale their vulnerability management processes.
As the automotive software ecosystems become more and more complex, early and continuous monitoring for vulnerabilities is just the first step. Even if product security teams have tools and processes in place for this crucial practice, they are then left to deal with an increasingly long list of issues to mitigate. Simply looking at the CVSS score is not enough, as most vulnerabilities are rated high or critical – leaving teams to sort through the list and decide which vulnerabilities demand immediate attention.
According to recent data, manual vulnerability management can take months, some research puts mitigation of high-severity vulnerabilities at nearly 250 days – an unacceptable timeframe, especially considering the ever-growing list of vulnerabilities. In order to speed up and scale the vulnerability management process, it’s crucial to focus on the vulnerabilities that present the highest risk to your organization.
In our research, we found that only a third of detected vulnerabilities affect the product. Using advanced technology to analyze the vulnerabilities and cut down the long list is a crucial step in achieving quick mitigation.
Facing the Latest Automotive Cybersecurity Challenges Head-On
As product security teams in the automotive space continue to work hard to achieve cybersecurity and compliance, it’s critical to put a mature cybersecurity strategy in place.
This requires implementing new processes and policies from the earliest stages of development all the way to post-production. Cybellum’s Product Security Platform helps product security pros speed up and scale cybersecurity throughout the entire product lifecycle – from SBOM’s, to vulnerability management and incident response.
Want to learn more about the latest automotive cybersecurity trends? Download Cybellum’s State of Automotive Cybersecurity 2022 Report




