INDUSTRIAL DEVICE SECURITY
Get reliable, secure industrial equipment to market
Manage SBOMs and vulnerabilities for industrial manufacturing equipment during design, development and post production, preventing costly downtimes and safety risks

OT networks may be secure, but what about the devices within them?
Product security is becoming one of the biggest challenges for industrial equipment manufacturers - SBOM blind spots, new vulnerabilities, and supply chain risks threaten to cause downtimes and business issues that we simply can’t afford. But with competing priorities and limited resources, how can we manage cybersecurity and privacy risks continuously, and adhere to multiple regulatory requirements, across all our products and devices?
The Product Security Platform
Continuous product security for
industrial manufacturing equipment
Manage SBOMs across teams
Create, merge, auto-fix, edit and approve SBOMs for all products versions and branches, and manage the entire SBOM process across multiple business units
Identify the most relevant vulnerabilities
Assess vulnerabilities in the context of your products, automatically filtering irrelevant, non-exploitable ones, and getting detailed mitigation recommendations
Continuously monitor for cyber risks
Understand exactly which products are affected by a new vulnerability, and conduct detailed investigations, accelerating pre and post market cybersecurity

Cybellum’s platform allows the team to detect and mitigate risks early and often

Cybellum is solving many of the problems we identified in our CISA & SBOM working groups
Director of Product Security, Medical Device Cybersecurity Advisor


Cybellum’s services and platform has helped us produce a comprehensive Cyber Security Management System
Cybersecurity Analyst Team Leader
Industrial product security, simplified.
Manage risk across BUs and product lines
Quickly identify the most critical issues across all your products and teams, from security issues to compliance gaps and supply chain risks
Prevent downtimes & security issues
Increase uptime by identifying and mitigating security risks continuously, speeding up security investigations and getting clear mitigation reccomendations
Secure across the entire lifecycle
Detect and mitigate vulnerabilities, coding weaknesses and malware from design to post market, manage SBOMs, and analyze Threat Models, all from one place
What makes it all possible
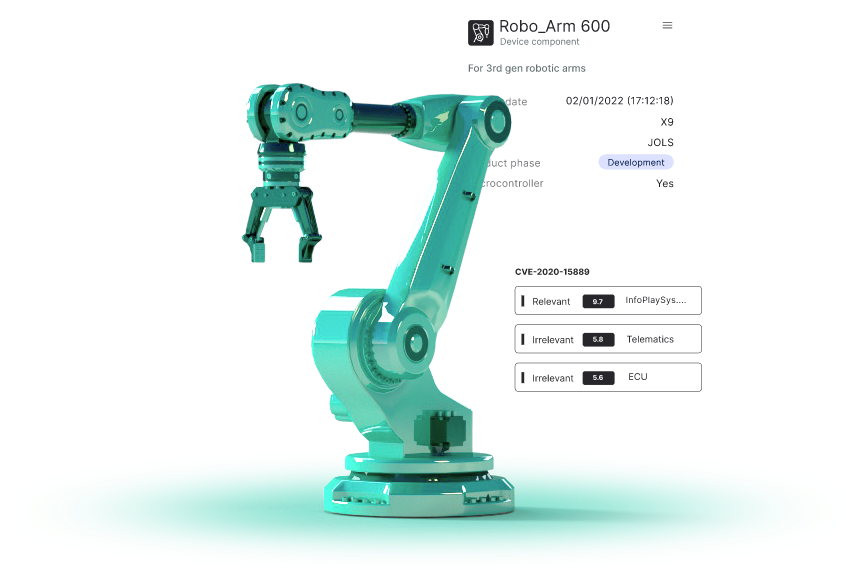
Cyber Digital Twins™ technology creates exact digital replicas of your device’s software, allowing you to analyze, detect and manage cyber risks in incredible detail, from a single component level, all the way to a full product system
I have to see this