The SolarWinds hack of 2020 allowed attackers to dig deep into many major businesses and government agencies. This high-profile attack called into question supply chain security, and the implicit trust enterprises place in suppliers of software and devices.
This post explores the challenges of protecting the supply chain, and how the new Vulnerability Exploitability Exchange (VEX) developed by the NTIA as a companion artifact to the Software Bill of Materials (SBOM) can help organizations tackle it.
Improving Supply Chain Security
In response to the SolarWinds attack, President Biden issued Executive Order 14028 to help improve national Cybersecurity with a special focus on addressing the challenges of software supply chain risks. Section 4 of the cybersecurity executive order mandates that organizations provide a Software Bill of Materials (SBOM) for products, detailing what software components are used in a product’s creation.
The executive order directed the Department of Commerce and the National Telecommunication and Information Administration (NTIA) to publish the minimum elements for a Software Bill of Materials. The resulting NTIA SBOM guidelines are considered the minimum set of data that an SBOM artifact should include. Unfortunately, standardization in what is included does not create standardization for how it is stored. Multiple formats have arisen, such as CycloneDX and SPDX, which have made it more challenging for organizations attempting to ingest and correlate across different suppliers instead of simplifying the process.
Looking into SBOM Security
Every component added to a product has the potential to bring inherent vulnerabilities into that product. Knowing when this happens and whether it affects the final product is challenging. It requires an in-depth understanding of the components making up the product or software. It includes maintaining a program to monitor the incorporated components for new vulnerabilities and investigating the impact of any discovered.
Manually maintaining such a comprehensive record is a time-consuming process. Any given product can have hundreds or even thousands of components used in various capacities. So even if an individual part is known to have a vulnerability, determining the level of exploitability is tricky.
Enter VEX.
What is VEX?
While SBOMs are useful for helping organizations understand potential risks from third-party software components incorporated into a product, it does not grant insight into the actual exposure. To deal with this, the NTIA has proposed a Vulnerability Exploitability eXchange (VEX), which is a companion artifact to an SBOM. It allows device manufacturers to communicate the exploitability of a vulnerability discovered in one of its software components listed in an SBOM. This saves organizations from the need to work backward to determine if a vulnerability for a product listed in an SBOM affects them.
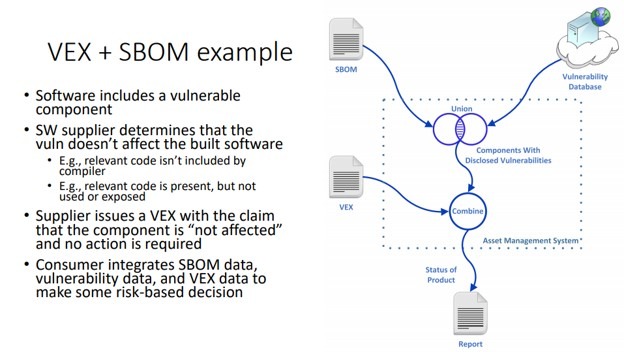
Figure 1: How VEX augments existing supply chain vulnerability assessment (source)
Dealing With a VEX’ing Problem
Using VEX allows OEMs to assess whether or not components they are using in their product with vulnerabilities are exploitable in the end product. Several factors might prevent a vulnerability from being exploited, such as:
- The final code may not actually execute any part of the library with the vulnerability
- Conditional compile statements have excluded the vulnerability from the final executable
- Current security controls prevent the vulnerability from being executed
In the above cases, despite a vulnerability existing in a component, it does not result in a vulnerability in the final product. This is an essential and time-saving piece of knowledge for developers. When this is the case, the vulnerability does not need to be further remediated; thus, no additional development time is wasted creating an unnecessary fix.
Not Just for Suppliers
VEX is also helpful for asset owners that wish to verify the security of devices that vendors provide. In the past, it was complicated to discern what software components were used on a given device. It was almost impossible for an asset owner to know without the manufacturer telling them that the device is vulnerable to attack.
This was the case on many devices using the Treck TCP/IP stack. A Zero-Day vulnerability known as Ripple20 was discovered in the Treck library. This library was already deeply embedded in many devices.
Having a system such as VEX, product owners could have quickly learned that their systems were vulnerable, allowing them to take steps to mitigate it. This is especially important for industries such as Utilities, Medicine, and Government Agencies that are already major targets for malicious actors.
Being able to identify and remediate vulnerabilities quickly can make all the difference whether they become compromised.
Context is King
VEX is conceptually similar to a context-based analysis system for determining if components of a digital system are vulnerable.
Advanced context-based analysis goes further in reducing the supply chain risk than VEX by incorporating the underlying hardware architecture, OS configurations, encryption mechanisms, keys, hardening mechanisms, full control flow, and API calls that are used. This allows for a more in-depth and accurate analysis of a given product.
Protecting the supply chain for development is an important factor in developing more secure products. Knowing what components are utilized is not enough. Instead, in-depth analysis is required to identify the vulnerabilities and determine their applicability.
VEX may not provide as in-depth an assessment as the context-based analysis; it is still helpful for defending against supply chain attacks. Using automated tools such as VEX combined with SBOM and context-aware vulnerability analysis is necessary to manage supply chain vulnerabilities efficiently.
Cybellum, a leader in context-aware analysis, can help shine a light on your software supply chain to protect your customers and your business. Discover how you can see all your software assets, understand each vulnerability’s real impact, and mitigate security risks before they cause any harm. Talk to us today!




