While developers speed up their work by utilizing open source components, they also rely on libraries maintained and created by a trusted community of their peers. When it comes to security, their ability to conduct thorough security testing is the difference between a secure device and one that poses a danger to operators.
However, with automotive regulation entering the next stage of its rollout later this year, data shows that security testing in the industry still has a way to go.
2023 data shows that many of the most notorious CVEs, multiple with a CVSS v3 score of 10.0, are still embedded in vehicles today despite years-long efforts to reign in known risks. As frustrating as that may be, companies that don’t properly address these vulnerabilities may see their vehicle not earn Vehicle Type Approval (VTA) or perhaps be revoked down the line (only time will tell).
So, how can companies keep their vehicles on the road while addressing the tediously long list of vulnerabilities– 70% of which are not exploitable or relevant according to the State of Automotive Security 2023 report?
Realities of today’s vehicle security
Much of the vulnerabilities we are seeing throughout connected automotive components continue to remain those whose true risk posture was exposed years ago. By not identifying all embedded software components, teams are unable to identify if any are outdated, have reached end of service (EOS), or end of life (EOL). When software is not maintained, there is no way to know that it is unserviceable without conducting a full product security check.
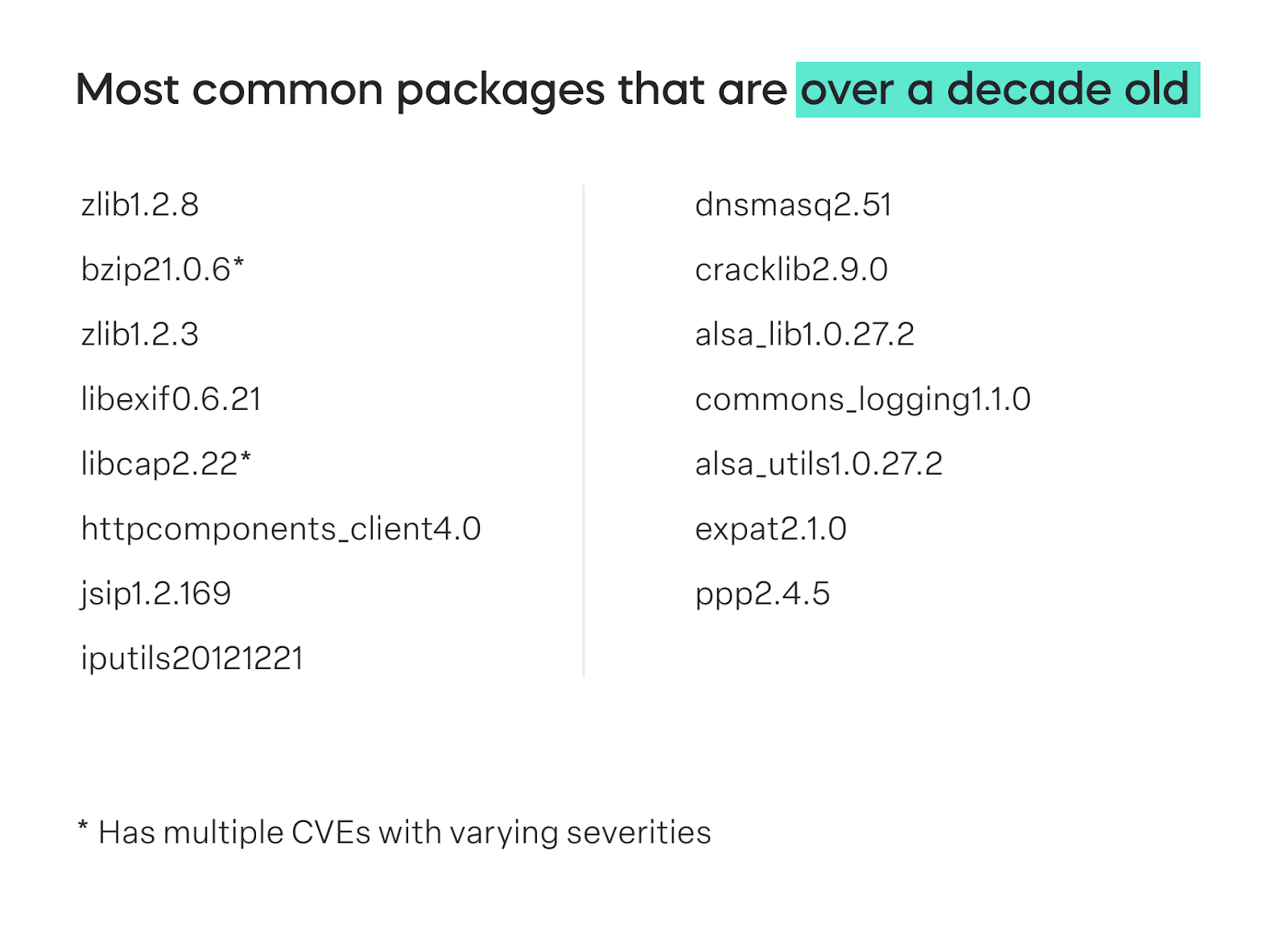
Relying on older components potentially exposes vehicles to exploits found in the wild.
This unacceptable level of risk mentioned above speaks to the wide gap across the automotive industry regarding how vulnerabilities are discovered, shared, and addressed. Soon, with the implementation of WP.29 R155, R156, and ISO/SAE 21434, companies will have to implement some standardized practices regarding automotive cybersecurity vulnerabilities. This can harbor a greater discussion of not only how to minimize vulnerabilities but also prevent them from ever entering the software supply chain.
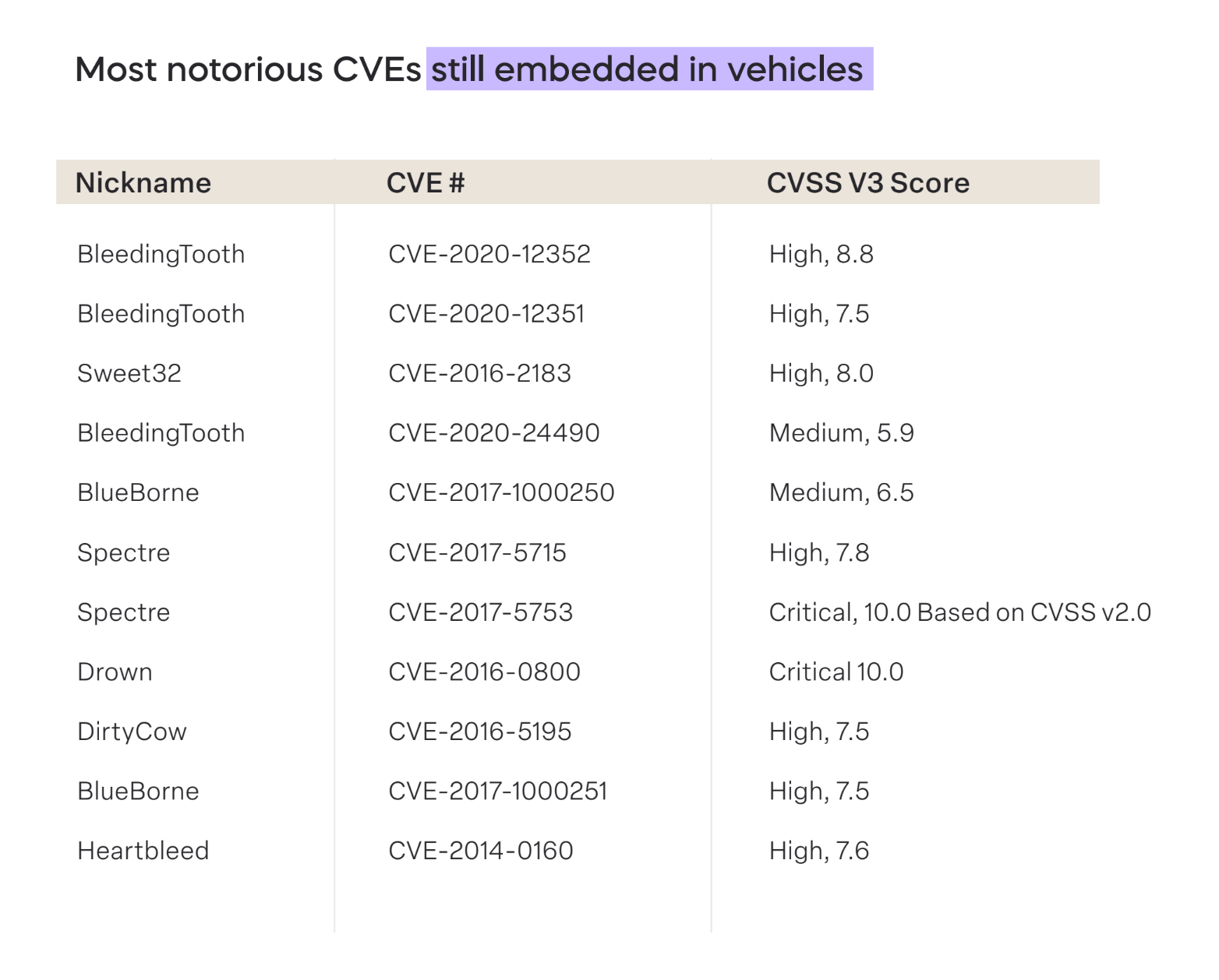
While it seems obvious that teams should be sitting and picking out pesky vulnerabilities, the reality is that they are challenging to identify. Without an automated product security platform that can fulfill various CSMS requirements, identifying and triaging vulnerabilities will be a manual resource-intensive process, which may not satisfy the company’s needs or R155 requirements.
Why automation is now required
With full WP.29 R155 implementation, it will become a joint requirement for both product security and compliance teams to work together in order to address vulnerabilities and report on their outcomes in a timely manner.
To facilitate this cross-departmental communication, UNECE’s R155 requirements include the adoption of a Cyber Security Management System, or ‘CSMS’ as it’s come to be known. Part of this system is its ability to introduce scalable automation to address the growing amount of code present within today’s vehicles.
For businesses’ this requirement comes at a time when automation can be used to ensure that the embedded automotive software, whether it be AUTOSAR or any other, is as reliable as the frame it’s resting on.

Relevant to both OEMs and suppliers who fall under UNECE WP.29, it also encourages the use of a standard format that companies can utilize to quickly pull the data they need without interrupting vehicle operations.
Opportunities in automotive regulation
The upcoming full implementation of WP.29 R155 is not just a regulatory hurdle to clear. It’s an opportunity to refine our approach to product security, ensuring that our vehicles are not just marvels of engineering but also bastions of digital safety. Automation in product security is no longer optional but essential, offering a streamlined, efficient path to identifying and addressing vulnerabilities that might otherwise slip through the cracks.
Download the State of Automotive Security in 2023 and help the industry implement a more secure future.