As connected products and devices become increasingly software reliant, and the cyber threat landscape continues to evolve, manual and one-off security testing for devices is no longer an option. Today’s security standards and regulation demand product security teams address compliance and security throughout the entire product lifecycle – from design and development till devices’ end-of-life.
This requires adopting a holistic approach, and the processes and technology that support the types of risks connected devices are vulnerable to today.
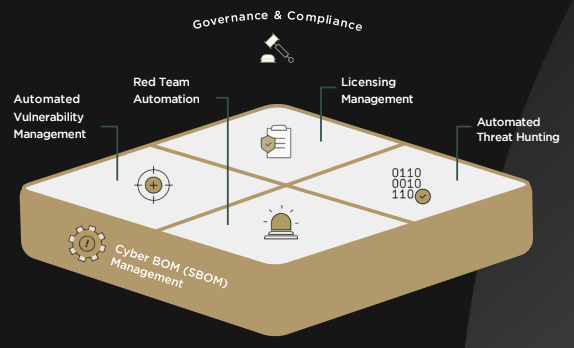
We’ve put together a quick a rundown of the six ways that Cybellum’s Product Security Platform works. Our Cyber Digital Twins™ technology continuously detects, manages, mitigates, and prevents software vulnerabilities and compliance risks across your product portfolio so they stay secure and compliant every step of the way.
Cyber Digital Twins™
Cybellum’s unique Cyber Digital Twins™ technology creates a precise replica of every firmware and software component in your entire product portfolio as you design, develop, deploy, and update in the field.
You can run all your latest cybersecurity and compliance testing against the up-to-date digital replica to assess every product’s security posture with certainty, from from a single firmware component to a full product system – including inter-system architecture, external connections, and available countermeasures.
#1 SBOM (Cyber BOM) Management
Get an automatically updated SBOM of your entire product portfolio anytime you need it to extend inventory visibility from SBOM to product ID including all associated risks. You can view all the characteristics of product firmware and software to create a complete SBOM, including:
- License details for your and 3rd party components, commercial, and open source
- Hardware architecture
- Operating systems
- Configurations
- Control flows
- APIs
- Build
- Usage
- and more
#2 Governance and Compliance Management
Achieve a high standard of governance while you accelerate time-to-compliance. Cybellum provides you with regulatory reports including a full trail of evidence, enabling you to see changes to the status of vulnerabilities, user triage decisions, and more. The automatic process validates compliance with security regulations plus your own policies, including cryptography, coding, hardening, and PII protection.
#3 Automated Vulnerability Management
Quickly detect, prioritize, and mitigate known and zero-day vulnerabilities across your entire asset inventory. Cybellum’s contextual analysis of vulnerable components and automated policies eliminates false positives and reduces your alert count using binaries – no source code required!
#4 Red Team Automation
Cybellum is continuously on the lookout for zero-day threats. The combination of static detection and dynamic validation cuts down on false positives and prioritizes the most relevant results. You get an in-depth analysis of exploitable issues, including risk family and type, as well as actionable remediation and mitigation insights integrated with your ticketing system.
#5 License Management
Use of open source and 3rd party commercial software can expose your devices to legal risk. Cybellum helps you make sure that every 3rd party and open source component’s license is accounted for as it automates detection and validation of license compatibility with your licensing policies. You can rely on preset policies or configure your own free and open source software (FOSS) licensing rules.
#6 Automated Threat Hunting
With Cybellum on your team, you don’t have to wait for attacks; you can go on the offensive to safeguard your products. Cybellum’s proactive prevention uses aggregated threat intelligence to track new vulnerabilities in real time, matching them against your entire product portfolio to prevent incidents. It also delivers security analysis details and mitigation recommendations to your Incident Response Team, enabling them to zero-in quickly on the root cause of any incident.
Stay Secure and Compliant From Design to Post-production
Cybellum enables product and device manufacturers to keep the products they build secure and compliant for life, from design to post-production and beyond. Industry leaders use Cybellum’s platform to manage cyber risk and compliance continuously, throughout the entire product lifecycle. With Cybellum, manufacturers can ensure that their entire product portfolio is secure by design and that it stays that way.
Want to learn more about keeping connected devices secure for life? Schedule a demo to see how it works.