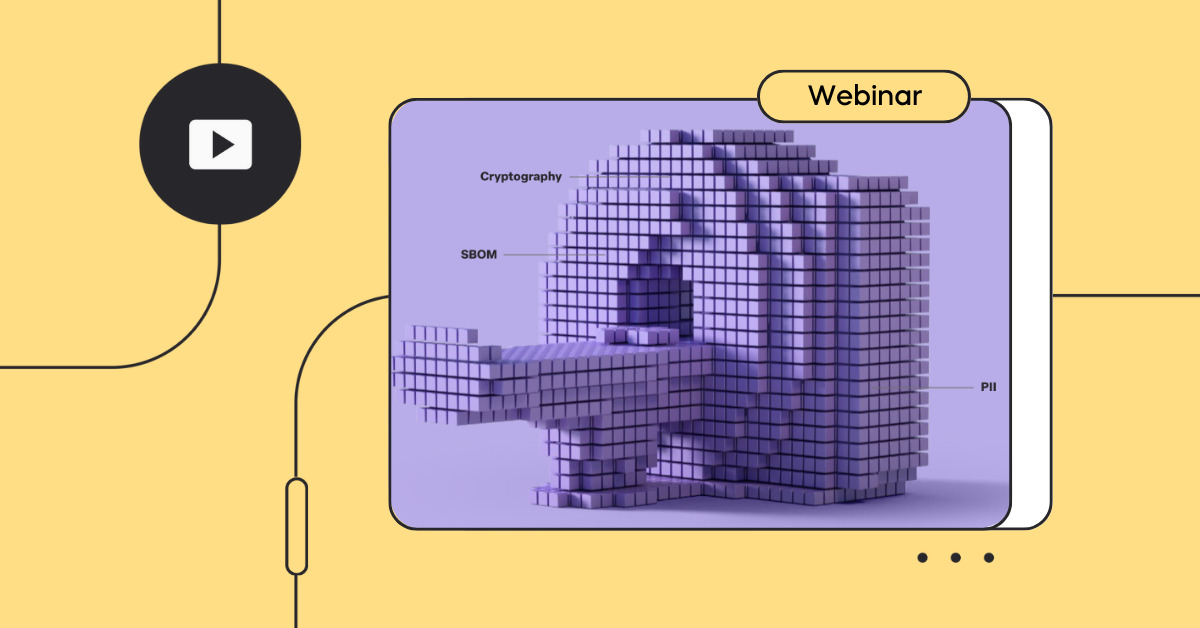
SBOM & Asset Management
Create & manage reliable, complete SBOMs and assets by merging, de-duplicating, auto-fixing, approving, and managing product SBOMs across components and business units.
SBOM & asset management
designed for connected products
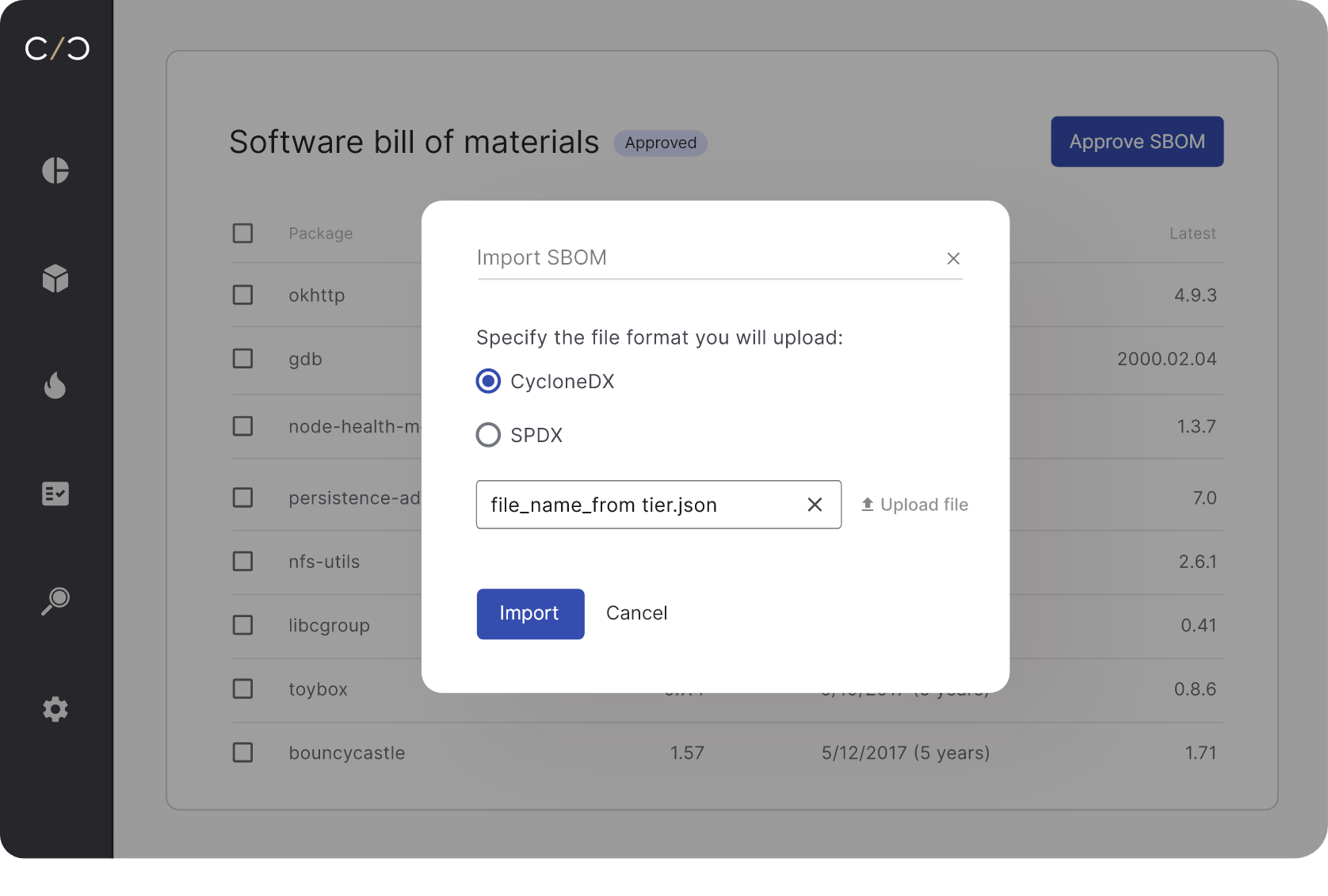
Merge & create SBOMs from multiple sources
Create reliable and complete assets & SBOMs by combining data from binary scanners, source code and external SBOM sources in SPDX, CycloneDX or CPEs CSV formats. Create high quality SBOMs that span open-source, commercial and proprietary software, and deduplicate identical packages
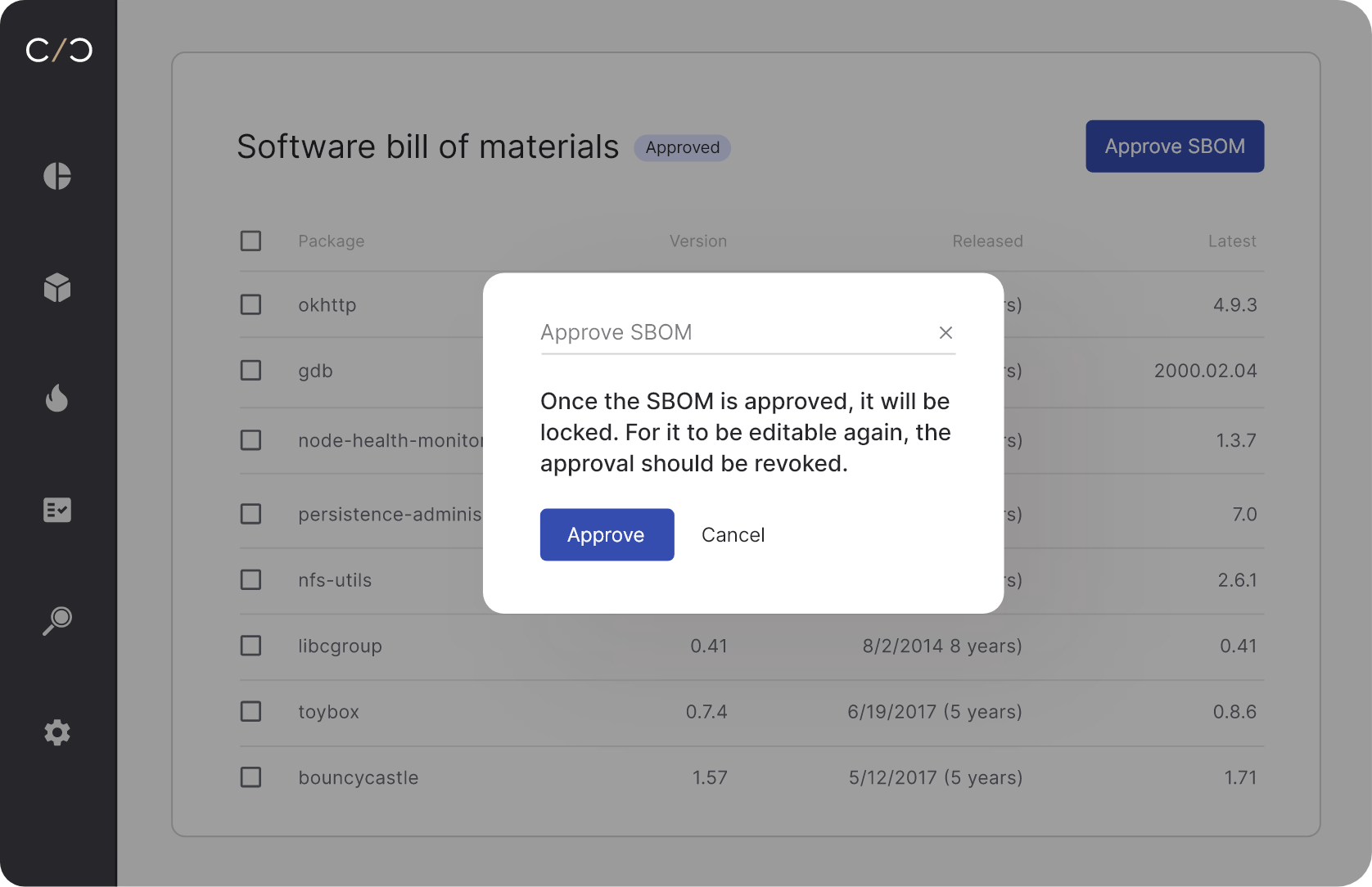
Validate, approve and collaborate
Auto-fix, validate, and approve SBOMs for any product, version or branch, then generate reports and share accurate, complete and reliable SPDX and CycloneDX SBOMs with internal and external stakeholders.
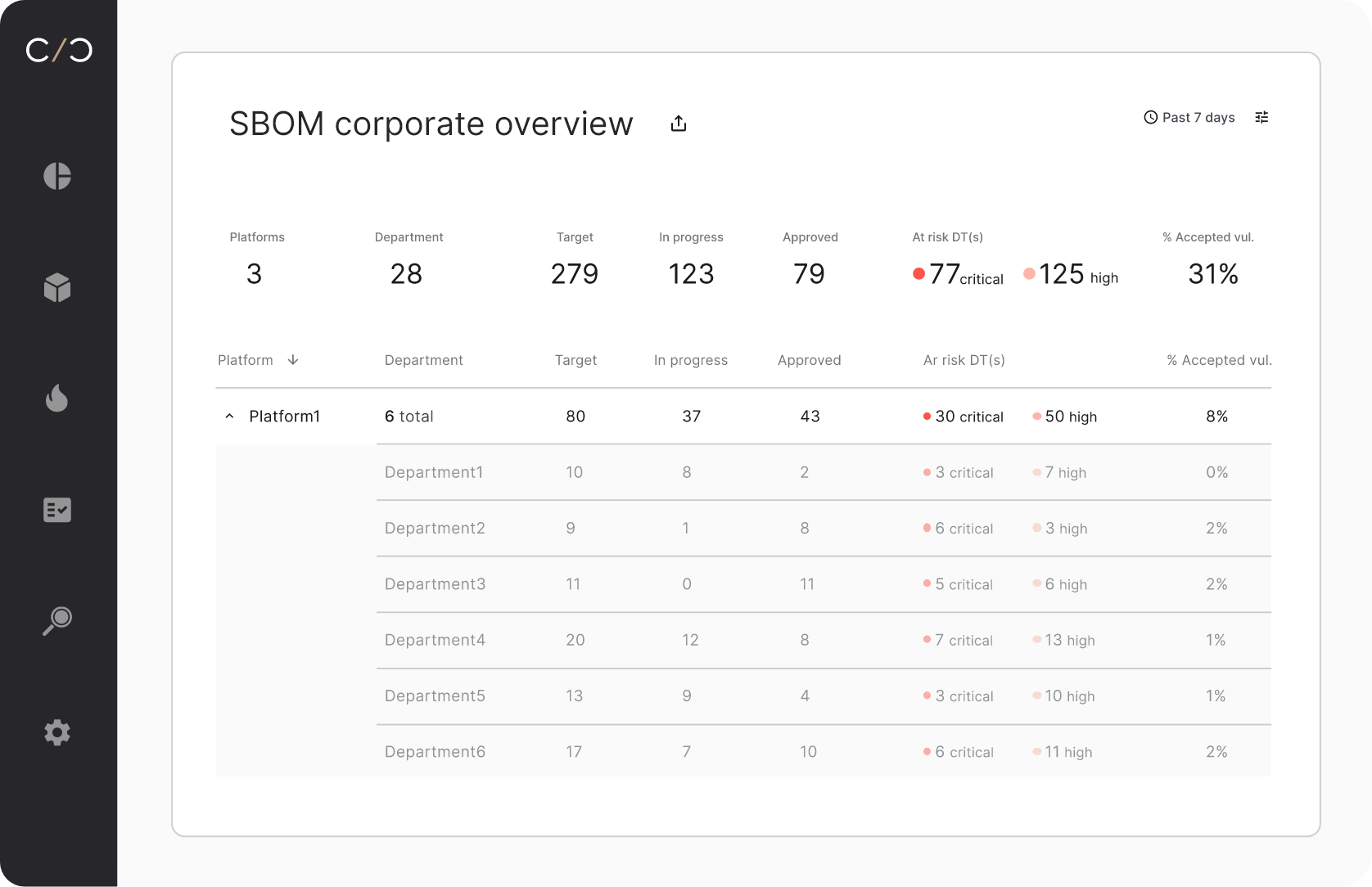
SBOM management across products and teams
View a complete product SBOM conveniently, uncovering exactly which components it includes, and get a high level view of your entire SBOM creation and validation process, to track the progress across teams and business units.
The SBOM & asset workflow,
perfected.
Scale SBOM & asset management
Automate the entire SBOM process from merging different sources, to fixing, and approval, for every version or branch.
Collaborate
easily
Track the entire SBOM management process across your organization, and share complete, reliable SBOMs.
Speed up
mitigation
Create VEX reports, analyze vulnerabilities, and get mitigation recommendations.

This platform is way more comprehensive than anything I’ve seen available on the market
Director of Product Security, Medical Device Cybersecurity Advisor