A joint Cybersecurity Advisory from the National Security Agency (NSA), the Cybersecurity and Infrastructure Security Agency (CISA), and the FBI, published Tuesday, June 8, outlines how state-sponsored hackers from the PCR (People’s Republic of China) have been exploiting known vulnerabilities – CVEs – to target public and private sector organizations worldwide, including in the United States, to establish a broad network of compromised infrastructure.
The advisory, titled “People’s Republic of China State-Sponsored Cyber Actors Exploit Network Providers and Devices”, it is built on previous NSA, CISA and FBI reporting, “to inform federal and state, local, tribal, and territorial (SLTT) government; critical infrastructure (CI), including the Defense Industrial Base (DIB); and private sector organizations about notable trends and persistent tactics, techniques, and procedures (TTPs)”.
The report is divided into three parts:
- The common vulnerabilities exploited by PRC state-sponsored cyber actors
- How open source and custom tools were used to target telecommunications and network service providers
- Recommended mitigations.
Hackers Have Been Exploiting Common Vulnerabilities For Years
The advisory details how PRC actors have targeted and compromised major telecommunications companies and network service providers, mainly by exploiting known vulnerabilities – in unpatched network devices.
It explains how the hackers exploit vulnerabilities to compromise unpatched network devices. Network devices, like Small Office/Home Office (SOHO) routers and Network Attached Storage (NAS) devices, serve as additional access points to route command and control (C2) traffic, and act as midpoints to conduct network intrusions on other entities.
According to the report “Over the last few years, a series of high-severity vulnerabilities for network devices provided cyber actors with the ability to regularly exploit and gain access to vulnerable infrastructure devices.”
The report goes on to map out the widespread campaigns that started in 2020 – to rapidly exploit CVEs in unpatched network devices. “This technique has allowed the actors to gain access into victim accounts using publicly available exploit code against virtual private network (VPN) services or public facing applications – without using their own distinctive or identifying malware—so long as the actors acted before victim organizations updated their systems.”
The advisory provided a list of the network device CVEs that the NSA, CISA, and the FBI consider the most frequently exploited by PRC state-sponsored cyber actors since 2020:
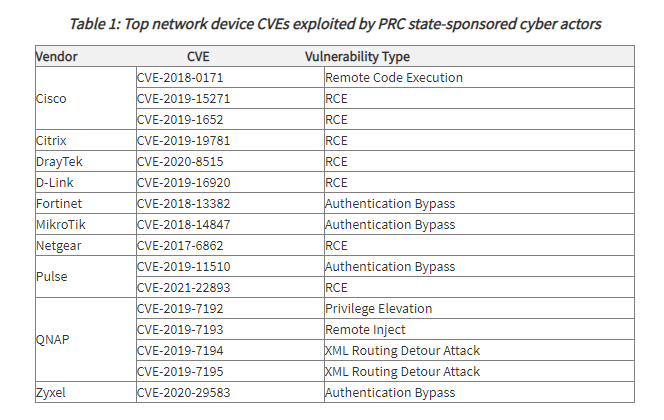
Threat Actors Continuously Adapt Their Methods to Dodge Detection
NSA, CISA, and the FBI have observed that the hackers continuously update tactics to bypass defenses. They monitor network defenders’ accounts and actions, and then modify their campaign to remain undetected.
Hackers modify their infrastructure and toolsets immediately following the release of information related to their ongoing campaigns. The agencies have also found that the threat actors often combine their customized toolset with publicly available tools, especially by using tools that are native to the network environment, to hide their activity in plain sight by blending into the network’s normal activity.
The advisory points out that the vulnerable devices are often overlooked by cyber defenders, who struggle to maintain and keep pace with routine software patching of Internet-facing services and endpoint devices.
The Targets: Telecommunications and Network Service Providers
The threat actors often leverage open source tools for recon and vulnerability scanning activities. They’ve used open source router specific software frameworks RouterSploit and RouterScan to identify makes, models, and their known vulnerabilities. These tools enable exploitation of SOHO and other routers manufactured by major industry providers, including Cisco, Fortinet, and MikroTik.
When the hackers get a foothold into a telecommunications organization or network service provider, they identify critical users and infrastructure – including systems that are critical to maintaining the security of authentication, authorization, and accounting. Once they identify a critical RADIUS (Remote Authentication Dial-In User Service) server, the threat actors gain credentials to access the underlying SQL database, and use SQL commands to dump both cleartext credentials and hashed passwords for user and administrative accounts.
The hackers use the credentials with custom automated scripts to authenticate to a router via Secure Shell (SSH), execute router commands, and save the output. The scripts targeted Cisco and Juniper routers, and saved the output of the executed commands, including the current configuration of each router. These configurations were exfiltrated to the hackers’ infrastructure.
The advisory estimates that the cyber actors probably used additional scripting to further automate the exploitation of medium to large victim networks, with many routers and switches, to gather massive numbers of router configurations that would be necessary to successfully manipulate traffic within the network.
The hackers then returned to the network, and authenticated and executed router commands to quietly route, capture, and exfiltrate traffic out of the network to actor-controlled infrastructure.
Cybersecurity Advisory Recommendations
The US agencies’ joint advisory ends with an urgent call that organizations mitigate the vulnerabilities listed in this advisory by:
- applying the available patches to their systems,
- replacing end-of-life infrastructure, and
- implementing a centralized patch management program
The advisory includes a detailed description of the CVEs and their patches, to help organizations implement the urgent mitigation recommendations.
Key Takeaways for Product and Device Security
This new advisory from the US security agencies highlights once again how malicious players will target outdated vulnerable software components to gain a foothold into organizations. This is another reminder for product and device manufacturers to upgrade their cybersecurity processes, and monitor continuously for security risks.
Extensive cybersecurity research shows that once one CVE is successfully exploited, actors will continue to target the vulnerable component, and new CVEs will follow. That means that one-time or periodic monitoring of the components that make up our connected devices is simply not enough.
In order to ensure that malicious players can’t find a way into the network, product and device security teams must continuously monitor their components, and remediate as quickly as possible when a new CVE is discovered in a version in their system.
Contact us to learn how Cybellum’s Product Security Platform helps product and device security teams continuously monitor their software to detect and remediate vulnerabilities.




