For Chief Product Security Officers (CPSOs), the landscape of cybersecurity regulations often feels like shifting sands. Rolling regulations, new rules and standards that get released every few months, necessitate constant vigilance and adaptability. But staying current with constant change is a challenging task for CPSOs. They are tasked with interpreting new changes, updating compliance processes, and putting new standards into team member action. All this while identifying and managing vulnerabilities that are hidden inside components from across the entire supply chain.
Understandably, CPSOs struggle to build secure products with minimum vulnerabilities when every day, 100s of new ones are discovered. The only thing left to do is to build a managed product security workflow- one that is focused on future-proofing and safety by design.
The Regulatory Landscape
The rapid rate of new product security regulations affects virtually every industry– and it shows no sign of slowing down. For instance, the automotive sector is currently grappling with implementing steps to meet UNECE WP.29 R155 & R156 as well as ISO/SAE 21434. The medical field is influenced by the federally legislated FY 23’ Omnibus, leading to the implementation of an October 23’ refuse-to-accept policy with new cybersecurity-related guidelines expected later this year. For the industrial sector, rolling regulations are taking the shape of CISA’s minimum SBOM and VEX guidelines, the EU’s NIS2, and other guidelines that require CPSOs to implement new compliance checks without impacting facility operations.
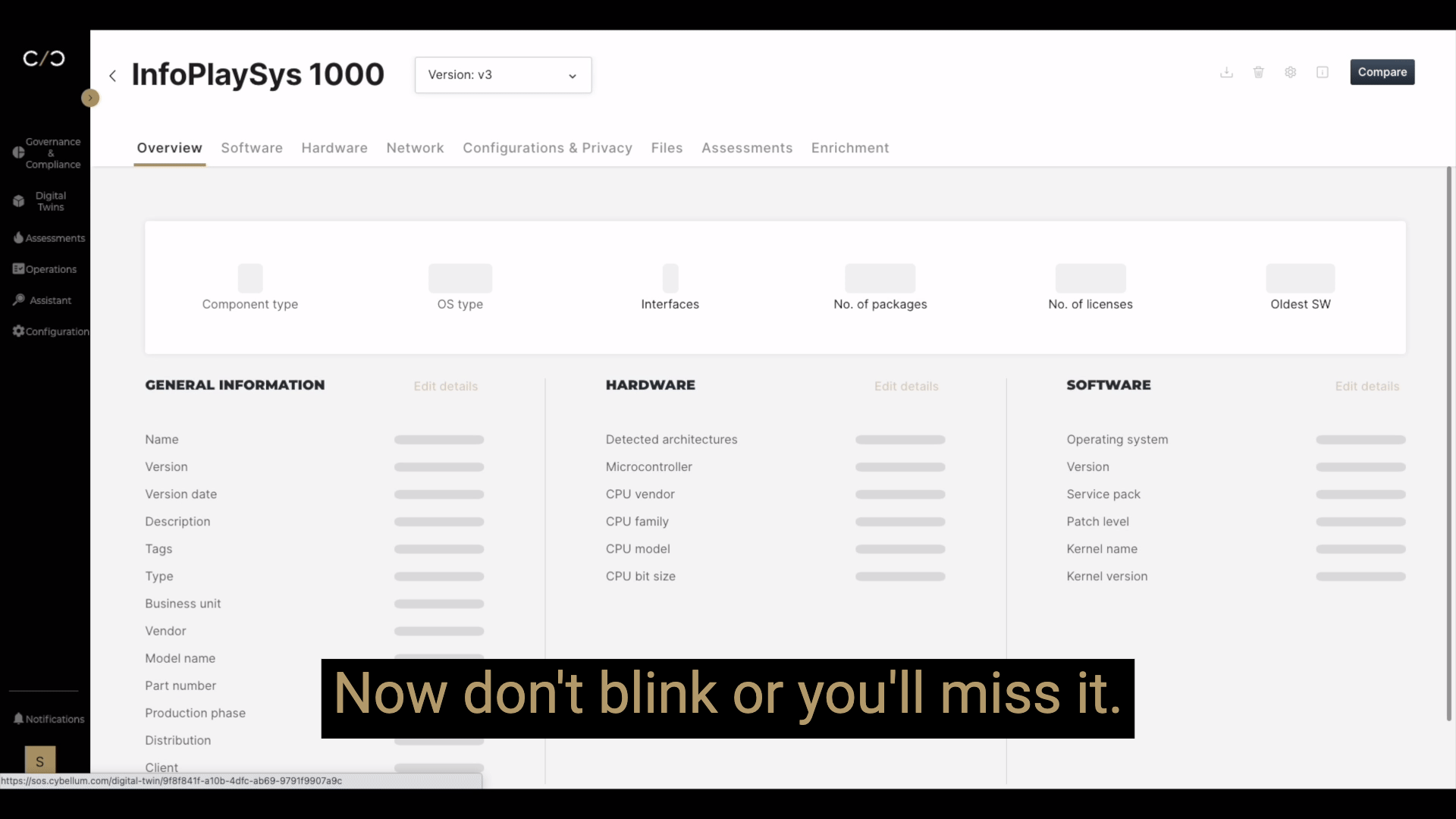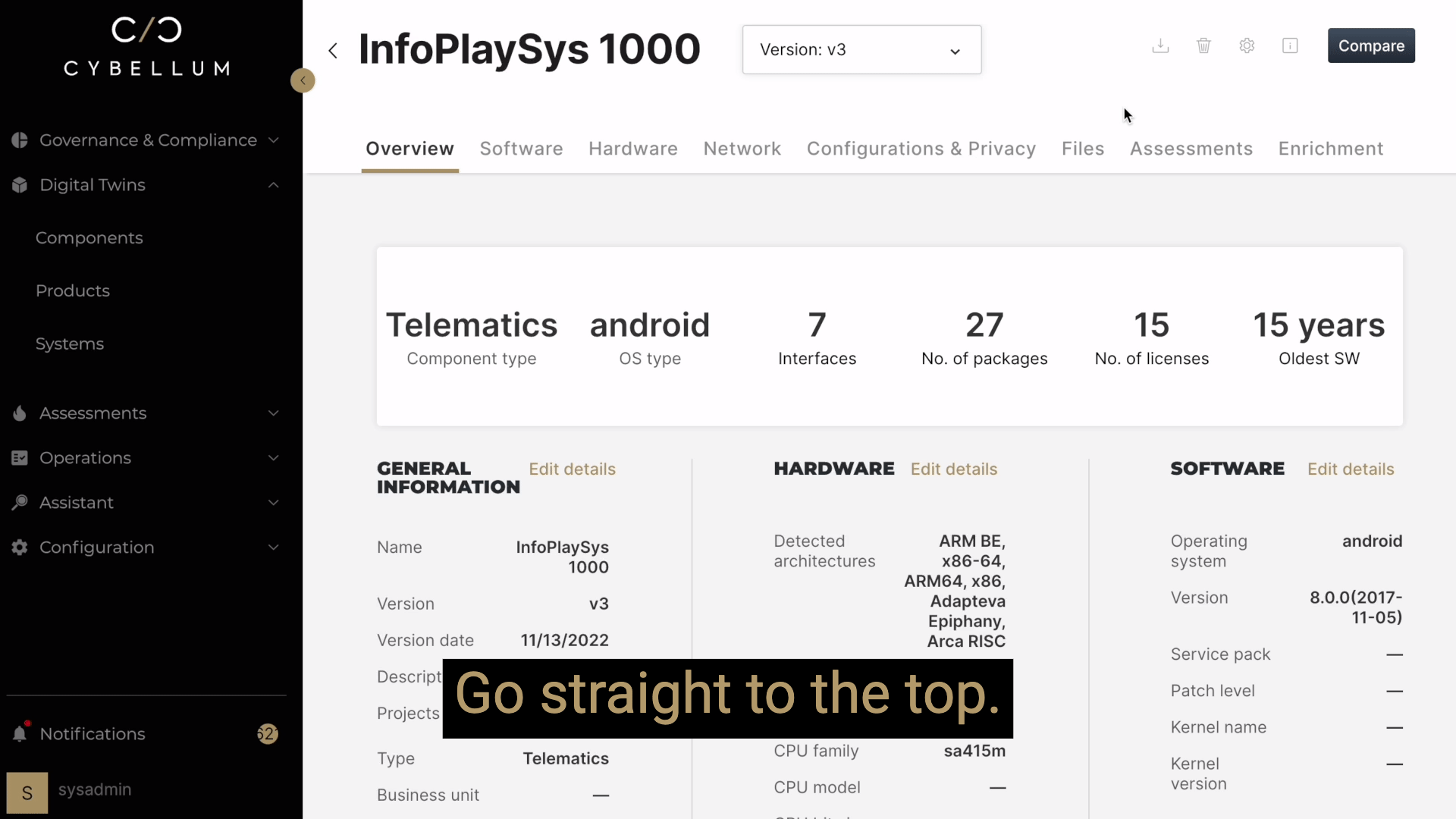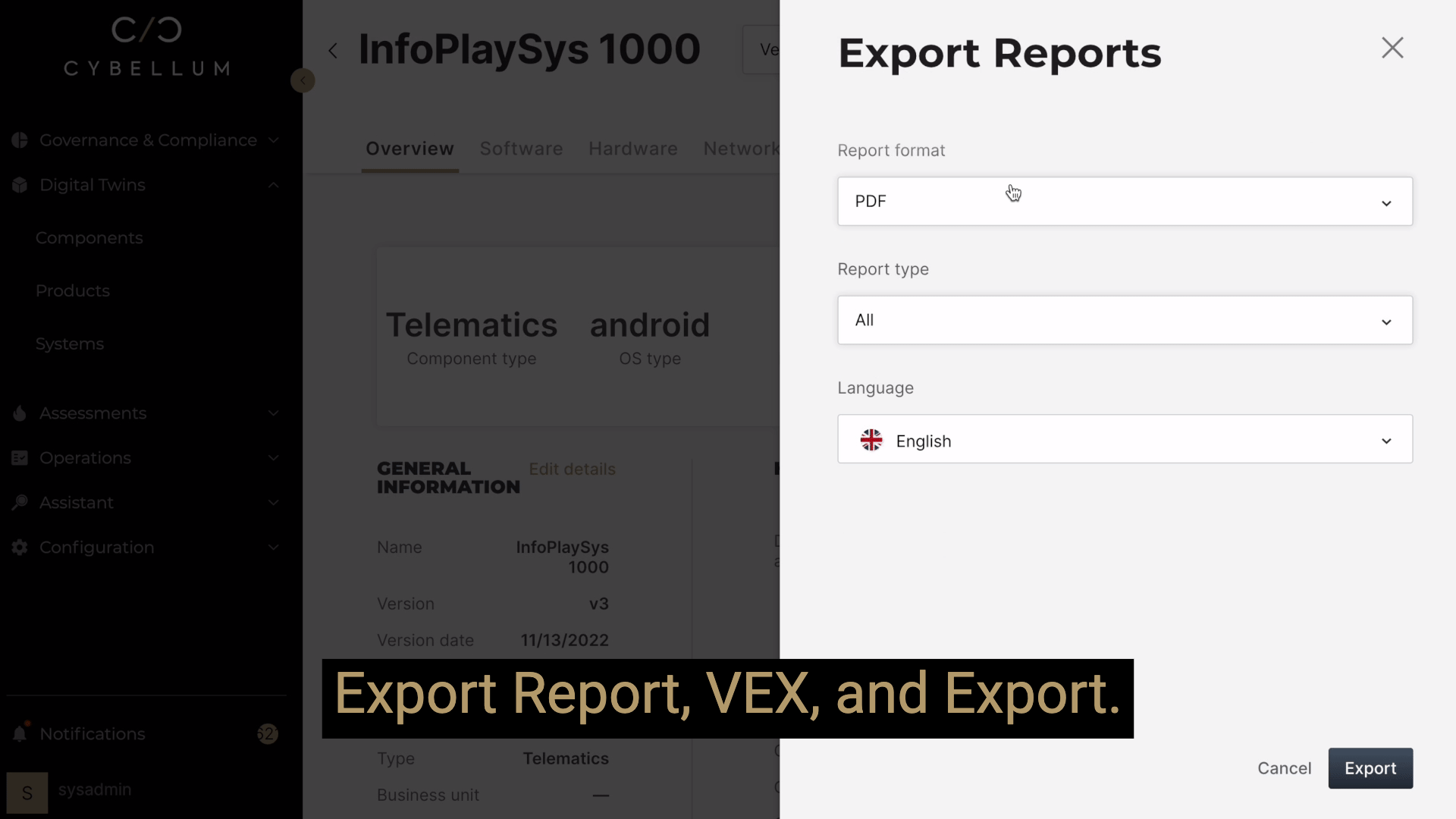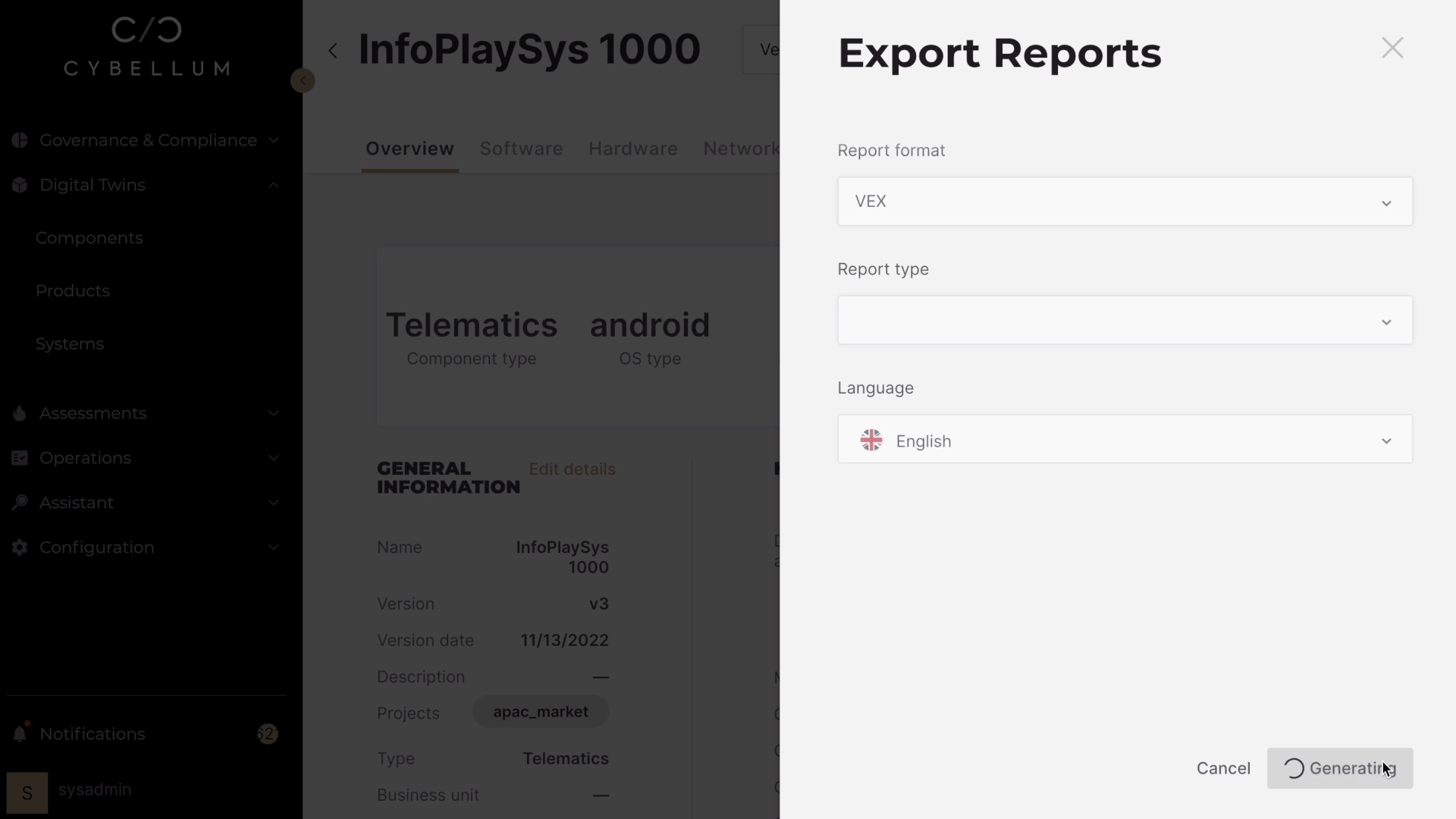
Given the scope of changes these regulations have brought with them, the approach of playing whack-a-mole with each new regulation or finding product security loopholes is untenable. It doesn’t hold up from a business perspective or operational necessity. Worst still, it complicates the already intricate processes security teams have to go through to find, assess and act on weaknesses for effective vulnerability management and ever-changing compliance management.
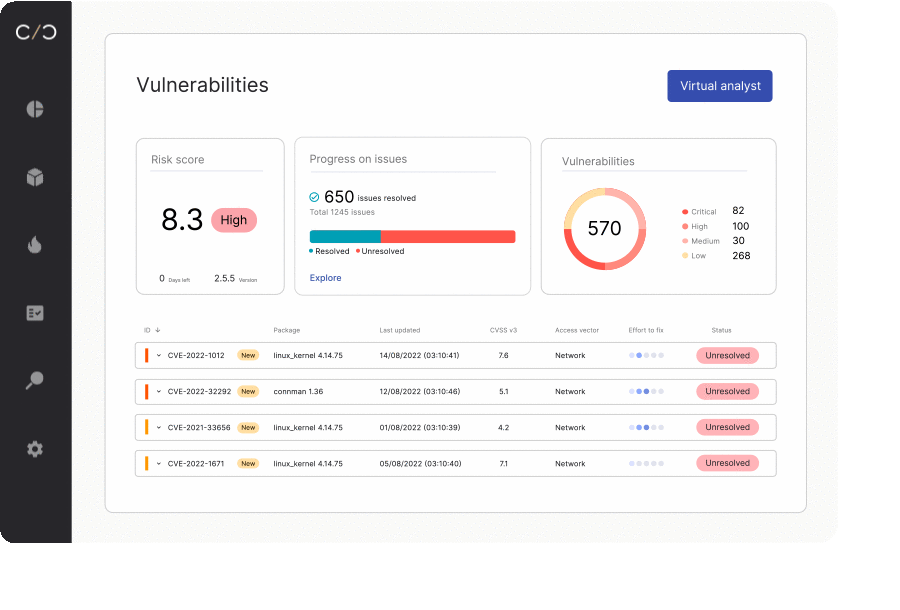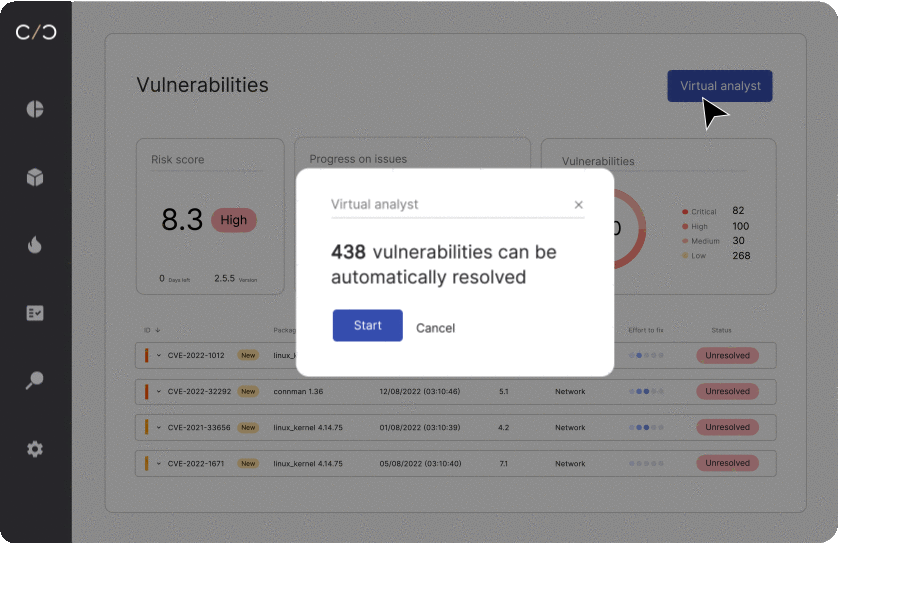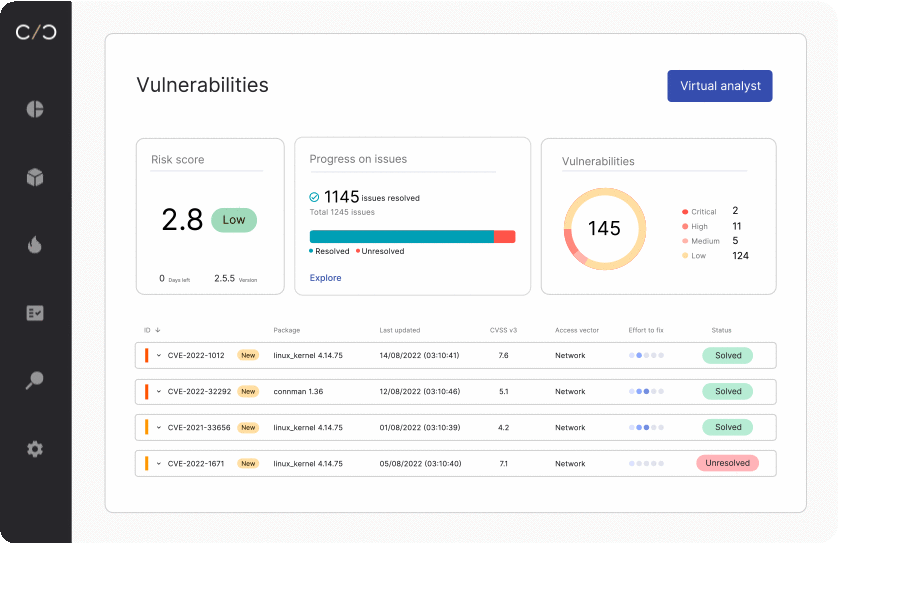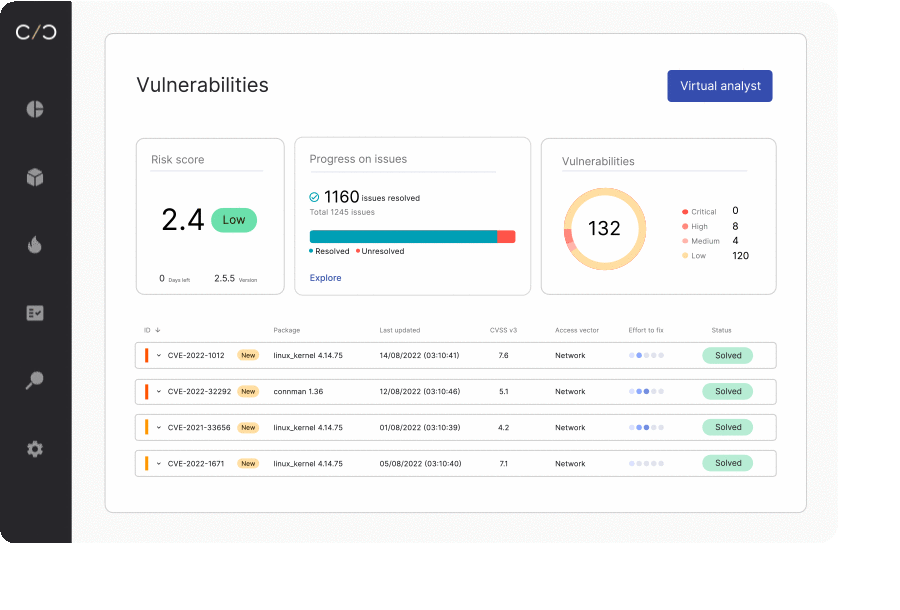
Future-Proofing Lies in Foundational Documentation
The key to strong and future-ready product security is to create robust, comprehensive, and foundational documentation that can be relied on for compliance as well as a source of truth. This documentation should be designed to measure KPIs, meet current compliance demands, monitor internal policies, and accommodate new regulations as they are rolled out.
KPIs allow CPSOs to measure progress, identify areas of improvement, and ensure they’re meeting compliance goals efficiently and effectively. Building a strong foundation starts with reviewing current policies, understanding their strengths and weaknesses, and determining how they can be bolstered to withstand future changes.
Once foundational documentation is in place, tracking and integrating new policies becomes a more streamlined process, creating a smooth path for transitions.
Creating and updating SBOMs can be a good starting point. By focusing on foundational documentation, CPSOs can ensure they’re building on a strong, organized, and transparent approach rather than an unstable house of cards that can crumble under the scrutiny of regulators or the assault of threat actors.
Once foundational documentation is in place, tracking and integrating new policies becomes a more streamlined process, smoothing the path for transitions.
Streamlining Regulatory Compliance with a Unified Workflow
The wave of rolling product security regulations creates labor-intensive processes for product security teams that have yet to embrace automation. The solution? A unified product security workflow that can funnel all activities into one process.
This workflow should encompass all product activities, from development, compliance, deployment, and beyond. Such a design enables teams to introduce and manage new regulations seamlessly without having to reset or re-tool any part of the production process.
In addition, it adds a layer of transparency and adaptability no matter what team or supplier is working on the product.
Turn Rolling Security Regulations into an Opportunity
In short, embracing rolling regulations doesn’t have to be a laborious process. With the right strategies in place, including foundational documentation, measurable KPIs, and unified workflows, product security teams can turn the challenge of rolling regulations into an opportunity for enhanced security and continuous improvement. Rather than playing catch-up with each new regulatory wave, it’s time to build safer products with confidence and control. Regulations are a pain, but at the end of the day, the goal is to create safe and secure connected devices end users can trust. In other words, safety by design is key.