Future proofing can feel a bit like Marty Mcfly’s first journey to the future. It’s fast paced and overwhelming.
This is somewhat similar for Medical Device Manufacturers (MDM) and automotive manufacturers who are navigating the ever evolving world of cybersecurity to support their software-driven approach. As both industries work hard to implement proper cybersecurity measures, the FDA, IMDRF, UNECE, and other organizations have signaled to MDMs and OEMs that it’s time to protect against any vulnerabilities from both today and whatever transpires in the future.
Organizations are still ironing out the processes for embedding cybersecurity into their development and management processes. Ultimately, it’s on the product manufacturer to ensure that all third-party and open source code within the device is constantly up to date, even if they didn’t develop it. That’s why new tools and frameworks, such as software bill of materials (SBOM), can help companies shift right and future-proof their products as they set the foundation for long-term protection.
These industries, just like other sectors, are discovering that shifting right cybersecurity may be exactly what they need.
Why post-production security is a whole new ballgame
There is no way for us to know what will happen in the future but that means efforts need to be doubled to secure the code within our devices today. As industries come to this realization, emerging standards and regulations are requiring companies to put processes in place that continuously monitor, mitigate, and secure devices far after they’ve left the production facility.
Devices today are more reliant on software than ever before. In addition, software code is not static. Like we’ve seen with our phones and computers, software is continuously changing based on updates, patches, authorizations, and other factors.
From a security standpoint, each device demands the latest version with the best mitigations regardless if it is a phone, computer, medical device, or vehicle. This can be achieved through manufacturer-pushed remote software updates, even after being released to users. That poses a challenge for end-users and fleet-management facilities who must track all device versions and match them to the latest recommended software version– something that industries are now automating to reduce expenses and bolster cybersecurity.
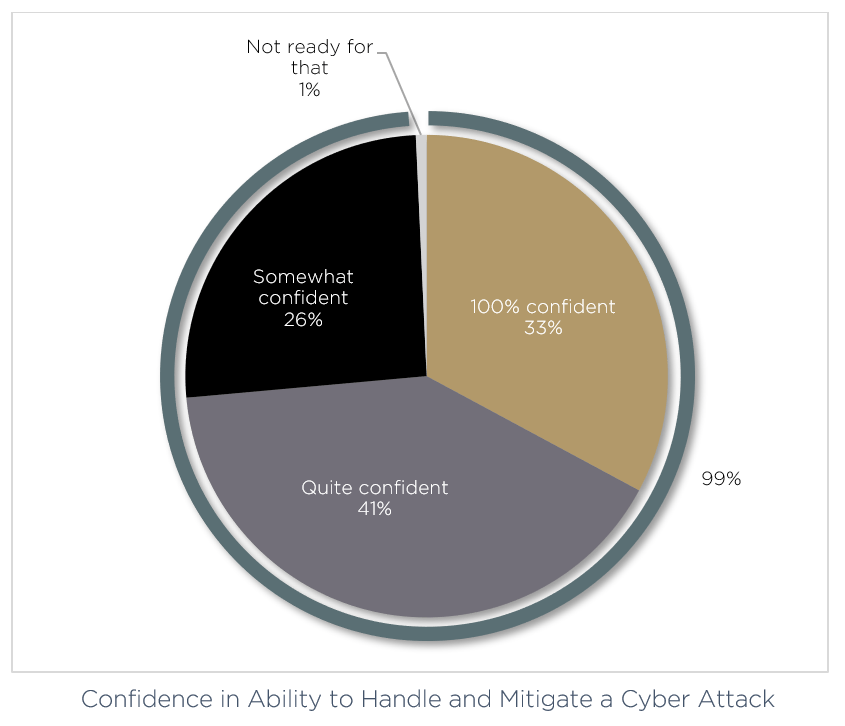
In our recent 2022 Medical Device Cybersecurity: Trends and Prediction, we surveyed 150 medical device professionals, including senior decision makers from the US, Germany, The Netherlands, Belgium, The UK, Switzerland, Japan, Mexico, France, South Korea and Canada. What we found was that while many felt confident in responding to a sudden cyber attack, 67% still of these professionals felt they needed to sharpen their cybersecurity processes when asked prying questions.
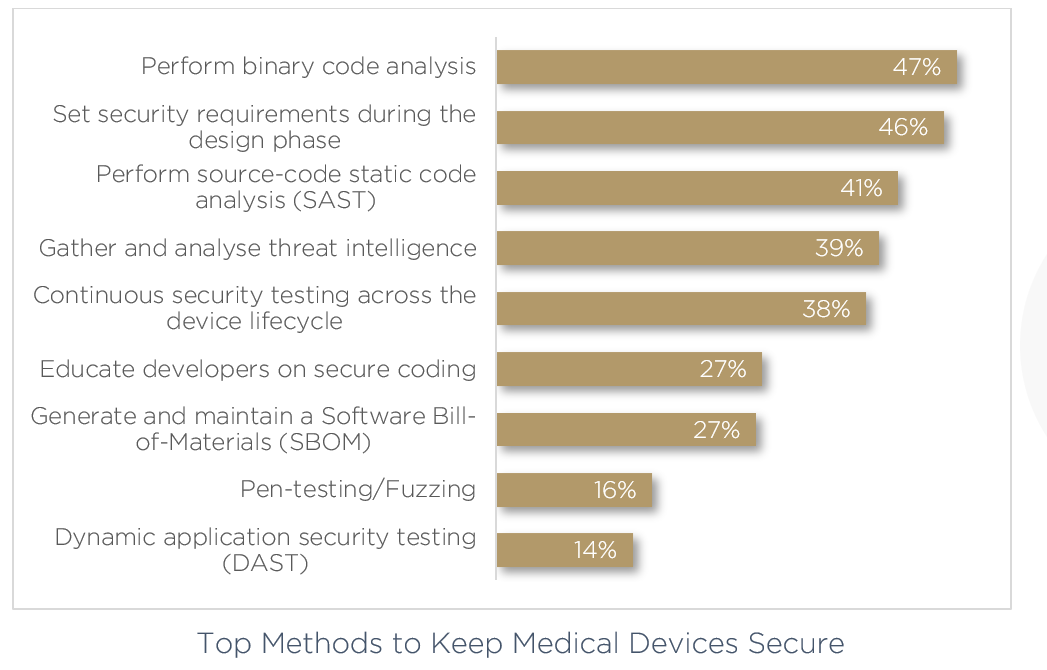
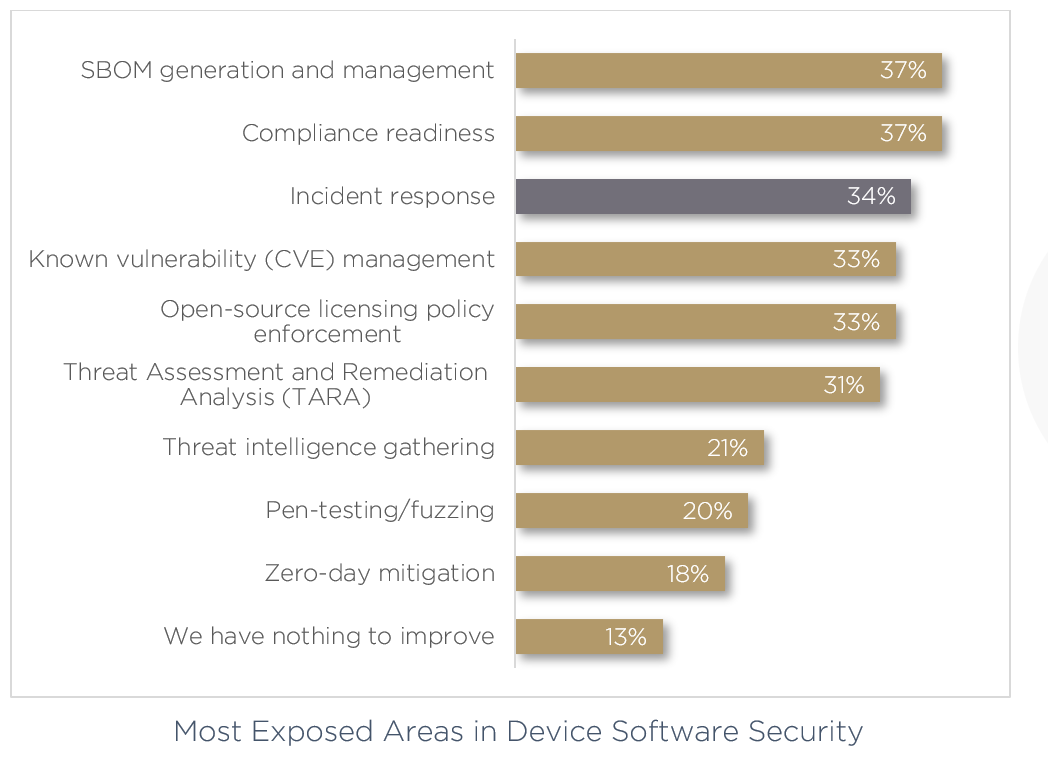
The most pressing issues surround methods for keeping devices secure. Here, more than one third believe their most exposed areas in device software security is incident response, worrying if an attack can even be remediated once identified.
Adding a layer of complexity to the mix, software defined vehicles and devices are designed to download and implement remote updates — also known as over the air (OTA) updates. Without thorough SBOM upkeep and predetermined cross-organizational incident response, companies risk facing catastrophic damage should a breach occur.
Shifting right, the right way
Shifting cybersecurity challenges right allows for companies to lay the foundation for addressing future vulnerabilities at a later time. It is critical not to confuse this with procrastination, but to see this as an opportunity for creating an ongoing culture of lifetime cybersecurity.
Before shifting right, the practice of adding certain tasks to later in the production process, companies have to get comfortable shifting left many of their cybersecurity procedures. One example is making documentation and testing components throughout the development process and using tools like threat modeling and TARA– not something to be considered just before final version submission.
Once early design and development stages have systems for cybersecurity management, including ongoing threat detection via automated vulnerability management, companies can begin understanding which steps can be taken later on in the lifecycle of the product.
In the past ‘shifting right’ referred to pushing a process closer to the end of the production process. Today, it applies to future proofing components that are already operating in the field. The connected nature of these components allows for a quality assurance infinity loop where best practices and mitigations are continuously monitored and updated all the way through the end of the product’s life.
Dealing with problems upfront and developing ongoing as well as post-deployment solutions early on in the production process is simply the best way to ensure earning the coveted FDA, CE, UNECE, and ISO/SAE approvals. Earning these certifications can take years, with production costs and attention to detail that would make big budget hollywood film producers blush. Shifting right the right way ensures that backend systems are in place to avoid recalls, prioritize consumer safety, and remotely secure products into the future.
Key tools to shift right
Modern technologies are assisting cybersecurity teams to future proof by providing deeper insight into what is occurring throughout the device. Examples of these are:
- Cyber Digital Twin- The Cyber Digital Twin was built to manage demands during development and later in the field later, after it’s in a customer’s possession. Organizations can use this shift right tool to construct a virtual representation of the product’s software.
The Cyber Digital Twin is critical in this role because each triggered alert must be triaged and understood by teams. - Smart Contextualization- Most alerts are nothing to be concerned about– but an industry that is struggling to fill their security gaps with qualified cybersecurity professionals can’t afford to be bogged down by false alarms. With contextualized real-time data a well equipped tool can build on a deep understanding of the underlying architecture and rapidly determine if the alert needs to be elevated to a live person.
- Workflows- These are amazing management systems that allow a company to understand existing vulnerabilities or how a new software version may impact the cybersecurity posture of a device. Relying on data from production engineers alongside the latest in-field data, software and hardware teams can create pre-defined automated workflow automations. This means responses to various events can be automated, freeing up teams to manage greater risks.
- Detection & beyond- The most difficult part of shifting right to manage post-production cybersecurity, is knowing how to identify yet undiscovered vulnerabilities after devices are released to market.
By automatically generating an updated Software Bill of Materials (SBOM), Cybersecurity professionals are now relying on automatic monitoring, scanning, and detection of new threats with the development of each newly deployed patch or update.
These tools are critical in developing even further security measures, such as automated product security immediate response team (PSIRT), automated red teams, and a functioning product Security Operations Center (SOC). It also allows for greater cross-organizational collaboration as all vendors in the software supply chain can access an updated single source of data. If something occurs to a piece of software, the vendor can be notified immediately and a patch rolled out in less time. It is then on the manufacturer to ensure all other third party software is protected as well.
Shifting right is the best way forward
Shifting right is an acknowledgment that cybersecurity is an ever-evolving, shape-shifting foe. It demands the utmost vigilance from any organization– especially those whom people trust with their lives.
From an operational standpoint, shifting right allows for products to become future-proof, avoiding recalls by sending remote software updates. This works best when teams have an automated process for understanding which devices are running out of date software versions, or risky open source components. From a business perspective, shifting right protects the organizations you work with, ensuring that your devices and their networks are safe. For customers and end users, shifting right exemplifies your commitment to being a trustworthy partner into the future.
Despite this being a clear win-win for organizations, it is a process. Bolstering security during design and development, while also starting to build the post-production process, will make sure that your devices are secure and allow you to be compliant with standards and regulations. Only then can you begin to future proof your devices, keeping them secure for the long term.




