VEX reports have finally hit the mainstream and the excitement surrounding them has as much to do with automation as it does with vulnerability management.
To appreciate the full practicality of Vulnerability and Exploitability Exchange (VEX) reports, we need to go back to our old friend, the Software Bill of Material, endearingly known as ‘SBOM’. These bills of material list all known software components that go into a specific device, allowing it to operate the way it does. But, the shift from hardware components to software-driven components has boxed out many developers from prying deeper into the embedded software packets that exist inside– blocking them from properly identifying and mitigating vulnerabilities.
That’s where SBOM calls in some muscle- the VEX report.
Once an SBOM is automatically extracted, that information is reviewed to identify any known vulnerabilities within the context of the product’s architecture. Once compiled, it’s a powerful report, relied on by developers through post-production Product Security Incident Response Teams (PSIRT). But, as companies begin scaling their SBOM development and VEX reports alike, can companies really manage all the incoming data at scale?
SBOM and VEX- the have and have-nots
To answer the question of whether to generate and manage VEX reports, it’s important to understand the damage caused by NOT having one.
While SBOM generation, and by extension VEX report generation, seems straightforward the problem becomes apparent once acknowledging that a product can have hundreds of components- each in need of their own investigations. Automating these reports allows companies to understand if a bluetooth component has a vulnerability is actually a 9.6 or if the vulnerable configuration does not apply to them, bringing it down to a near 0.
We saw this in late 2021 when Log4j sent the product security world into a frenzy as they tried to identify if any components within their products contained this vulnerable component.
As hackers raced to breach organizations using this common vulnerability, those with proper SBOM management quickly mitigated their products– patching software and making it home in time for dinner. Those without organized SBOMs took months to identify which products were impacted– leaving them exposed until discovered.
As customers panickedly asked suppliers if their products were impacted by Log4j, staff was redirected to field questions on breaches, potential impact, and if they’ve rolled out a patch for specific models in the field. As time went by and no new answers were given, frustration built.
Using VEX to improve prioritization and mitigation
Ensuring ongoing protection, not just a quick reaction following a breach, companies have heeded the White House’s urgent call to generate SBOMs for all new and existing products.
According to Tom Alrich, a private Supply Chain Cybersecurity consultant, with experience in both the private and public center, including the US NTIA Energy Sector stated: “Probably 90%+ of what’s in the NBD, alongside their CVE name, are not necessarily relevant to your device. If 100 vulnerabilities are returned, you may contact a supplier to discover that 95 of those hundred are not actually exploitable. Essentially, those vulnerabilities are not really there. There are various reasons why that can happen but ultimately, they are not relevant to your device.”
Beyond the compliance, licensing, and other benefits, SBOMs allow organizations to compare their components against private and public databases to identify unaddressed vulnerabilities that may have found their way into products. Their findings will be placed in a machine-readable format VEX.
With detailed SBOM management at scale, organizations can begin to generate VEX reports to understand which risks matter to them and which are only specific to configurations that don’t exist within their products.
Automating the VEX generation process alongside SBOMs, cybersecurity and product security teams can really get cooking. As a prioritization engine, vulnerabilities can be addressed one by one- or not at all!
Reaping VEX’s benefits with automation
Ultimately, for your team to generate VEX reports with Cybellum’s Product Security Platform, they only need to follow a simple process that is easy to use at scale.
When conducted manually, the VEX generation is cumbersome and risks being inaccurate, due a potential lack of real-time data or human error as the sheer number of tasks is too great for people to conduct both quickly and efficiently.
With Cybellum’s Product Security platform, creating a report is as simple as going to your SBOM, selecting reports, choosing ‘VEX’, and clicking ‘Export’.
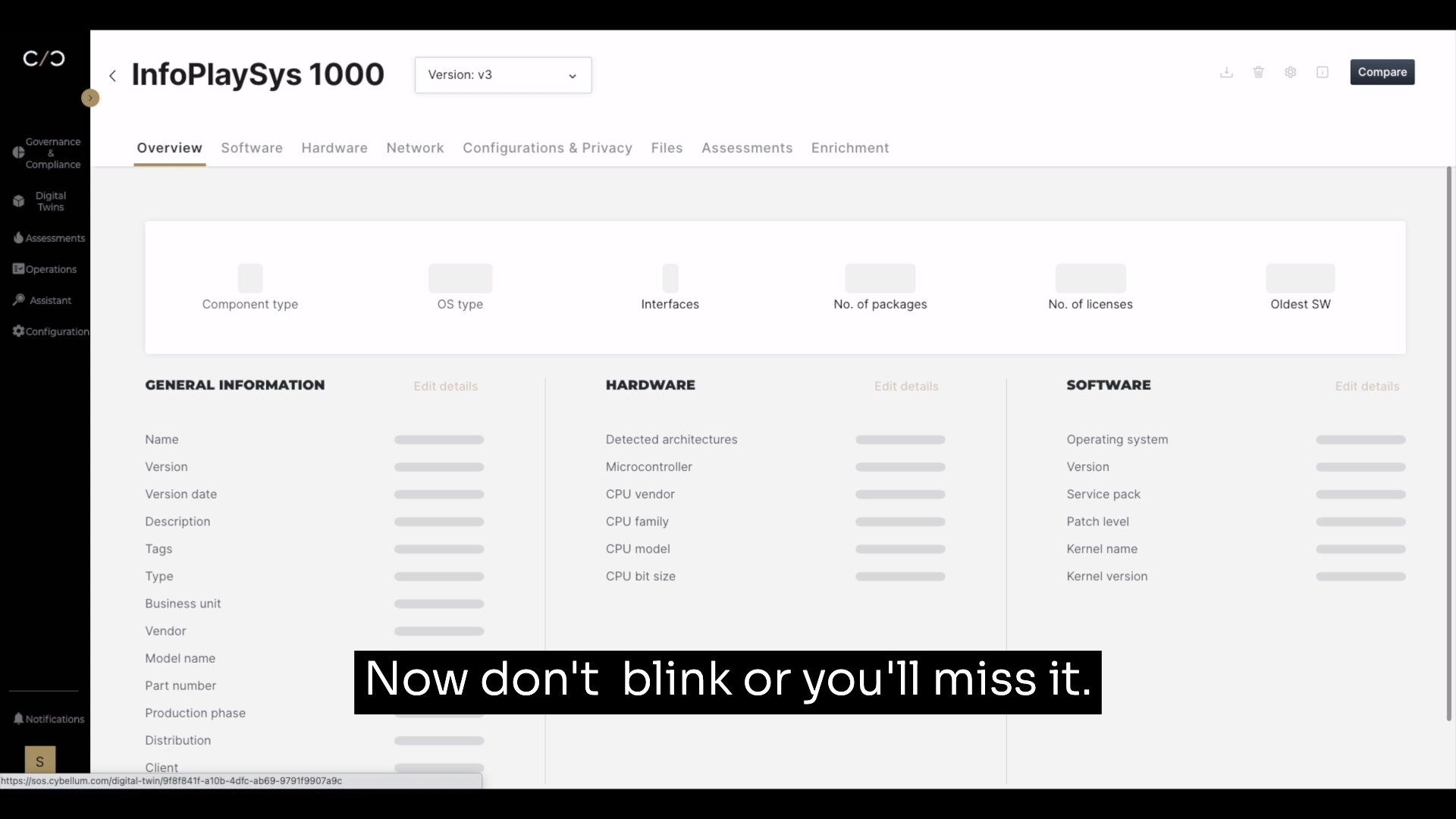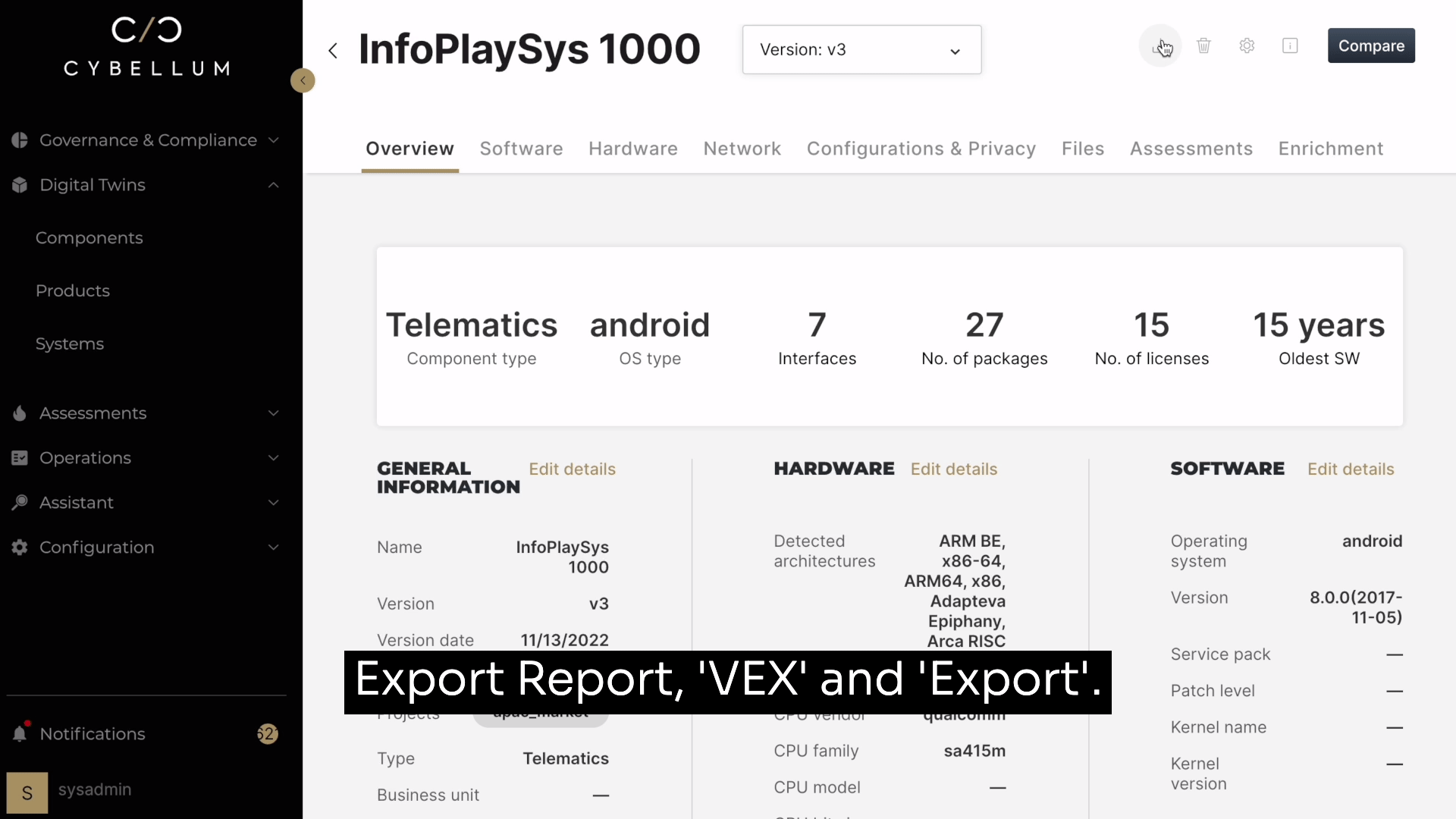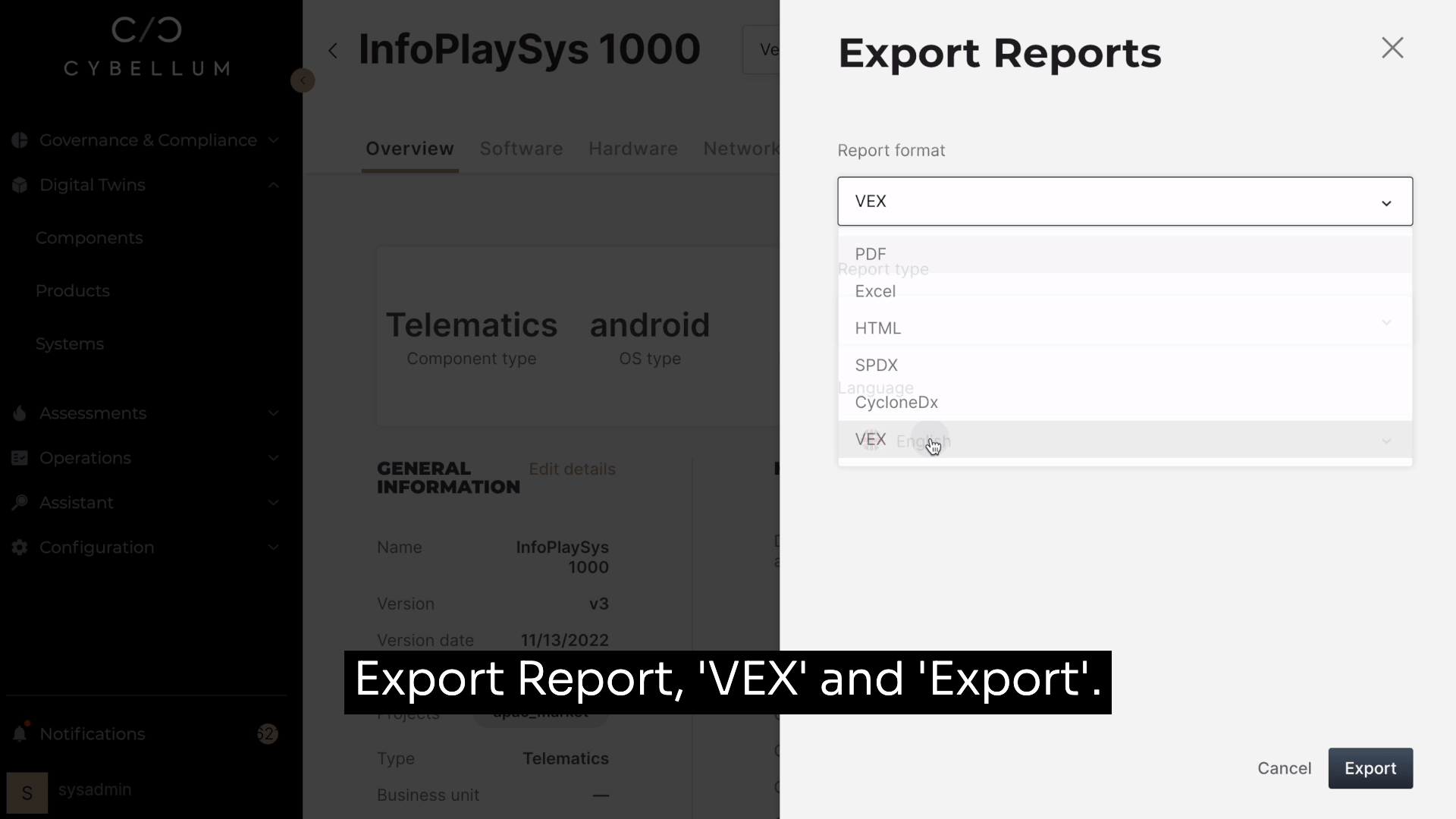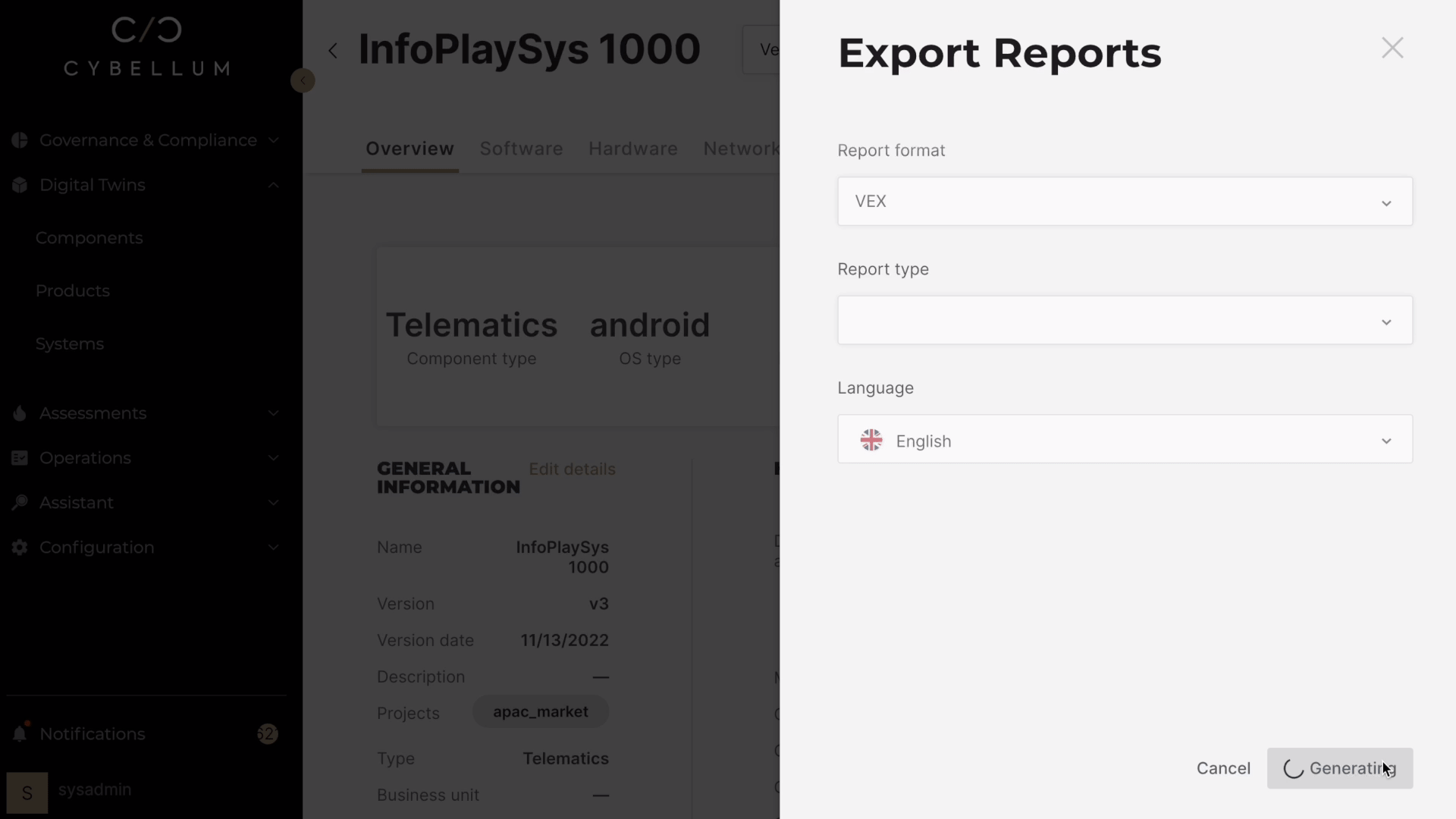
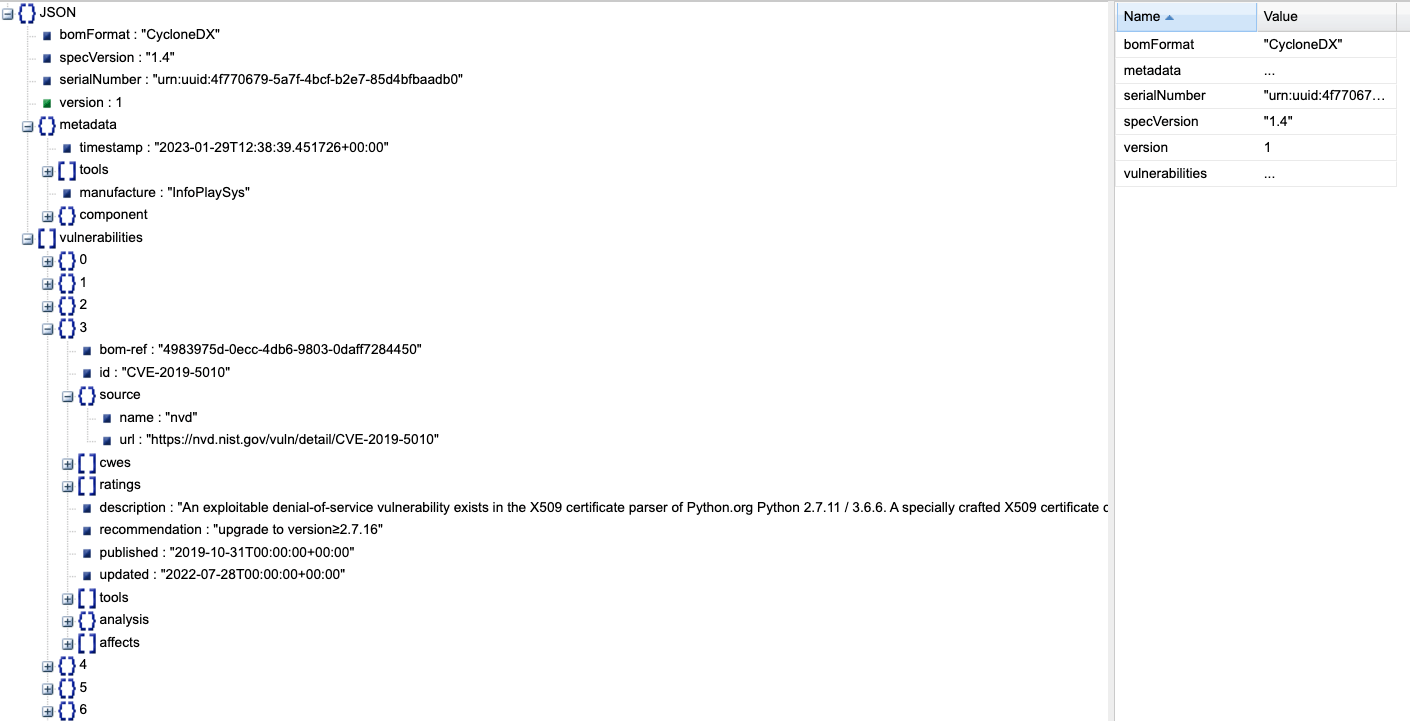
This automatically generates a JSON file that breaks down critical insights based on version, file type, publisher, and more. Now teams can rely on the most relevant exploitation information so they can address vulnerabilities at scale.
Protect with confidence
When an incident occurs, it is easy to distinguish between teams that focused their peacetime efforts on proper documentation and those that were caught off-guard. By leveraging the power of VEX through vulnerability prioritization, vulnerability management, and PSIRT activities, companies can better secure their products– even after being deployed to the field.
During a time when product security is a matter of life or death for customers, being on top of vulnerabilities is not only a good opportunity to boost brand reputation as having customers top of mind, it’s a reminder of the responsibility we hold to business operations and end users alike.