With over 100 new vulnerabilities being reported daily and 11,613 new Common Vulnerabilities and Exposures (CVE) identified in 2023 so far. New CVEs, a key tool in identifying, categorizing, and prioritizing vulnerabilities, are on track to exceed 2022’s discoveries.
Naturally, everyone in the product supply chain finds themselves in an overwhelming position as mission-critical automotive, medical, and industrial devices become increasingly software driven.
Despite our best efforts to mitigate cyber attacks, we continue to introduce new vulnerabilities into our products which begs a deeper understanding of how these stubborn vulnerabilities make it past deployment and into the products our clients use. Often, developers unknowingly introduce vulnerabilities into the software by incorporating code from sources like Stack Overflow, Github, or other open-source libraries. This code might have unnoticed security vulnerabilities, contributing significantly to the overall risk.
So how does a vulnerability make its way into a product and hitch a ride throughout the device’s full lifecycle?
Vulnerability scan frequency and human error
The lifecycle of a vulnerability is complex. Imagine you’re a chef, concocting a dish. But there’s a catch – you’re unsure about the ingredients in your pantry. That’s how a software development team feels without an up-to-date SBOM (Software Bill of Materials). Each new software component or ‘ingredient’ can be a wild card, triggering a domino effect on dependencies and stirring up fresh vulnerabilities like uninvited dinner guests.
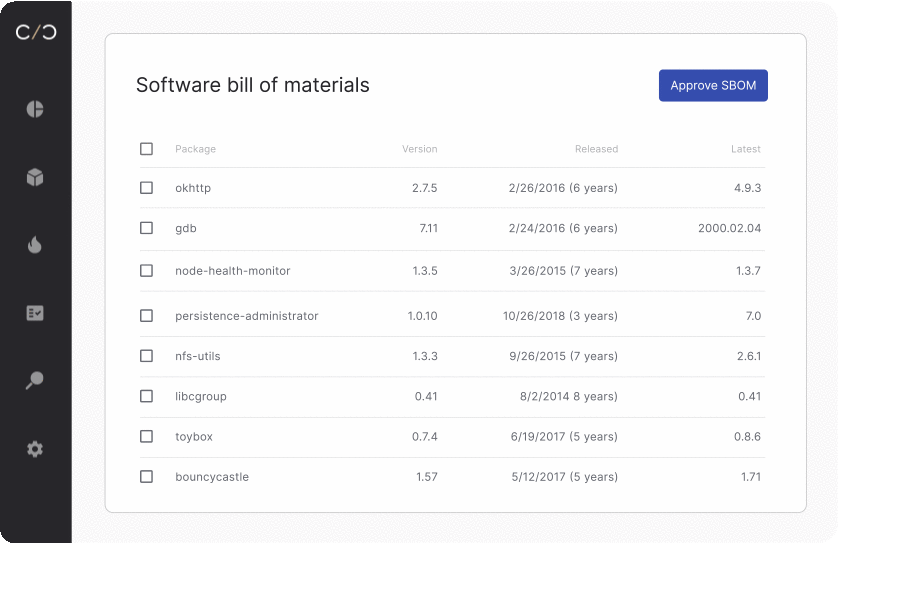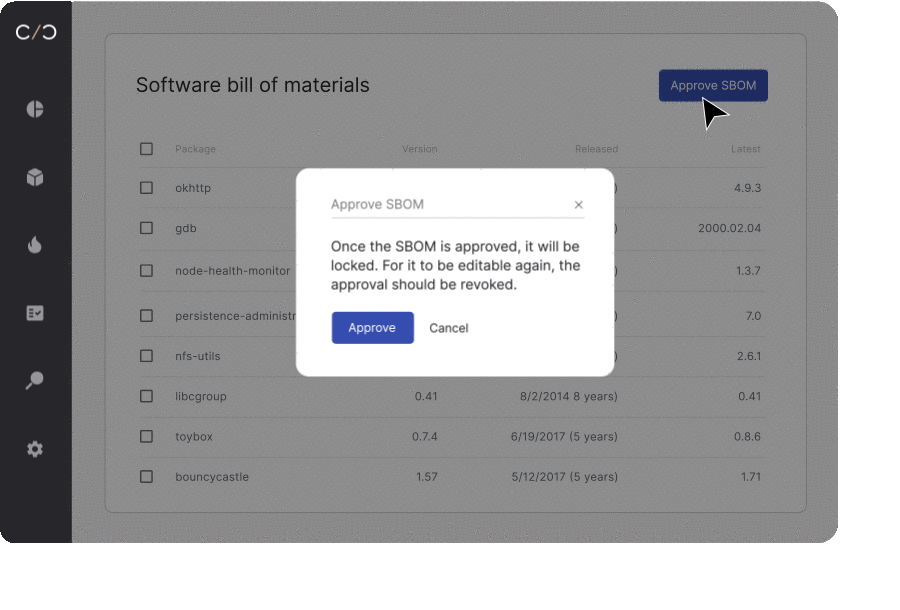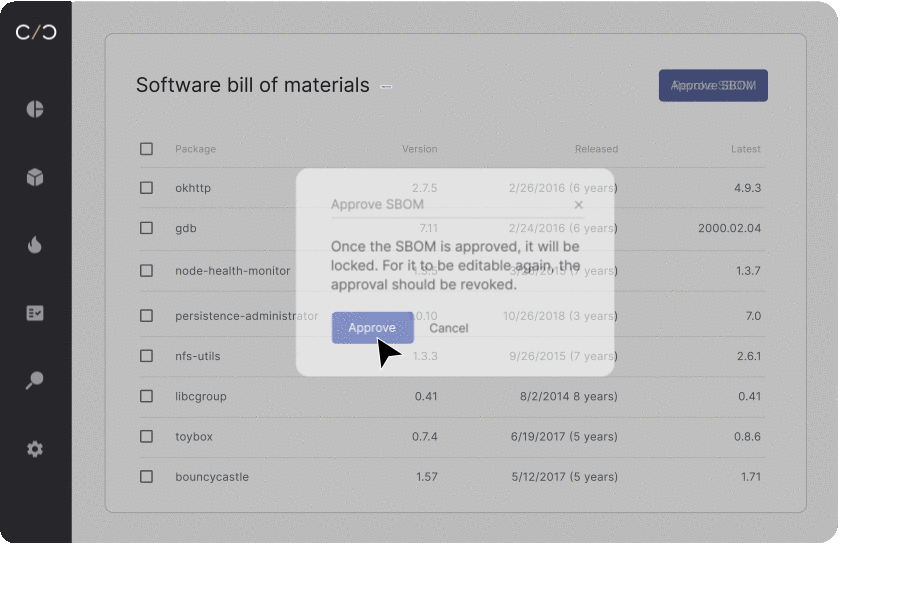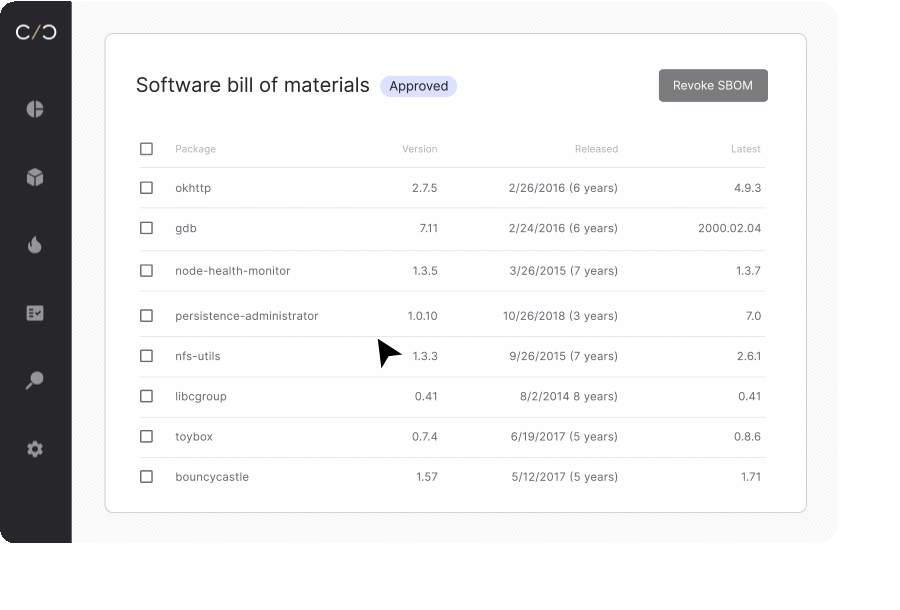
Rushing a product to market often feels like a high-stakes race against time. In the pit stop, security professionals juggle budgets, functionality, and a ticking clock. The constant pressure and tight deadlines can make comprehensive vulnerability checks seem like an unaffordable luxury.
Its critical for Chief Product Security Officers (CPSOs) to implement a security culture’. Led by a strong focus on security in all aspects and stages of development, regular training, and processes that ensure higher quality from the start can save significant headache down the road.
Many professionals don’t have the luxury to check and recheck for vulnerabilities after every change to the code. The thing is, it’s not a luxury, it’s a necessity. If a product was secure in the early development stages but wasn’t rechecked before deployment, it doesn’t mean it’s still secure. Not scanning for new vulnerabilities at every step of development can backfire after deployment.
For many manufacturers, product security is not part of quality control.
It’s like hiring a builder to put up a security wall, but unbeknownst to you, part of the wall is made up of paper that will be penetrated at the first attempt. This gaping hole in a meticulous fence can be opened with the introduction of a new unsecured component. Without implementing security culture documentation or SBOMs, developers don’t know what’s inside the component they just sourced.
Identifying these reactions can be challenging without transparency into the component ingredients. But not all vulnerabilities are created equal.
Not all vulnerabilities are exploitable
There are a range of tools to manage and assess software vulnerabilities. Catalogs, calculators, and ratings help us find and assess the exploitability of vulnerabilities, aiding in prioritization and patching efforts.
Understanding the different types of vulnerabilities is a must to ensure the security and safety of connected devices, particularly in mission-critical systems.
There are three primary types of vulnerabilities to consider:
Easily Exploitable
These vulnerabilities can be exploited with relative ease, often resulting from common programming errors or oversight. Usually, exploitation methods for these vulnerabilities are well-known and documented.
Dormant vulnerabilities
Dormant vulnerabilities exist in the software but are currently not exploitable due to various factors, such as a lack of pathways for exploitation. However, they may become exploitable as the software evolves or new exploitation methods are discovered—another reason to monitor products in the field continuously.
Complex vulnerabilities
Complex vulnerabilities require a high level of expertise to exploit. They often involve chaining multiple vulnerabilities together or exploiting subtle flaws in intricate algorithms or protocols.
Mature security teams leverage VEX reports and SBOMs to know which components are a security threat and require mitigation and which components have no impact. Businesses that wish to enhance the security of connected devices must opt for smarter use of their resources if they want to continue to provide safe and secure products to their consumers.
Safety vs. security critical
Connected devices require higher security and safety of both hardware and software, as vulnerabilities can impact operationality and data.
To better manage risk, it’s important to distinguish between the security and the safety of connected devices:
Security Critical
Security-critical systems are those in which security measures are of the utmost importance. The potential impact of security breaches in these systems is high, making the maintenance of confidentiality, integrity, and availability of data and services paramount. Examples of security-critical systems include banking systems, military systems, and healthcare data systems.
Safety Critical
Safety-critical systems are systems whose failure or malfunction can lead to severe consequences, such as death or serious injury to people, loss or significant damage to equipment or property, or environmental harm. These systems are prevalent in industries like aviation, healthcare, industrial manufacturing, utility operations, and automotive.
Exploitable vulnerabilities can hit both. Understanding the distinction between security-critical and safety-critical systems is important, but identifying and assessing vulnerabilities’ severity and potential impact before deployment is even more so. Appropriate identification, prioritization, and allocation of resources for effective vulnerability management must be standardized across the supply chain to help the different teams working on these products communicate better.


How to locate, assess, and mitigate vulnerabilities
Many weaknesses and unknown dependencies may remain undetectable without visibility into the guts of upstream components. Transparency and visibility into components allow us to find, evaluate, prioritize, and act on risky vulnerabilities on time. The severity and potential impact of a vulnerability should be carefully assessed before deciding on the appropriate course of action.
Implementing robust controls, increasing visibility, and adopting a risk-based approach to vulnerability management is another form of quality assurance that will help us build a resilient supply chain of secure connected devices.
While CVE and Common Weakness Enumerations (CWE) serve as broader frameworks for identifying and discussing vulnerabilities and common weaknesses, VEX reports provide crucial information on specific device-focused security analysis and recommendations about vulnerabilities, exploitability, recommended fixes, and more.
Vulnerability management is quality control
Once you understand how vulnerabilities can creep into connected products, it becomes clear that vulnerability management is an essential aspect of quality control in developing and deploying connected products. It is important to recognize that while vulnerabilities will always exist in connected products, not all require patching, as some may never be exploitable.
Effective ongoing monitoring and information sharing are necessary throughout the supply chain to maintain quality control of mission-critical connected products. By checking and rechecking for vulnerabilities throughout the supply chain, from development to manufacturing and deployment, potential security issues can be identified and addressed early on. However, this can only be achieved if the security teams share information and work together.
By using the tools at our disposal, we can recognize and mitigate actual risk, focus more on exploitable vulnerabilities while keeping an eye on currently unexploitable ones for any changes in their status and build more reliable connected products in a world of ever-evolving cyber threats.