The data below is based on findings from the State of Automotive Security in 2023
—-
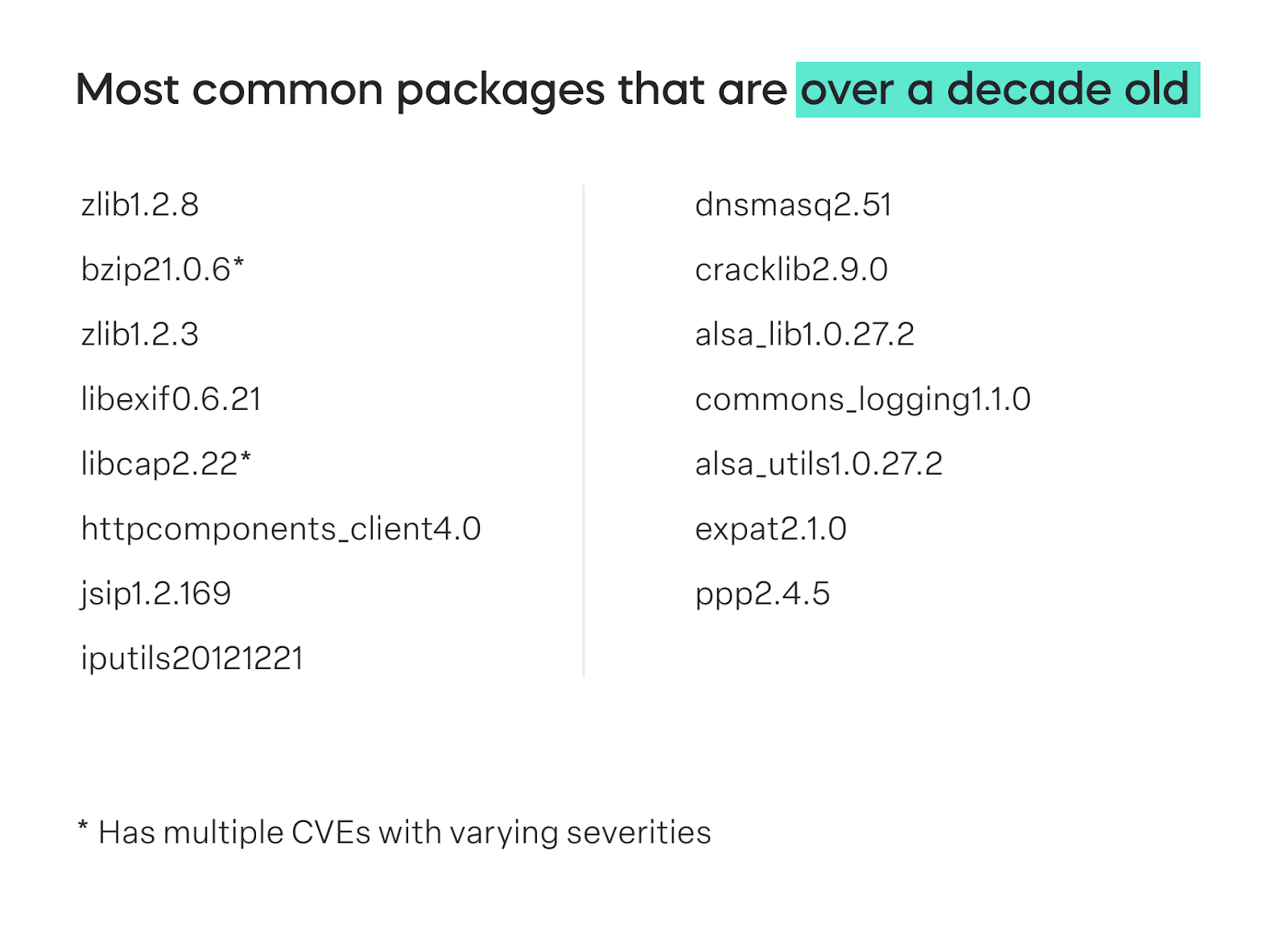
A significant proportion of software components in the industry—over 20%—are relics from a decade ago. This presents a striking dichotomy in product security standards between contemporary components and their antiquated counterparts.
The persistence of these older components, developed in an era of markedly different security landscapes, poses a tangible threat. A notable 24% of all automotive software elements were a decade or older. This scenario not only perpetuates existing cybersecurity vulnerabilities but also introduces a broad variance in security standards. The continued use of end-of-life (EOL) or end-of-service (EOS) software compounds these risks, urging a critical reassessment and potential replacement with more secure alternatives.
Open Source Software Components and CVEs
The automotive industry’s reliance on open-source software (OSS) components, maintained by a community of trusted developers, has its own set of challenges. While these components accelerate development, they also require rigorous security testing—a determining factor between a secure device and a potential security liability.
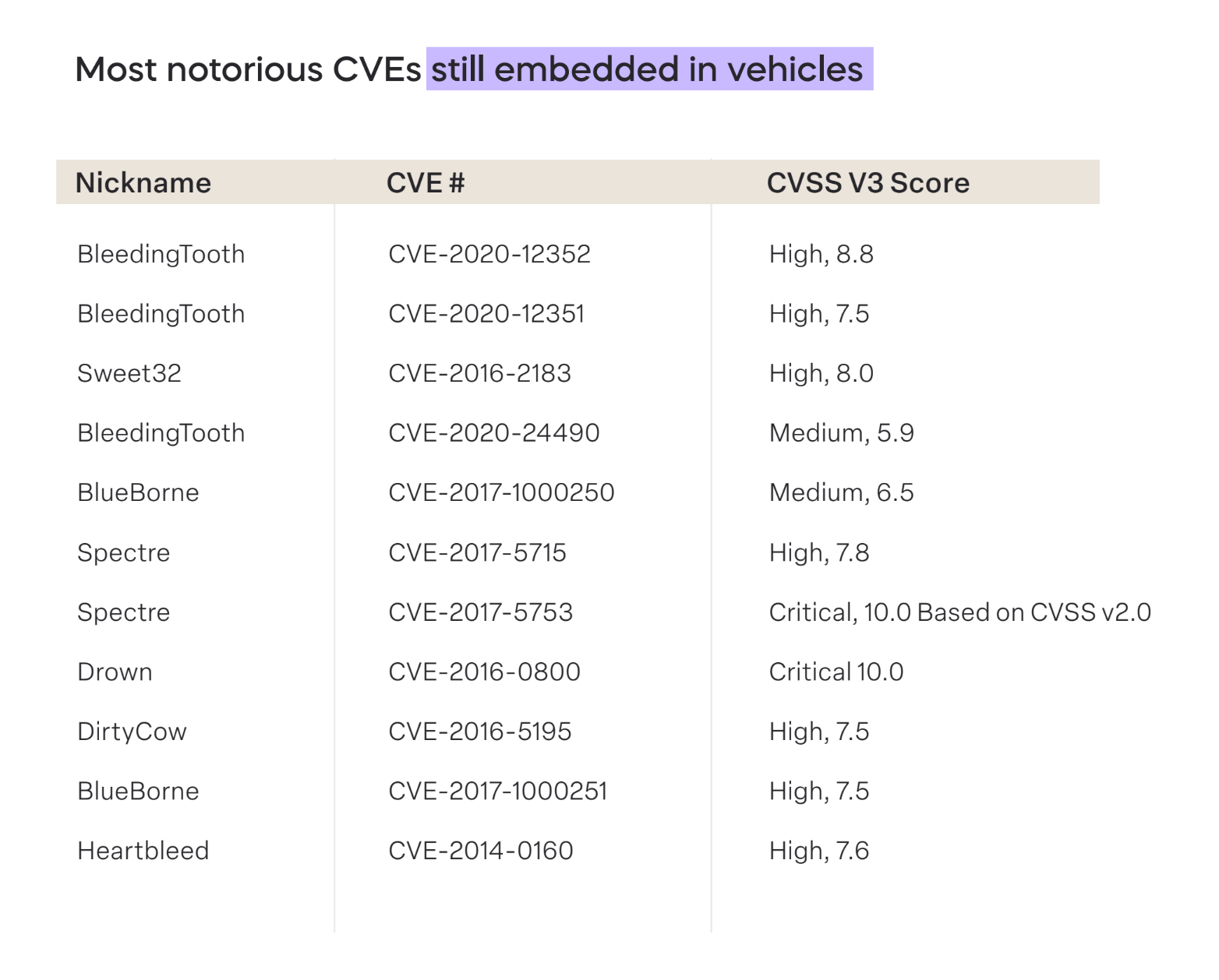
Alarmingly, 2023 data reveals the presence of high-risk Common Vulnerabilities and Exposures (CVEs) in vehicular systems. Two of these CVEs boast a Common Vulnerability Scoring System (CVSS) score of 10.0, signaling an unacceptable risk level. This situation underscores a significant gap in the industry’s processes for discovering, sharing, and addressing vulnerabilities. The impending implementation of international standards such as WP.29 R155, R156, and ISO/SAE 21434 could foster a more robust discussion on minimizing and preventing vulnerabilities within the automotive software supply chain.
Common Weakness Enumeration (CWEs)
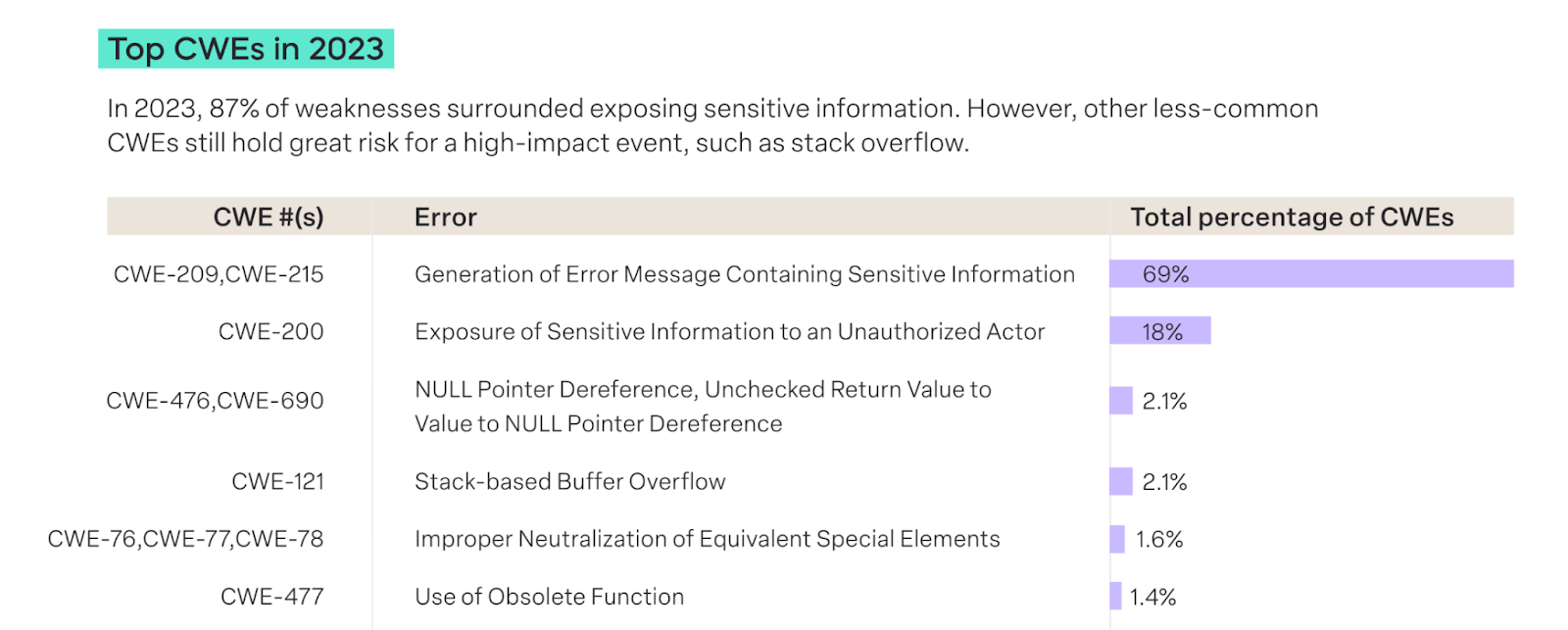
CWEs serve as a simplified classification system for identifying security weaknesses in both physical and software-driven systems. Like CVEs, CWEs are numerically designated for easy reference and updates. These weaknesses range from vulnerabilities that could lead to unauthorized data sharing to system shutdowns.
In 2023, the use of obsolete functions (accounting for 1.4% of top CWEs) and buffer overflows (2.2% of top CWEs) in the automotive industry, while relatively low, still present significant concerns. Buffer overflows, in particular, carry the potential to completely disable a device.
The Risk of Legacy Components
The vulnerabilities prevalent in connected automotive components often reflect risks identified years ago. A failure to comprehensively identify all embedded software components leaves teams blind to outdated, EOS, or EOL elements. The lack of maintenance for these components leaves their serviceability unknown, presenting a significant risk, particularly when older components are used in newer developments.
This challenge is exacerbated when development teams build upon outdated functionalities to create new features. As a result, common vulnerabilities continue to permeate today’s products through EOS/EOL software and outdated versions of current components.
The pain of both relevant and irrelevant vulnerabilities
Relevant vulnerabilities dropped this year from last year by 3%, from 33% in 2022 to 30% in 2023.
While this speaks to improved practices used across the industry, it also highlights the enormous drain on resources needed to sift through and triage this seemingly never-ending list of vulnerabilities. Without an automated process, Chief Product Security Officers (CPSOs) must dedicate both manpower and financial resources to identifying which vulnerabilities pose a threat and those that don’t.
Automotive safety, reliability, and compliance
As the automotive industry forges ahead in its technological evolution, the lingering presence of outdated software components, CVEs, and CWEs poses a critical challenge. It is imperative for industry leaders to not only recognize but actively address the inherent risks associated with these legacy elements. The convergence of cutting-edge development and robust cybersecurity practices will be key to ensuring the safety, reliability, and compliance of the next generation of automotive software.
Go further into the data in the State of Automotive Security in 2023




