The National Institute of Standards and Technology (NIST) published an updated guidance on managing supply chain cybersecurity risks on May 5th 2022, titled “Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations” (C-SCRM), for organizations that are acquirers and end users of products, software and services.
The update includes a detailed list of C-SCRM security controls, a risk exposure framework – including example scenarios, C-SCRM templates, and more.
Over the past few years, the software supply chain has become an attractive attack target for hackers, as companies rely on an increasingly high number of third-party and open source software components to build their products. Attacks like the SolarWinds hack, that affected major US government agencies, 425 of the US Fortune500 companies, and other organizations across Europe, Asia and the Middle-East, and the more recent Log4J vulnerability, that put hundreds of millions of devices at risk, have justifiably brought supply chain security to the forefront of product security teams’ efforts to manage cybersecurity risks.
The guidance is part of NIST’s ongoing efforts to help organizations enhance cybersecurity through multiple initiatives related to the security and integrity of the software supply chain following two draft versions, and the US Executive Order 14028 on improving cybersecurity, issued May 17, 2021.
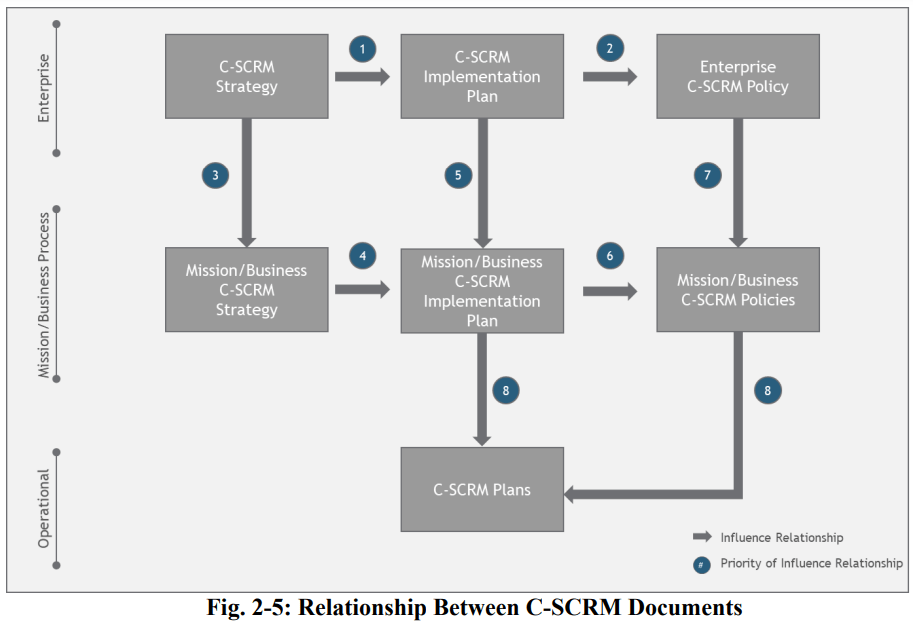
Fig. 2-5: Relationship Between C-SCRM Documents. From: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-161r1.pdf
NIST’s Jon Boyens, one of the publication’s authors, stated: “Managing the cybersecurity of the supply chain is a need that is here to stay. If your agency or organization hasn’t started on it, this is a comprehensive tool that can take you from crawl to walk to run, and it can help you do so immediately.”
The updated guidance aims at helping organizations address several vulnerable aspects of the supply chain, and provides recommendations for integrating supply chain risk management throughout the entire process – from acquisition to risk monitoring. “A manufacturer might experience a supply disruption for critical manufacturing components due to a ransomware attack at one of its suppliers, or a retail chain might experience a data breach because the company that maintains its air conditioning systems has access to the store’s data sharing portal,” Boyens said.
The revised publication provides teams with the practices they need to manage cybersecurity risks throughout their supply chains, with detailed guidelines for identifying, assessing, and responding to supply chain cybersecurity risks at all levels of an organization.
The guidance offers specific recommendations for a number of teams involved in managing supply chain cybersecurity, including cybersecurity specialists and risk managers to systems engineers and procurement officials.
“It has to do with trust and confidence,” said NIST’s Angela Smith, an information security specialist and another of the document’s writers. “Organizations need to have greater assurance that what they are purchasing and using is trustworthy. This new guidance can help you understand what risks to look for and what actions to consider taking in response.”




