The new technology helping Medical, Automotive, and Industrial manufacturers manage vulnerability noise and costs.
We need to talk about product vulnerability management
One of the biggest problems in product security is undoubtedly cutting through the vulnerability noise. With more software-driven products than ever, more lines of code, and more complexity in the supply chain, we now have more product vulnerabilities discovered every day, and that number is growing exponentially.
Add to that the unique nature of embedded devices – where each product is built differently and has its own unique architecture. Where different industries have different workflows and configurations. Where there aren’t nearly enough trained product security analysts as needed – and you get a task that’s nearly impossible to pull off.
The good news is that there are now major advancements in product security technology and AI that could finally set things straight for struggling product security teams, allowing them to automate device vulnerability prioritization way more efficiently.
Companies like Microsoft have recently introduced cybersecurity analysis tools based on the likes of Chat-GPT. This is exciting, as combining similar but more focused AI capabilities with embedded system know-how could lead to a significantly improved vulnerability management process. In fact, such a technology called VM Co-Pilot already exists and is already used by large manufacturers from the Automotive, Medical Device, and Industrial Manufacturing industries.
Challenges in cutting through vulnerability noise
Why is cutting down vulnerability noise so difficult?
Looking at the product development lifecycle, there are 4 major contributors to the complexity of managing connected device vulnerabilities:
- Scale and complexity – The number of products under verification and validation is growing and due to a lack of resources, most organizations only do sample test units and move forward after receiving the results– taking a huge risk on poor visibility. In addition, the amount and complexity of software is rising, which means verification and validation is more difficult to perform and takes more time
- Inability to adapt to continuous product development workflows – In an ideal world, we would want the security test to be part of our CI/CD process in multiple phases during the manufacturing process. This proves to be extremely difficult, since the manual processes we rely on limit the number of tests we can do. In most cases, tests are usually done at the end of the process, and, as we know, the later you fix a problem the more time and resources it takes to correct.
- Time pressures – product development has to adhere to extremely strict deadlines, which proves problematic for extensive security verification and validation. Manual analysis forces us to make a costly compromise between time to market and product safety and security.
- Unknown business risk – There’s a growing need coming from top management of manufacturing organizations to connect product security with risk management – communicating the actual business impact of every vulnerability. This is extremely difficult in industries such as Automotive and Medical Devices, where safety and intended use have to be intertwined with product security, in order to assess the actual risk to the business and human lives.
First thing’s first - exploring the vulnerability management workflow
There’s no way around it. Today’s challenges demand a new approach to connected device vulnerability management and prioritization. One that can deal with scale, continuity, time pressures, and business risk, while cutting down costs– all efficiently.
Cutting to the heart of the matter, there are 4 main tasks in the vulnerability management workflow. If we could automate a major part of these, our process will dramatically improve. Those are:
- Policy-based triaging – The ability to match a vulnerability with external conditions, company policy, and regulatory requirements to filter out irrelevant vulnerabilities. For example, if a vulnerability does not fall under our company’s cyber risk policy, then it can be easily filtered out
- Contextual prioritization and exploit analysis – The ability to understand exactly how exploitable a vulnerability is based on its characteristics combined with the product’s software composition, such as understanding the configuration and component functionality and deciding how relevant it is to the company. For example, if a certain vulnerability cannot be exploited because the file is missing from the final build, as it was not compiled during the build process then you can tag it as “irrelevant”.
- Business risk extraction – The ability to understand the function or impact of our products and business units, and extract the business impact of mitigating a specific vulnerability. For example – if 70% of products planned for release this year have the same vulnerability, fixing it becomes a top priority for the entire business, even if its security score is a bit lower than others.
- Post- prioritization risk management – the ability to conduct detailed investigations with the most relevant data.
The VM Co-Pilot - your AI analyst for vulnerability management
Now for the fun part – in this section, we’ll break down how each of the parts above can be easily automated using the VM Co-Pilot, which automates large portions of the manual vulnerability filtering, by understanding the product’s software composition along with any relevant policies. Let’s begin:
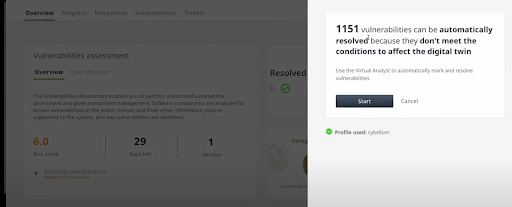
Policy-based triaging
As mentioned above, the first step would be to conduct basic prioritization, filtering out irrelevant vulnerabilities based on company policies, regulatory requirements, or risk score. Using VM Co-Pilot technology, those can be filtered out automatically, as seen below:
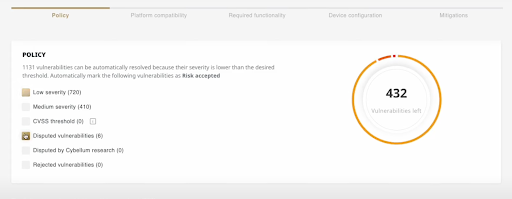
Contextual prioritization and exploit analysis
This is where things become more complicated. Filtering out low-risk vulnerabilities and policy-irrelevant ones is hard enough, but analyzing the exploitability of each vulnerability automatically is next to impossible. To pull that off, you need to have a detailed breakdown of the product’s software, and then match it with the vulnerability details. The VM Co-Pilot does exactly that, by analyzing data like platform compatibility, required functionality (such as drivers or file systems), and device configurations (such as different kernel configurations), to understand which vulnerabilities are actually critical, and which ones are only theoretically so.
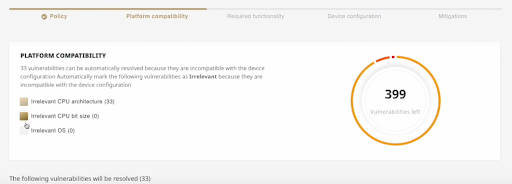
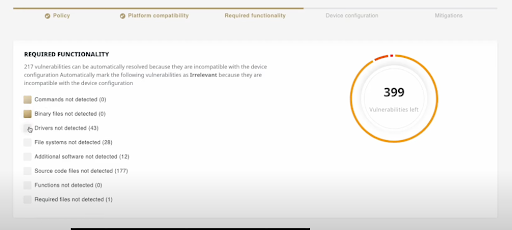
Business risk extraction
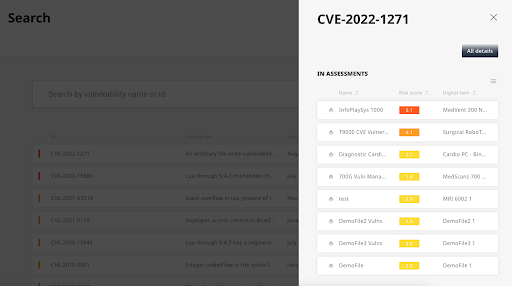
This part is probably the trickiest one to automate. Surfacing the actual business risk of a vulnerability is different for every company and team, and can drastically change based on market conditions and company goals. There are, however, ways of getting invaluable insight automatically, that would help in making more informed decisions about the vulnerabilities’ business impact. For example, using the VM Co-Pilot, it is possible to understand how many product systems and/or product components are affected by a specific vulnerability. That way, managers can decide which vulnerabilities to mitigate first, according to how critical they are for new product launches.
Another way of analyzing the business risk would be to get a high-level view of risk across product lifecycle stages and business units, in order to understand which product lines have bigger cybersecurity gaps that need to be addressed.
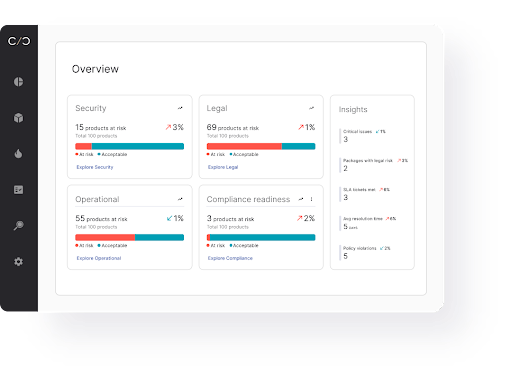
Managing risks post-prioritization
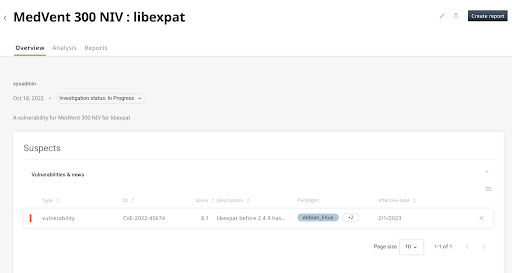
After prioritizing based on the potential business impact and severity, the teams usually open an investigation. The VM Co-Pilot provides teams with all the relevant baseline information, context-aware insights, and asset relationships that are mandatorily required to start the process. Just like a senior surgeon in a hospital, who only enters the operation room after their team arranges all of the required setup, tools, and tasks beforehand, the product security or PSIRT manager makes the process more cost-effective and resource-efficient.
Cutting through the noise, cutting down the cost
Product vulnerability management is more difficult and complex than ever. At the same time, the capabilities needed to manage that complexity are finally available. Using new technologies like the VM Co-Pilot, allows product security teams for the first time to have a reliable virtual analyst by their side, automating a large part of the process and saving huge amounts of time and resources. With cybersecurity AI tools used more and more, it’s time to leverage those advancements into the world of product security.
To learn more about the VM Co-Pilot, reach out.