We would like to inform our clients about a security issue that came to our attention, as part of our commitment to transparency and the ongoing security of our products.
On June 21, 2023, a security researcher named Delikely reported an issue to Cybellum’s security team, specifically within a certain distribution of Cybellum’s software.
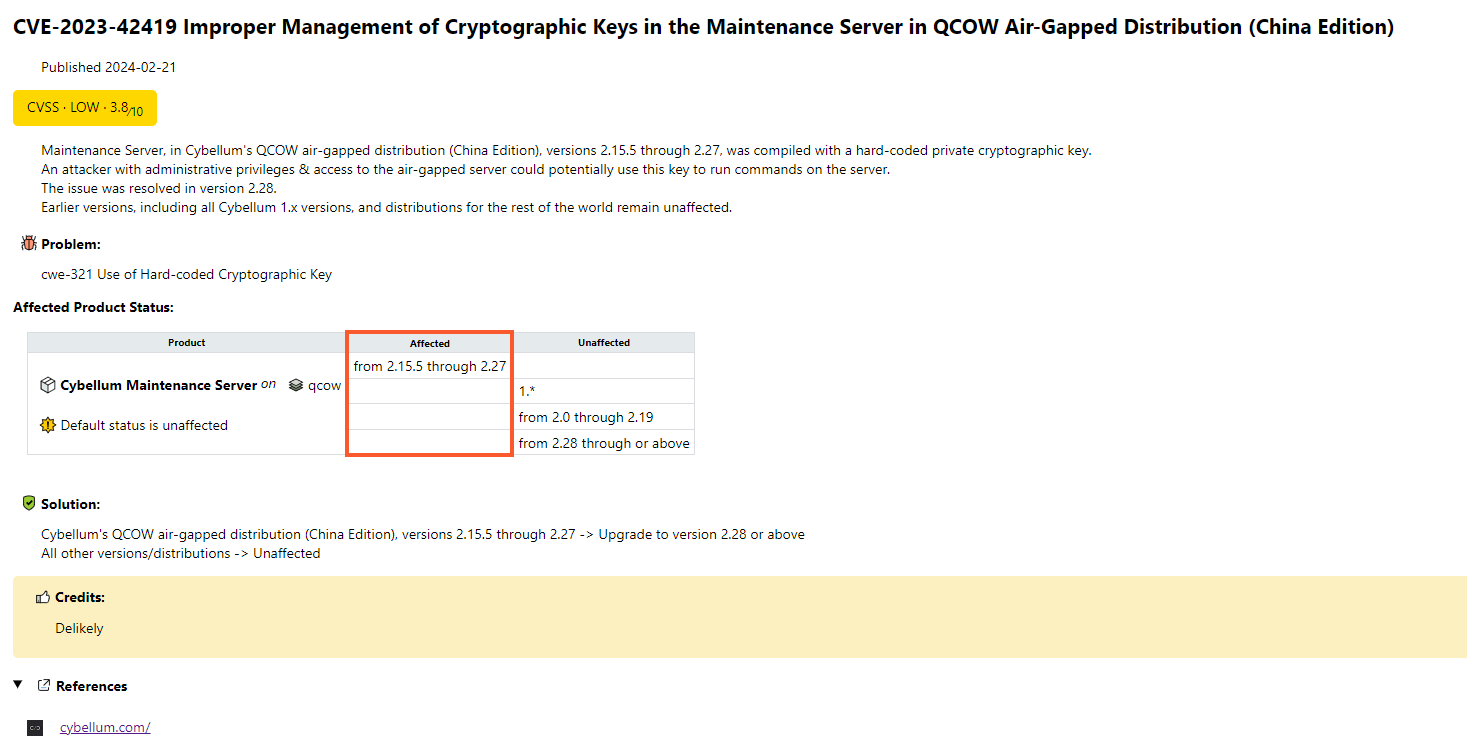
This issue was found in the Maintenance Server of Cybellum’s QCOW air-gapped distribution, exclusively deployed in China, affecting versions 2.15.5 through 2.27. The details are published in the NVD and can be found here.
It does not impact older or newer versions, including Cybellum 1.x.
The issue stemmed from a private cryptographic key within Cybellum’s QCOW distribution and was quickly addressed with a hotfix applied to the systems of affected customers.
A permanent fix was introduced and implemented in version 2.28. In addition to that, we inspected vulnerable systems and found no evidence of exploitation.
To exploit this issue, an attacker would need to satisfy two conditions:
- Gain access to the Maintenance Server of a QCOW air-gapped distribution (exclusively deployed in China).
- Obtain an administrator access key.
The likelihood of exploiting this issue is exceptionally low, as it requires both deep network penetration and the possession of an administrator key.
It’s crucial to highlight that this issue does not affect:
- Cybellum versions 1.x
- Cybellum versions 2.0 through 2.15.4
- Cybellum version 2.28 and above
Furthermore, editions distributed outside of China remain unaffected.
We extend our gratitude to Delikley for responsibly disclosing this issue. At Cybellum, we take security extremely seriously and are committed to maintaining the highest security standards. We are thankful for the community’s vigilance and support in helping us improve our product. Such collaborative efforts are invaluable to our ongoing mission to provide secure and reliable software.
FAQ
Q: How critical is this issue?
A: With an official CVSS score of 3.8, this issue is classified as LOW SEVERITY.
Q: How do I know if I’m affected?
A: If you’re using Cybellum’s QCOW air-gapped distribution for China, versions 2.15.5-2.27, you’re affected. Otherwise, you’re not.
Q: What if my version is unaffected?
A: No action is needed.
Q: How do I fix this issue?
A: Upgrade to version 2.28 or later. Or reach out to [email protected].
Q: Was this issue exploited in the wild?
A: To the best of our knowledge, no. A fix was released and deployed to all customers between July and August 2023. The details of the issue were made public on February 18, 2024.
Q: Does this issue affect findings or reports?
A: No, the issue is confined to the Maintenance Server and does not impact the Product Security Platform.
Q: Does this issue compromise users’ private information?
A: No, the issue is confined to the Maintenance Server which doesn’t include private information.
Q: Does this issue function as a backdoor?
A: No, it involves a private cryptographic key that was mistakenly deployed in Cybellum’s QCOW image.
Q: How can we prevent a recurrence of such issues?
A: We are continuously enhancing our security protocols through an improved Secure Development Lifecycle (SDLC), comprehensive penetration testing, rigorous code reviews, and the adoption of leading SecDevOps practices.
Q: What if I have additional questions?
A: Contact us at [email protected] for assistance.
Michael Engstler
Co-Founder & CTO, Cybellum