Assurance & Vulnerability Management
Manage risks and vulnerabilities in the context of your products, aggregate threat models, fuzz tests, pen tests and vulnerabilities into one unified risk data system, and use AI to triage accurately, allowing you to mitigate risks quickly and efficiently.
Product Assurance & Vulnerability Management
Your risk data system
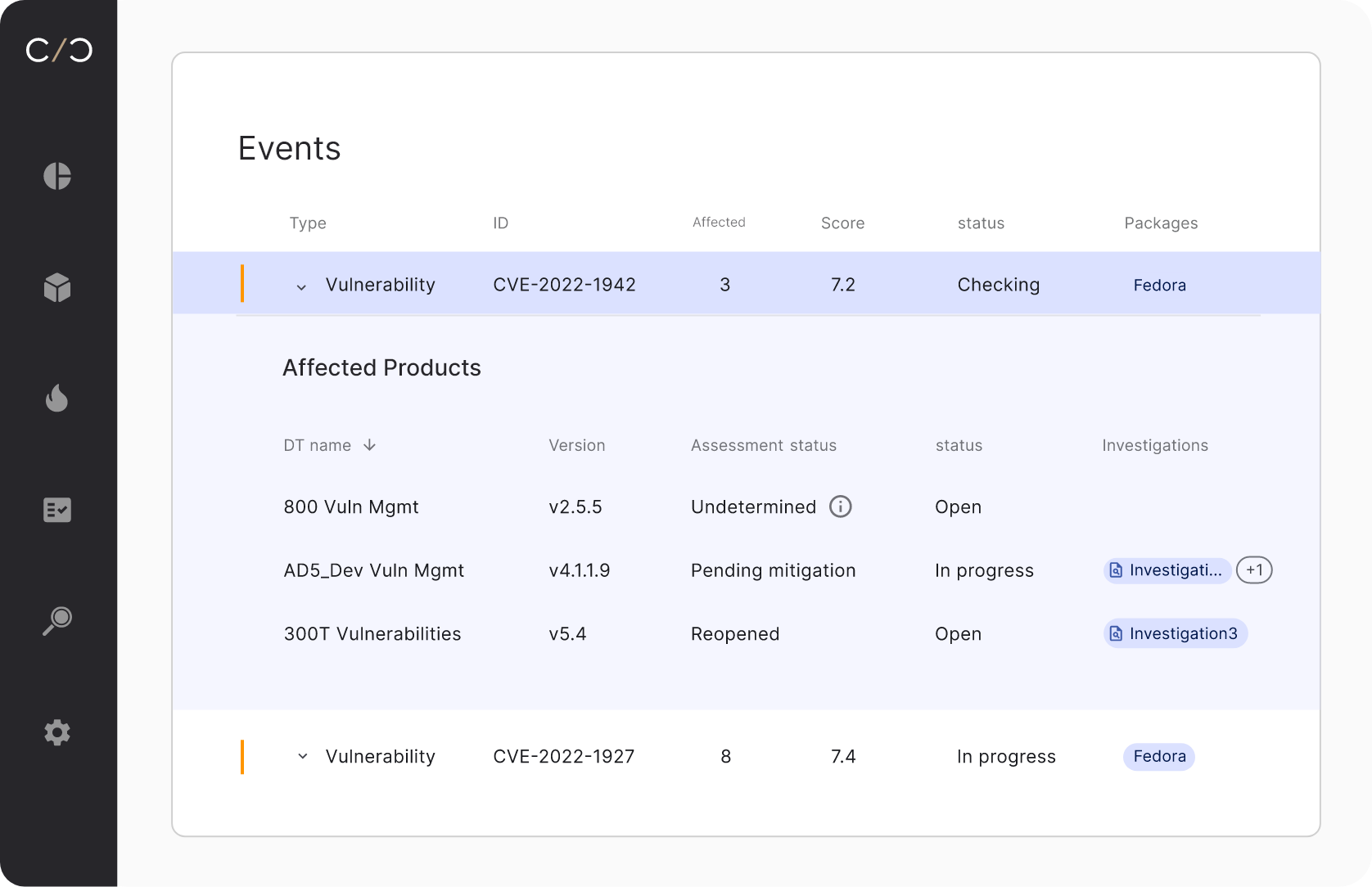
Manage a complete, multi dimensional picture of risk
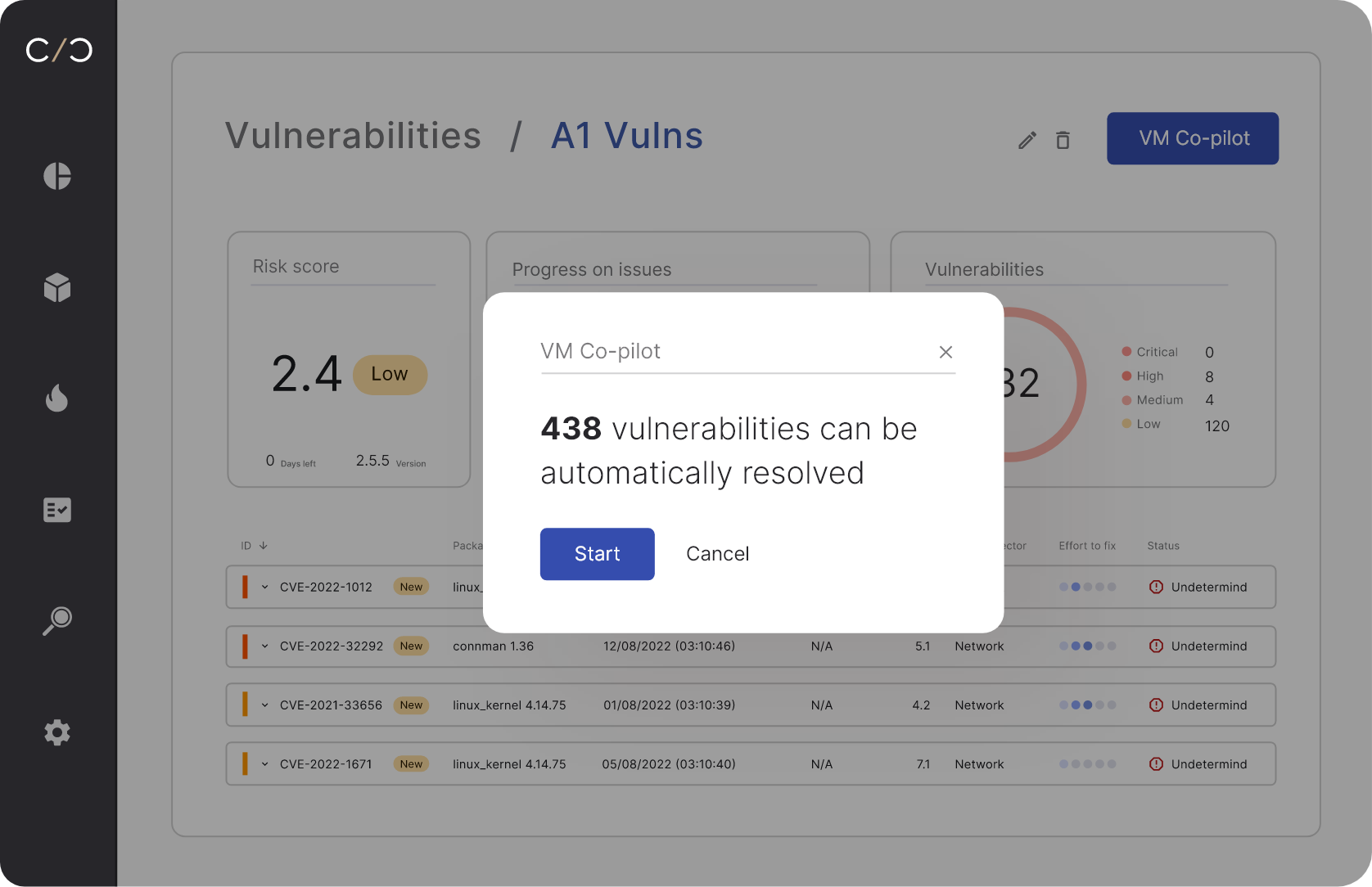
Match your SBOMs and asset data with our product vulnerability database which unifies intelligence feeds, EPSS scores, and research findings to identify risks, or use our built-in malware and coding weakness detection engines. Import Threat Models (TARA), fuzz tests and pen test results, then run everything through our triage assistant -- the VM Co-Pilot, to surface the most relevant, exploitable vulnerabilities and risks.
Analyze & get mitigation recommendations
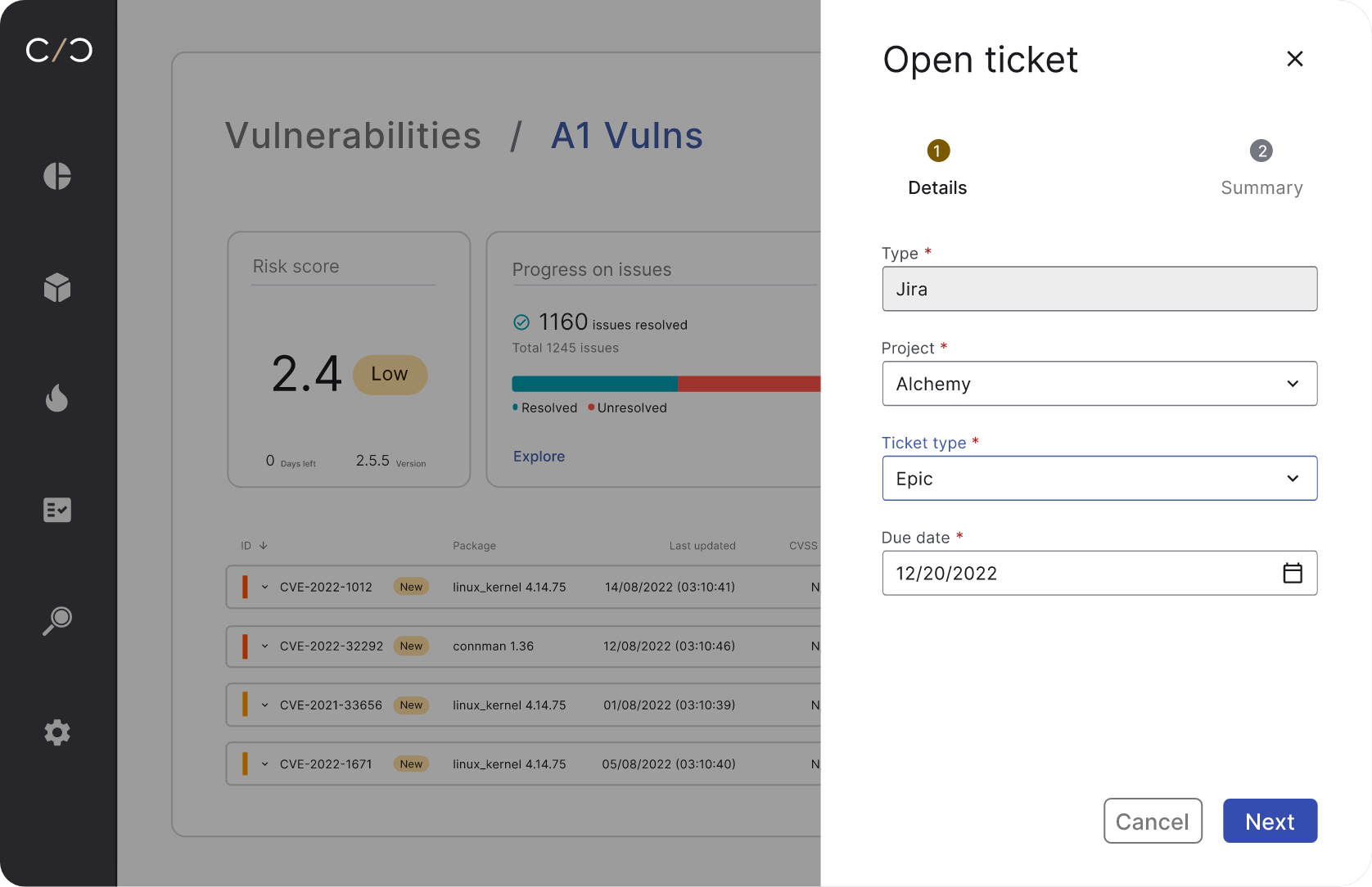
Conduct a detailed risk analysis including revision management and scenario exploration. Understand exactly how to fix each vulnerability using our Ask Roman AI and share those insights with your colleagues, speeding up mitigation.
Monitor risks continuously
Automatically monitor and analyze vulnerabilities in new software updates, product versions and branches in post production devices.
Assurance & vulnerability management,
unified.
Cancel out the noise
Focus on the risks that matter most, radically speeding up mitigation.
Close the loop
Go from detection to management and mitigation, with full traceability, all in one place.
Comply more easily
Meet cybersecurity standards and regulations from ISO, the FDA and others.

Cybellum’s platform allows the team to detect and mitigate risks early and often