Information below is based on the data collected in our State of Critical Infrastructure Security 2023. View the full report for greater detail and context.
—–
With the increasing sophistication of cyber threats, it’s become imperative for manufacturers to implement effective measures to safeguard these devices, especially as continuous security management ranks as the second top device security challenge of 2023.
In this article, we’ll rely on the information collected for our State of Critical Infrastructure 2023 to explore the importance of staying up to date on the latest cybersecurity threats facing industrial devices and discuss best practices for managing device security.
Benefits of Continuous Security in Industrial Devices
Continuous product security should begin as early as possible, ideally integrated into the very early stages of any product’s development.
For companies that integrate a security-first approach, SBOMs can be developed at any stage, even during ideation. With each additional release of the product’s embedded software, the software and associated SBOM can be assessed as part of a workflow that scans for vulnerabilities and identifies other potential risks– allowing for early detection and mitigation.
Once the production phase has been completed, continuous security across a device lifespan relies on automated processes, which continuously analyze cyber risks with each product software iteration. Leveraging SBOMs as part of this management process is part of a greater workflow that identifies potential future issues, such as vulnerabilities, licensing risks, and regulatory compliance-related gaps.
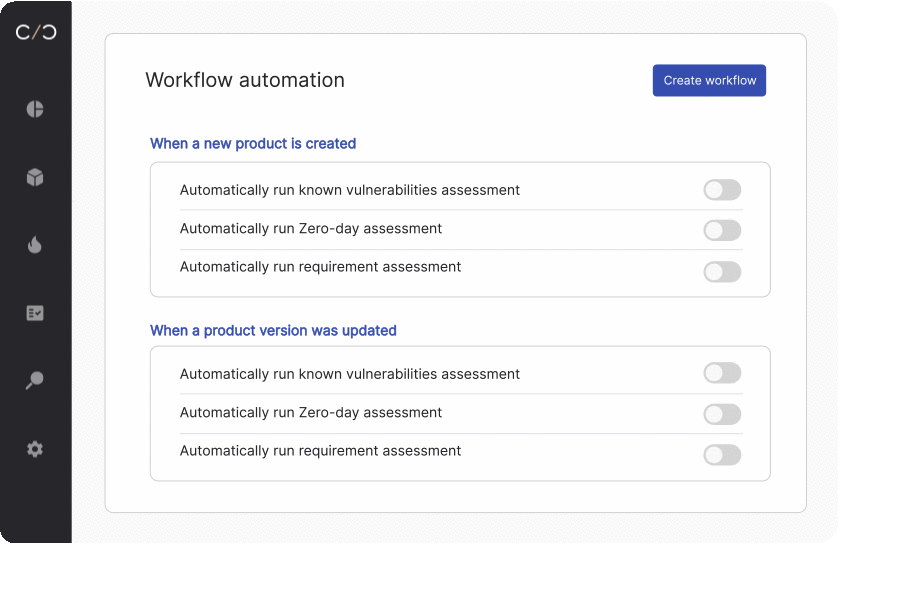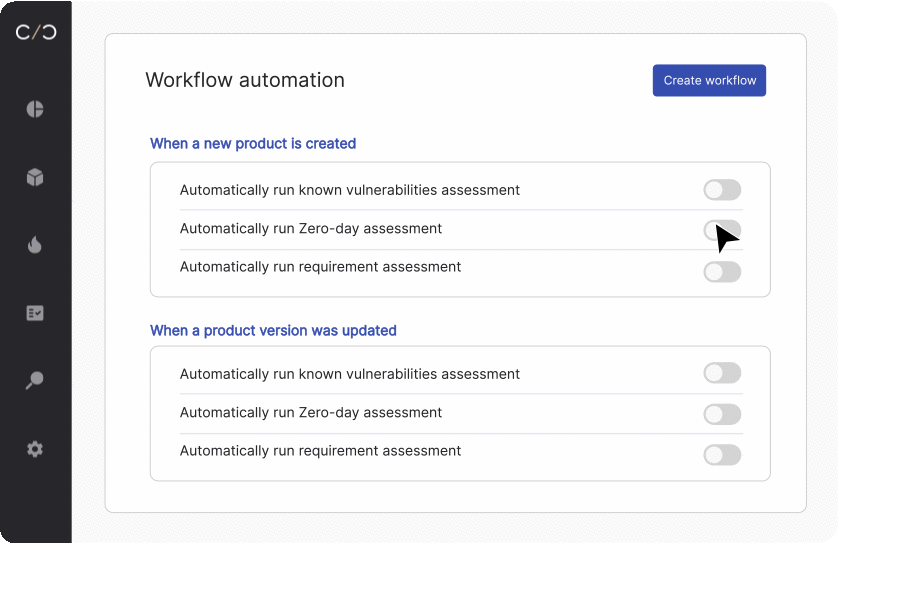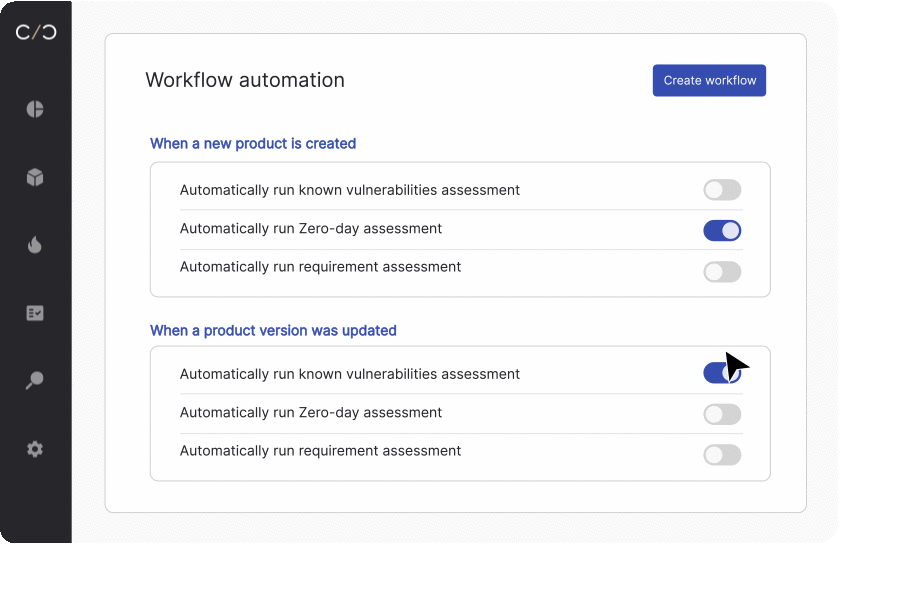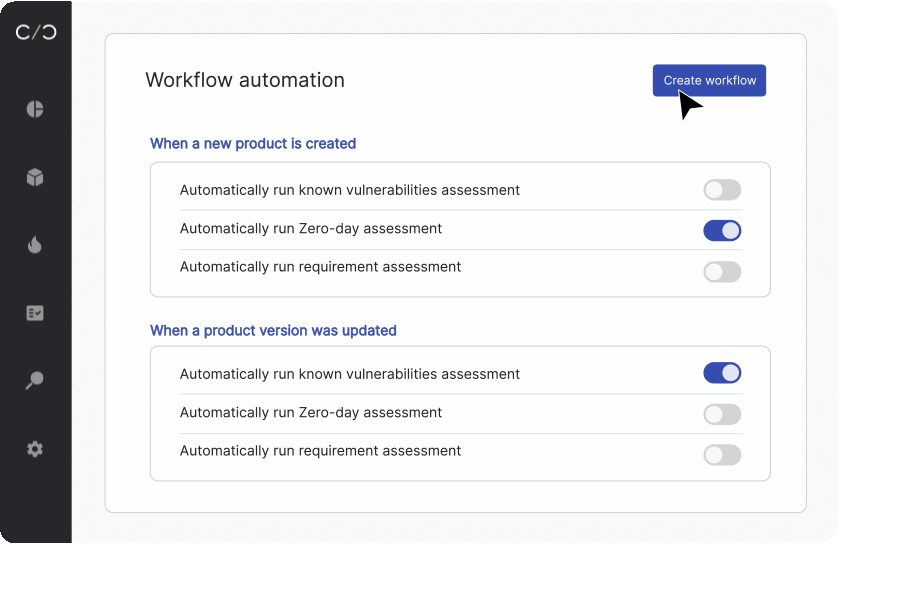
Ongoing security analysis and detection triggered by updated SBOMs offer several significant benefits for manufacturers, ensuring robust security measures throughout the device lifecycle. Let’s look at a few of the advantages.
Improved Threat Detection and Response Capabilities
Ongoing threat detection allows industrial equipment manufacturers to identify vulnerabilities and communicate their status, via VEX or other disclosure documentation, reducing time-to-remediation and safeguarding customers from a potential attack.
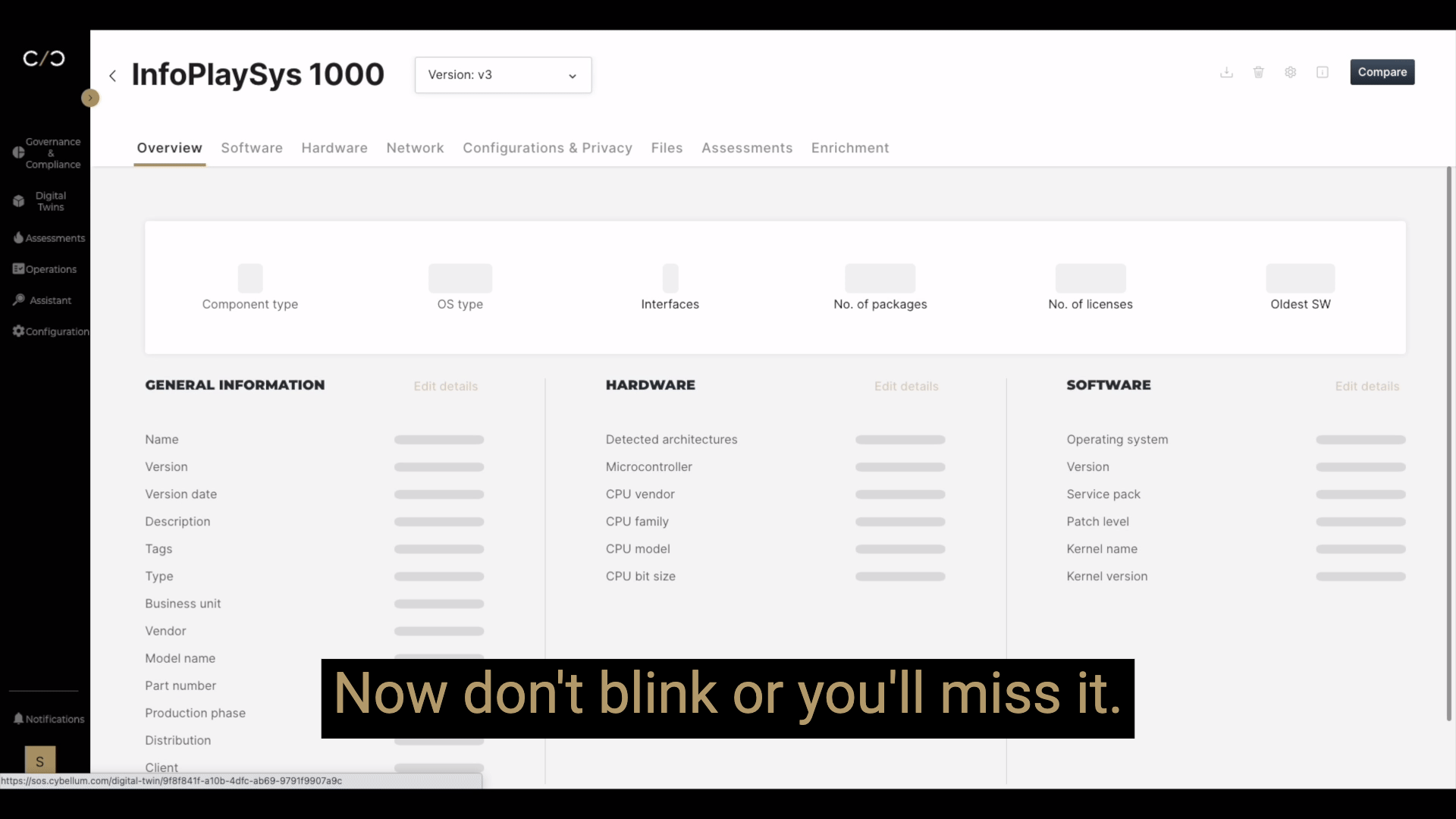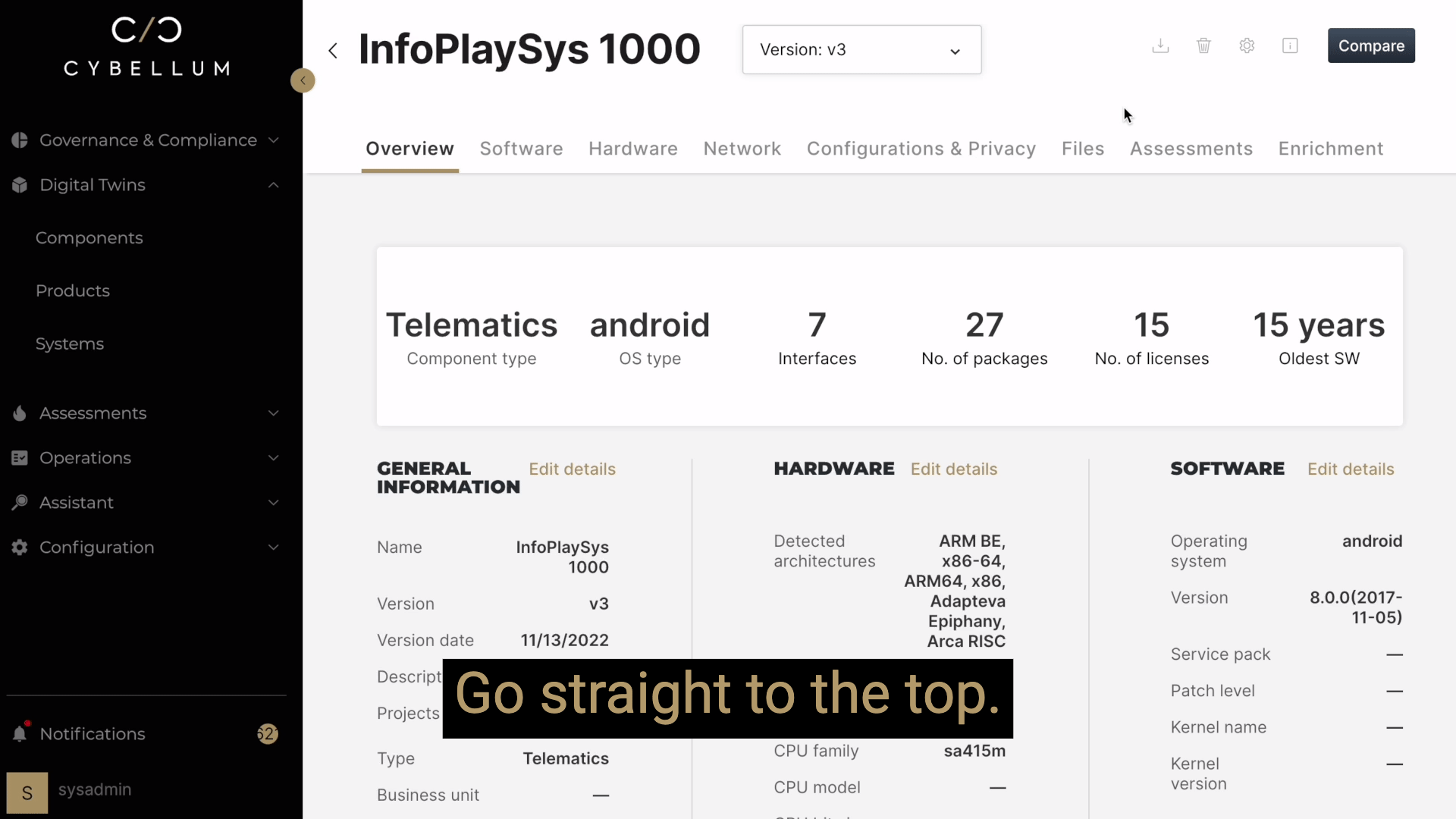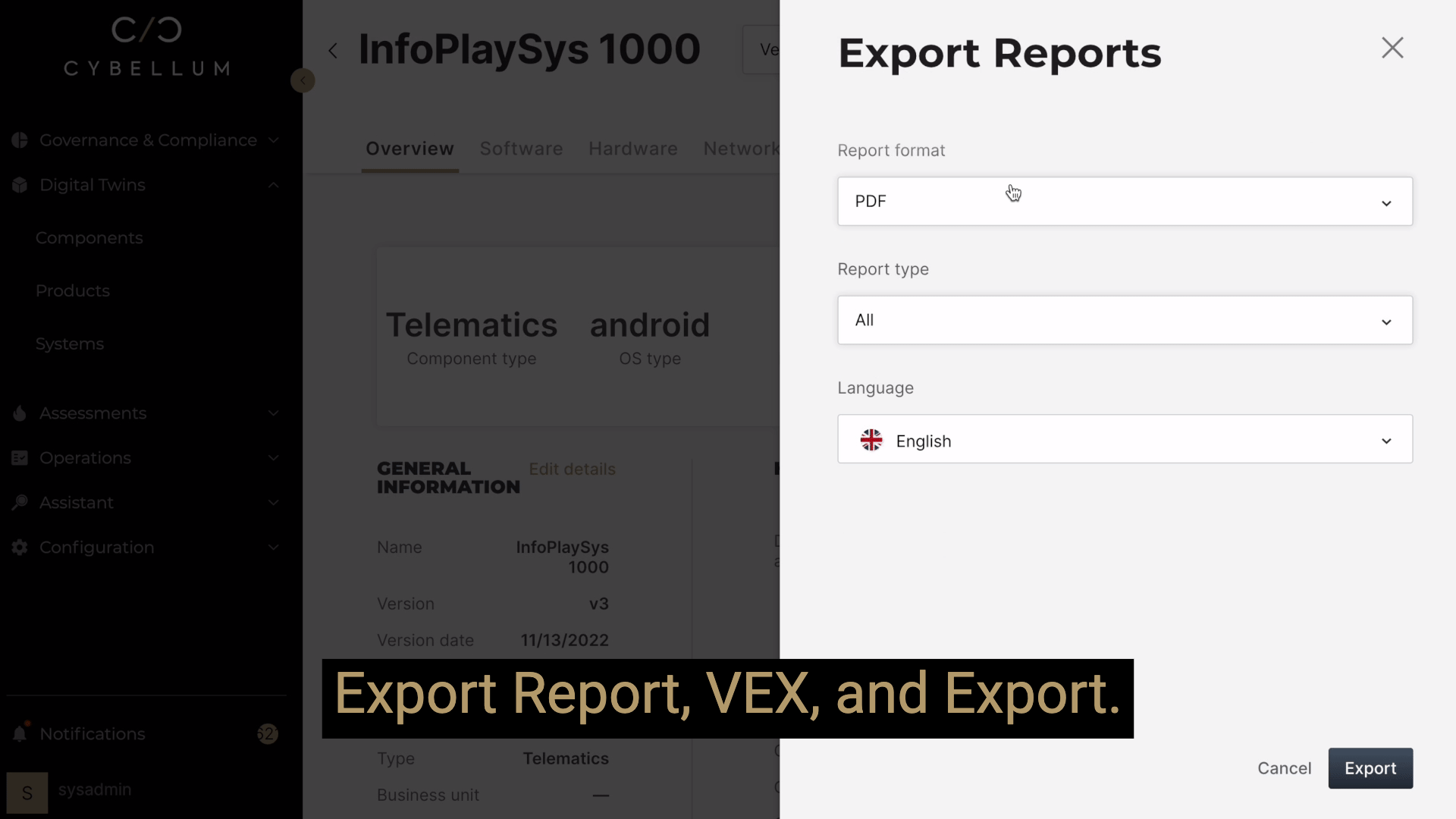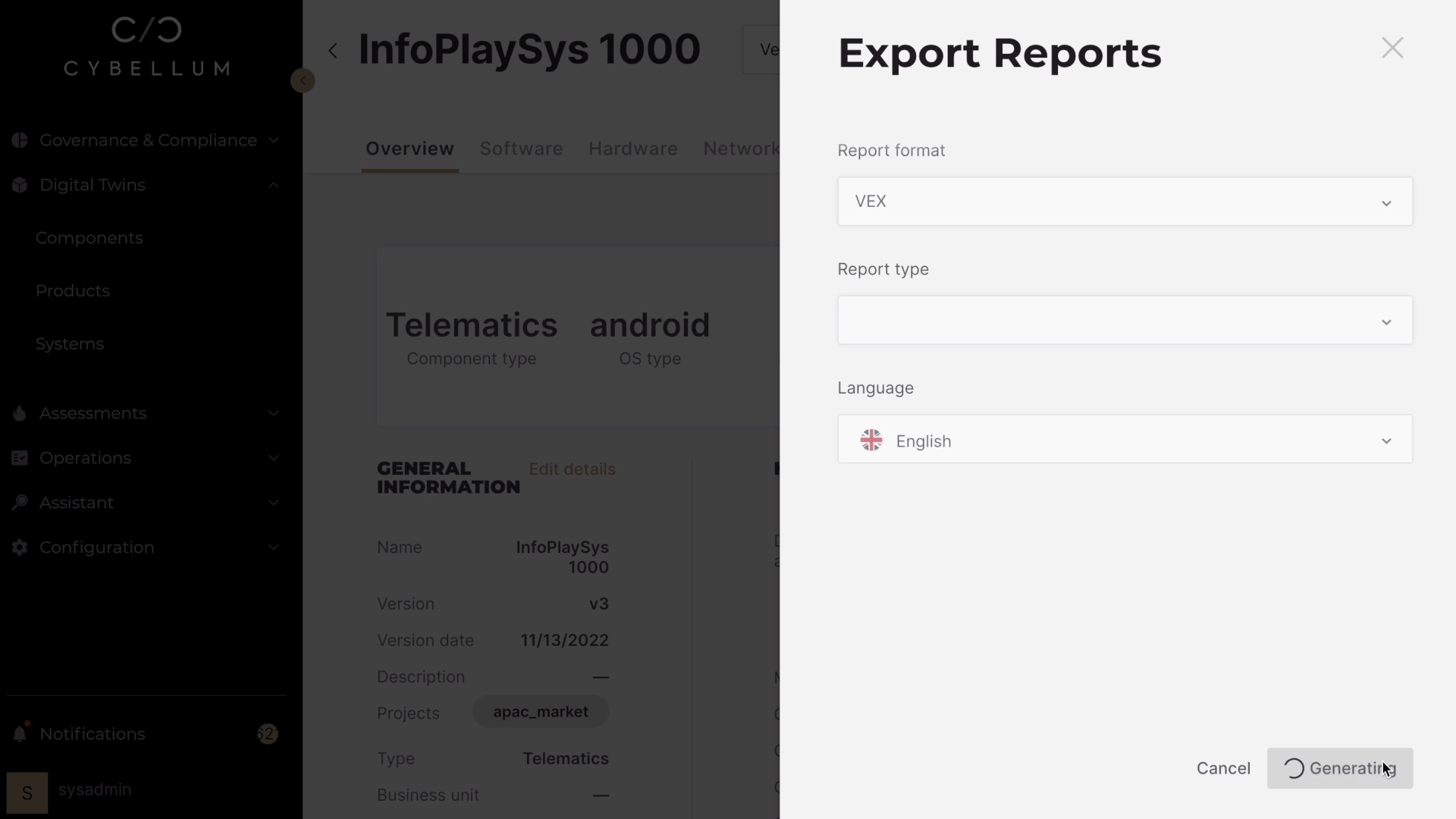
Mitigation of Security Risks Throughout the Device Lifespan
Industrial devices often have long operational lifespans, making it crucial to address vulnerabilities that may arise over time. Continuous product security ensures that security measures remain dynamic and adaptable as new demands emerge.
Staying proactive in identifying and mitigating security risks instills confidence in customers and regulatory bodies regarding compliance with industry-specific security requirements.
The Current State of Device Security Management
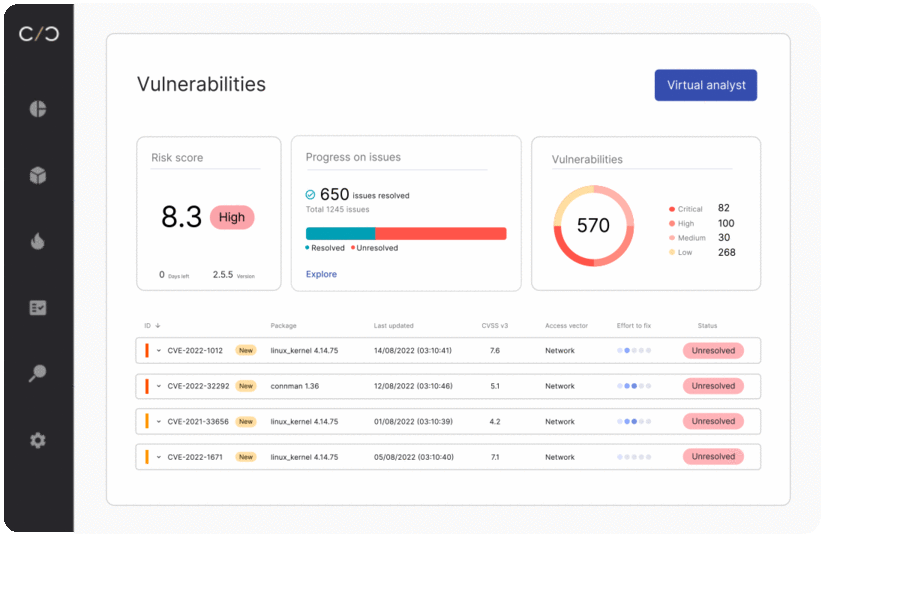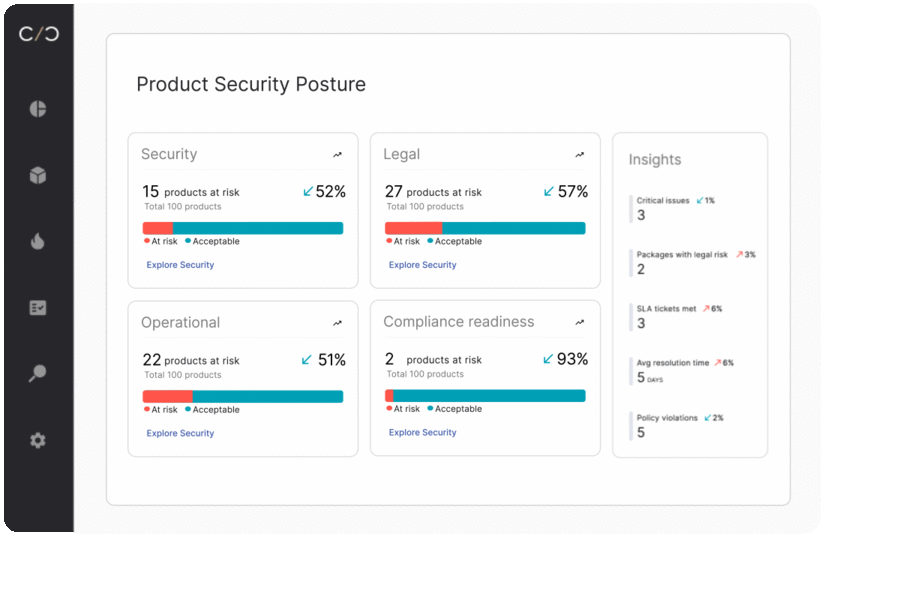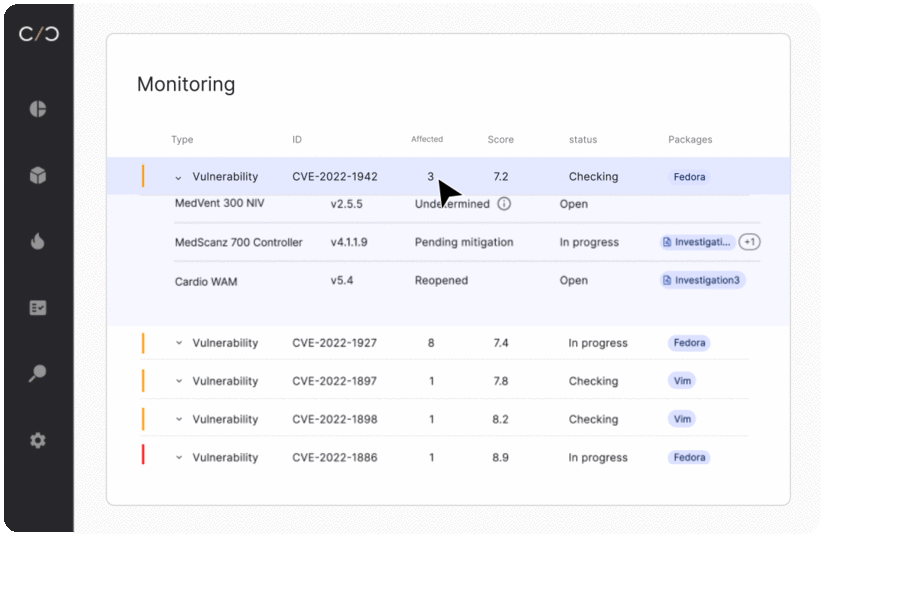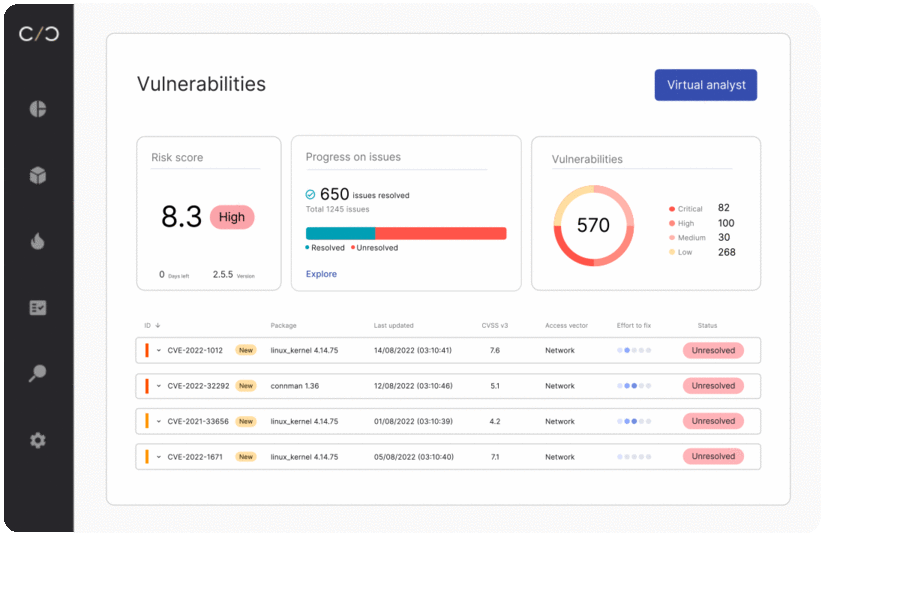
Despite its critical importance, managing device security in industrial equipment presents significant challenges for manufacturers. According to our 2023 Industrial Device Security Survey, continuous security management ranked as the second top device security challenge for 2023, with 30% of respondents highlighting its importance.
One major hurdle is the existence of siloed and fragmented processes, where a multitude of tools fail to communicate with each other effectively. This growing set of technologies was identified by 30% of survey respondents as a significant concern, as manufacturers require additional resources, expertise, and training to operate and integrate these technologies effectively.
This issue then leads to major inefficiencies, which may be one reason why enhanced efficiency emerged as the primary device security challenge in 2023, as indicated by 31% of the respondents. As manufacturers struggle with the complexity of navigating multiple security tools, each with its own unique interface and requirements, this disjointed approach hinders effective device security management and contributes to general operational inefficiencies.
This is all the more critical in light of the inherent risks and vulnerabilities associated with inadequate security measures, as industrial devices are prime targets for cyberattacks. As such, the consequences of a breach can be severe, leading to operational disruptions, compromised data, and potential safety hazards.
Best Practices for Focused Product Security
To effectively manage product security in industrial devices, manufacturers should implement the following best practices:
- Implement a proactive risk assessment strategy to identify and evaluate potential risks and vulnerabilities.
- Ensure vendors follow secure coding practices and standards by following established guidelines, conducting code reviews, promoting secure coding techniques, and providing relevant documentation.
- Rely on automation to conduct regular vulnerability scanning to identify and address security weaknesses and vulnerabilities in devices. They should then be rescanned with every software iteration.
- Implementing a continuous product security workflow, including a CI/CD integration, to automatically update SBOMs and related documents.
- Track relevant KPIs that give insights into the benefit of activities and device security progress
- Address product security throughout the entire lifecycle, enforcing security from ideation through post-production, to ensure ongoing security updates, patch management, and vulnerability remediation.
- Prioritize threat intelligence gathering (mentioned as a top device security priority for 2023 by 24% of respondents) to stay informed about emerging threats and adapt security measures accordingly.
- Train PSIRT teams to be ready for new attacks and emerging threats (prioritized by 21% of respondents).
- Foster collaboration and information sharing by collaborating with suppliers and partners to ensure end-to-end security.
The Benefits of a Comprehensive Security Platform
The issues in device security management, present in the industry today, point to a dire need for a comprehensive security platform. This brings several benefits to industrial device manufacturers, enabling them to effectively manage device security throughout the entire lifecycle, including:
- Holistic Approach to Managing Device Security: A comprehensive security platform provides a holistic approach to device security management. It integrates various security practices and use cases into a unified framework, ensuring seamless integration and collaboration across different teams within the organization.
- Seamless Integration of Security Practices: By leveraging a comprehensive security platform, manufacturers can seamlessly integrate security practices into their processes. This integration allows for consistent and standardized security measures, ensuring that no gaps or vulnerabilities are left unaddressed.
- Continuous Monitoring and Threat Detection: A robust security platform enables continuous monitoring of devices, ensuring reliable threat detection. By leveraging advanced technologies such as intrusion detection systems, behavior analytics, and machine learning, manufacturers can proactively identify and respond to security incidents promptly.
- Shared Data and Insights: A comprehensive security platform creates a shared set of data and insights that can be shared across different teams involved in securing devices, whether it’s during the pre-production or post-production phases. This shared knowledge facilitates collaboration, enables more effective decision-making, and enhances overall security governance within the organization.
- Enhanced Management and Governance: A comprehensive security platform acts as a key enabler for overall management and governance across the entire organization. It provides a centralized view of security practices, facilitates compliance with regulatory requirements, identifies licensing issues, and streamlines security operations, reducing inefficiencies and ensuring consistent adherence to security standards.
Wrapping It Up
In the rapidly evolving landscape of industrial devices, managing product security is vital for manufacturers to protect against emerging threats and ensure the long-term security of their devices. However, our survey reveals that many organizations face significant challenges in this area, with siloed processes, fragmented tools, and a lack of efficiency hindering effective device security management.
Collaboration, information sharing, and the adoption of comprehensive security platforms are crucial continuous security practices that will help bolster security posture, protect against threats, and ensure the resilience and integrity of industrial devices.
For more insights into the maturity of industrial device cybersecurity processes and the main challenges faced by today’s industrial organizations, download our full State of Critical Infrastructure 2023 today.