Software Supply Chain Security
Gain visibility into software supply chain risks, manage SBOMs and mitigate vulnerabilities, with a dedicated security solution built for device manufacturers
Product Software Supply Chain Security
Unchain your
supply chain
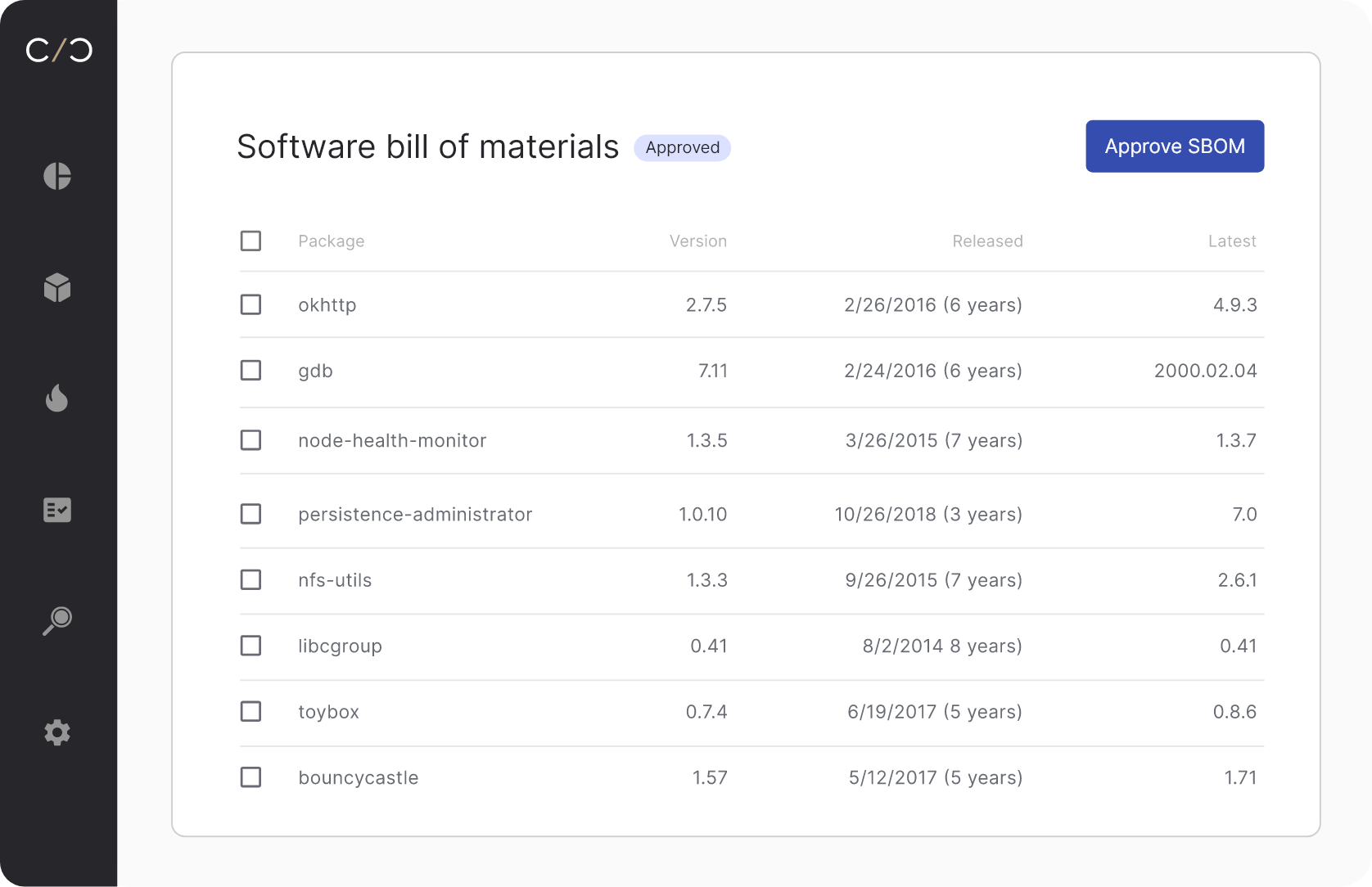

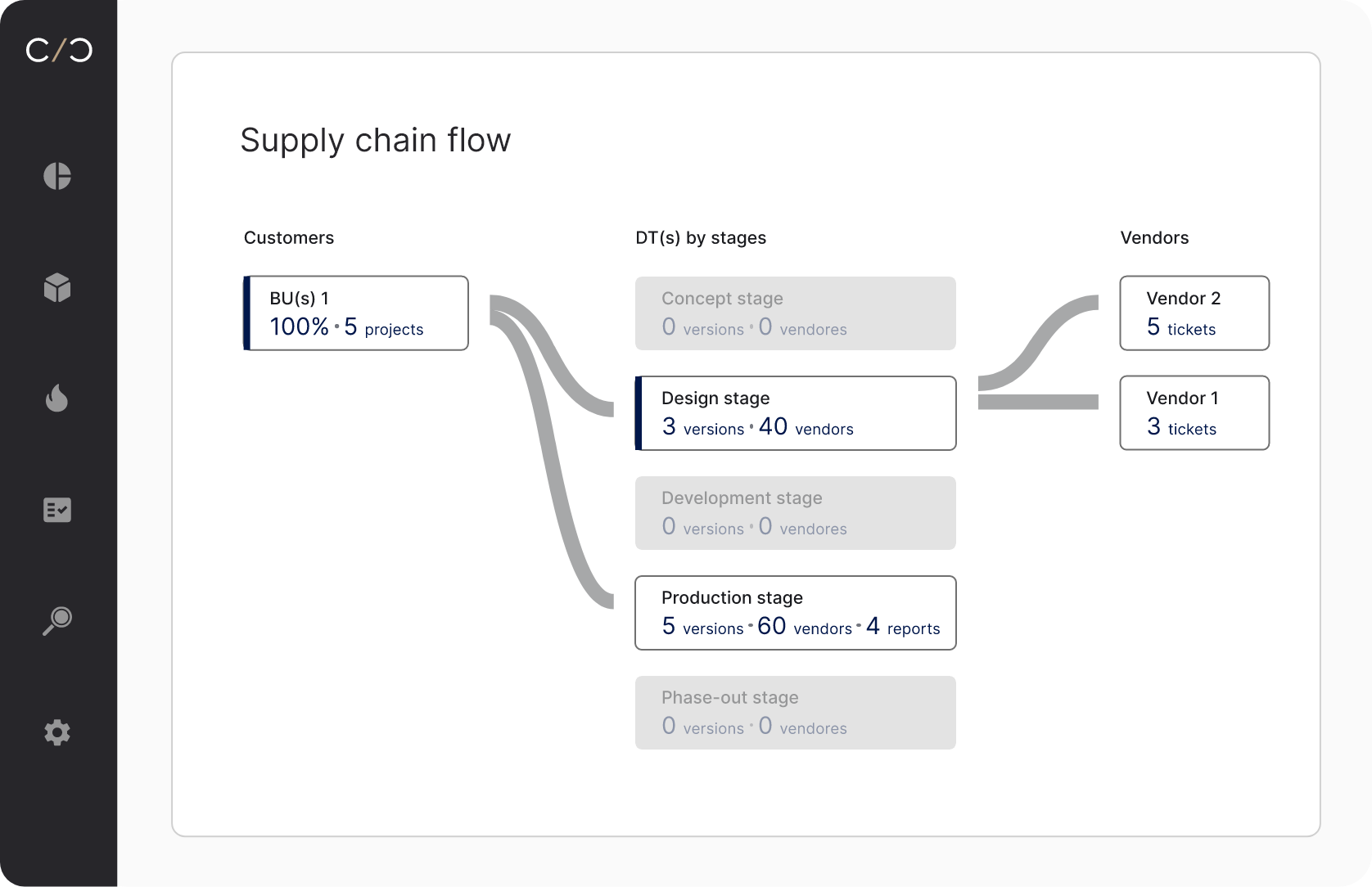
Manage SBOMs and VEXs
Orchestrate the entire SBOM and VEX process, from creation to approval, across business units, products and supply chain tiers
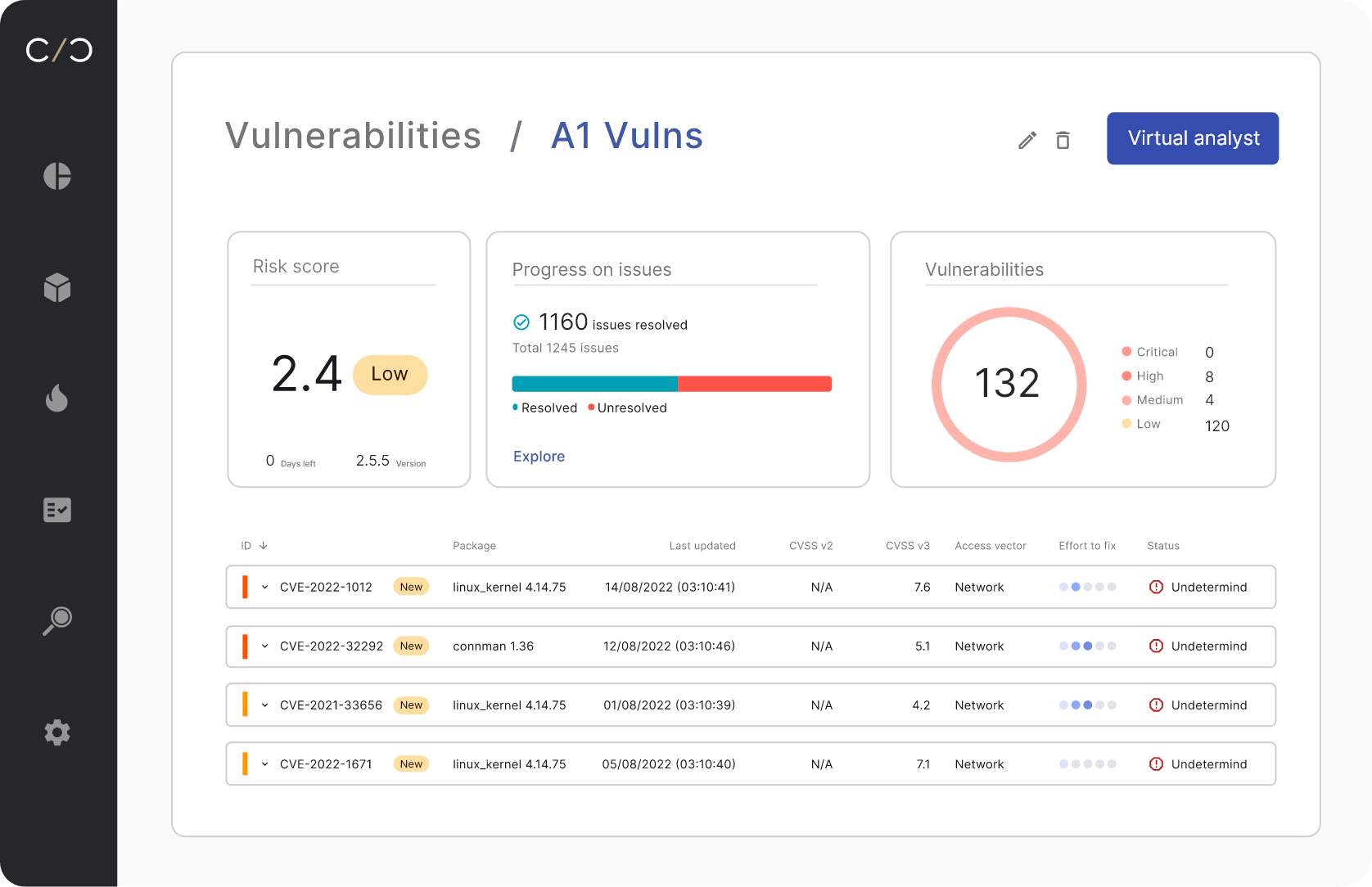
Mitigate vulnerabilities
Identify risky components across the entire supply chain, get mitigation recommendations and track remediation
Identify risky suppliers
See exactly which suppliers pose the most risk, or take the longest to remediate, and easily share the findings
See, control, comply
Stay
compliant
Comply with FDA, ISO and EU supply chain regulations
Become independent
Get a reliable, independent view of supply chain risks
Mitigate security risks
Identify risky components and mitigate, all automatically

Cybellum’s platform allows the team to detect and mitigate risks early and often