
Cyber
Digital Twins™
technology
Sitting at the core of the Product Security Platform, CDTs are digital replicas of your products’ firmware that allow for unprecedented visibility and control.
Book a DemoSitting at the core of the Product Security Platform, CDTs are digital replicas of your products’ firmware that allow for unprecedented visibility and control.
What are Cyber Digital Twins™?
CDTs are digital replicas of your product’s software that contain a wide variety of data required for cybersecurity analysis. They can be extracted from the binary files of any product or component and provide a rich data set that allows for ongoing cybersecurity and cyber-compliance. Here are some of the things uncovered in a component’s Cyber Digital Twin™:
How it Works
Uncover what’s hidden inside your product’s software
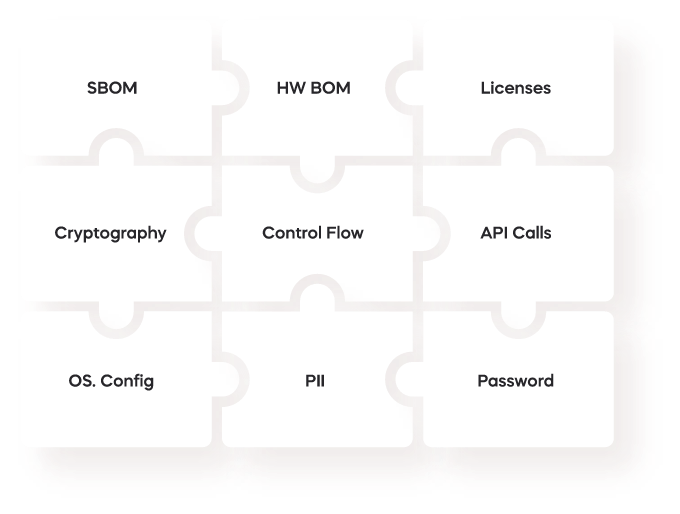
Automatically analyze the binaries of each product’s firmware to uncover their exact composition - from SBOM, to version history, licenses, HW architecture, OS configurations and more. No source code needed.
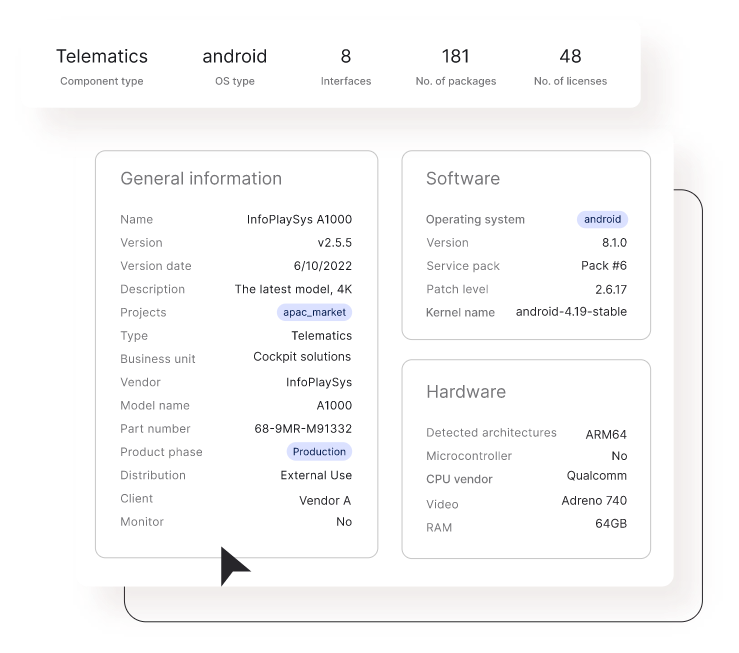
Assess security risks in the context of your products
Analyze your complete product system - from individual components to entire products. Send that data through our product vulnerability database to find a match for relevant vulnerabilities, zero days, regulatory compliance gaps, and more.
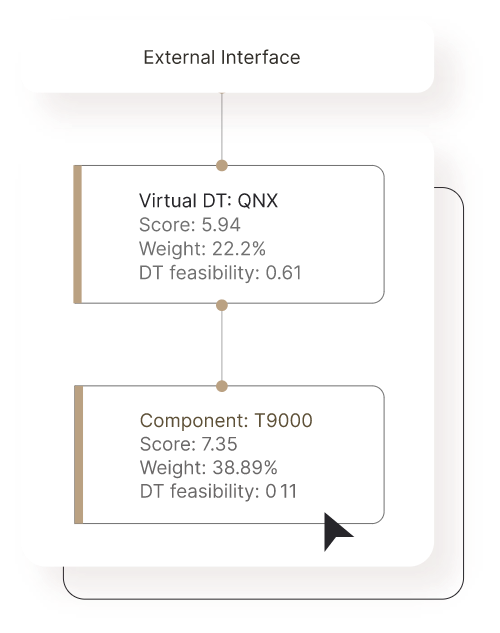
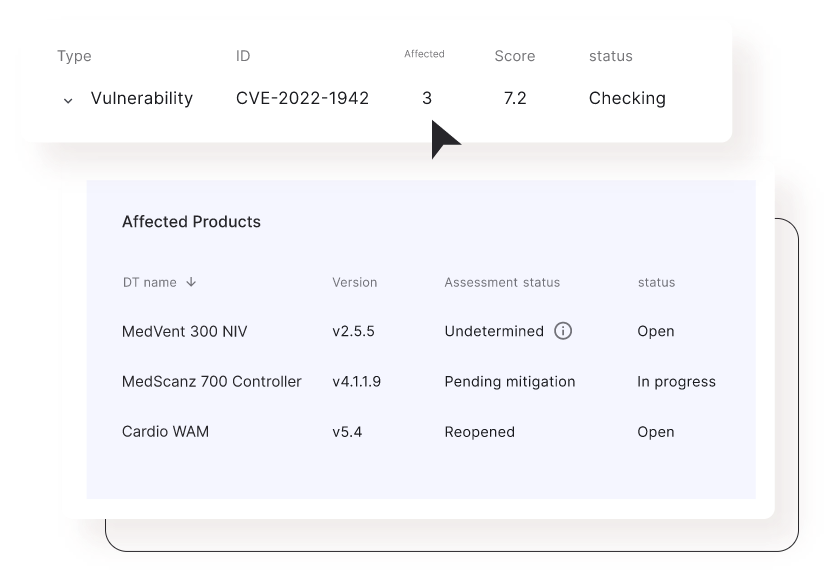
Manage and mitigate risks continuously
Detect new risks continuously, from development to post production, for each product. Then, get clear recommendations on how to quickly mitigate each risk.
What makes it so powerful
Built for connected
products
Analyze product systems as a whole and surface relevant risks in the context of your products.
Goes beyond
basic SBOMs
Uncover HW BOM, licenses, API calls, cryptography, OS configurations, and more.
Surfaces
supply chain risks
Get an independent view of supply chain risks identifying new risky suppliers and assessing existing ones.
What you can
do with Cyber Digital Twins™
Analyze product systems
Get a System of System view, including inter-system architectures and external connections, and uncover proprietary embedded frameworks such as AUTOSAR.
Maintain a software asset inventory
Track software versions, analyze cryptographic characteristics, and keep track of all product software and firmware characteristics, all from one place.
Validate policy requirements
Validate policy compliance using pre-mapped requirements from 50+ standards, regulations, and best practices, or create your own policies, including for OS hardening and exploit mitigation requirements.

