In the ever-evolving landscape of cybersecurity, staying one step ahead of potential threats is crucial. The adoption of the Common Security Advisory Framework (CSAF) by CISA and other government bodies is a significant stride towards enhancing the vulnerability management ecosystem.
This framework is a new vulnerability reporting format that is heralded by CISA and other government bodies as “critical steps to advance the vulnerability management ecosystem”. Let’s dive into the key aspects of the CSAF framework and understand how it revolutionizes the way we approach vulnerability reporting.
CSAF: A sign of Progress
CSAF goes beyond a reporting format to turn static documents, such as SBOMs and VEX reports into a language that allows us to communicate vulnerabilities systematically. According to CISA, CSAF takes “critical steps to advance the vulnerability management ecosystem.” This goes beyond the previous Vulnerability Exploitability eXchange (VEX) in terms of information fields. One notable improvement is its support for JSON, a feature unavailable in the older CVRF framework.
One of the standout features of CSAF is its ability to convey not only that a product is affected but also its status – whether it has been ‘removed,’ ‘remediated,’ and more. This added layer of information is instrumental in avoiding false positives, ensuring that organizations can accurately assess their vulnerability landscape and take swift action.
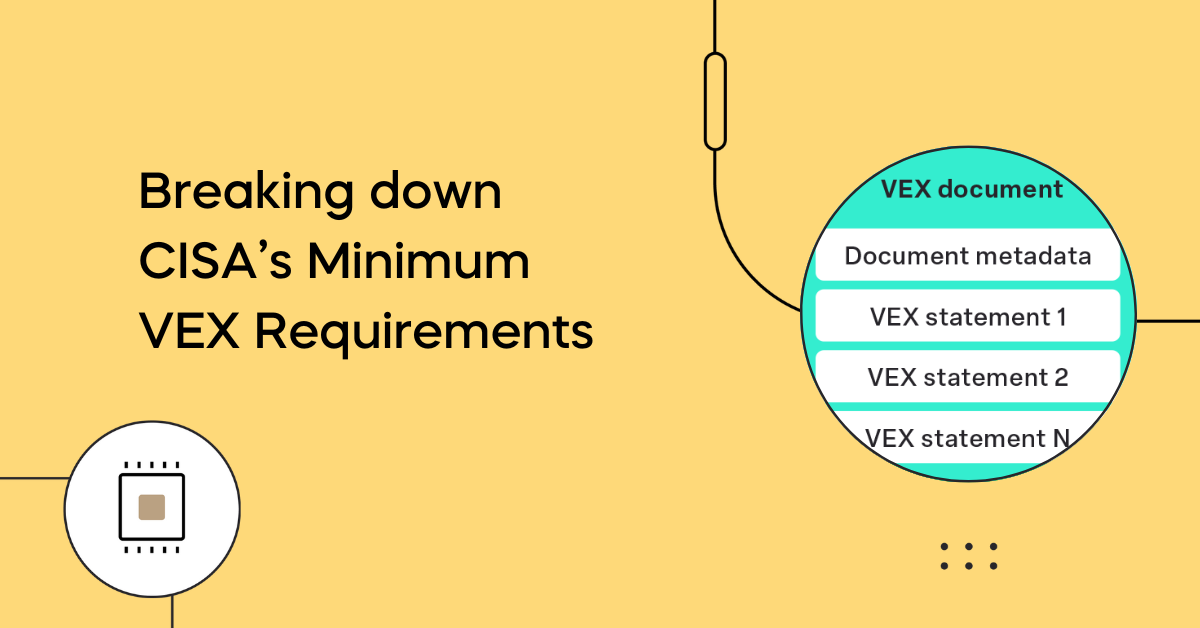
CSAF in action
To truly harness the potential of CSAF, CISA suggests three priorities that work in harmony to manage vulnerability progress, triage, and prioritization effectively.
Achieving automation with CSAF– CSAF is designed to be a standard for machine-readable security advisories. By publishing security advisories using CSAF, vendors can significantly reduce the time required for enterprises to comprehend the impact on their organizations. This paves the way for timely remediation, a critical factor in the ever-changing landscape of cybersecurity.
According to CISA, “CSAF provides a standardized format for ingesting vulnerability advisory information and simplifies triage and remediation processes for asset owners. By publishing security advisories using CSAF, vendors will dramatically reduce the time required for enterprises to understand organizational impact and drive timely remediation.”
Here, the use of CSAF allows for a more streamlined and efficient approach to understanding organizational impact.This is similar to the Product Security Platform’s Vulnerability Management Co-pilot (VM Co-pilot) that works together with automations to scan components, identify both relevant and irrelevant vulnerabilities, then triage accordingly– reducing the need for resource-intensive vulnerability review teams.
Clarifying impact using the Vulnerability Exploitability eXchange (VEX)– VEX serves as a communication tool to determine whether a product is affected by a vulnerability. It plays a vital role in enabling a prioritized vulnerability response. By leveraging VEX, organizations can gain clarity on the potential impact of a vulnerability, allowing them to focus their resources on addressing the most critical threats.
Prioritize based on organizational attributes– To further enhance vulnerability management, frameworks like Stakeholder-Specific Vulnerability Categorization (SSVC) are recommended. These frameworks utilize exploitation status and other vulnerability data to help prioritize remediation efforts based on organizational attributes. This ensures that efforts are directed towards vulnerabilities that pose the greatest risk to the specific context of the organization.
The future of CSAF
The introduction of CSAF marks a pivotal moment in the world of vulnerability management. By providing a standardized language and framework for reporting vulnerabilities, CSAF, along with complementary frameworks like VEX and others, empowers organizations to respond swiftly and effectively to potential threats.
However, the need for automation and additional framework does require additional initial efforts from teams as they understand how to best utilize the tools they have without adding another one. For teams with a mature product security model, CSAF can be implemented by leveraging existing workflows, which already follows internal processes and can develop compliance-worthy reports.
Ultimately, adopting the CSAF framework is a choice made by each individual company– however, the resource investment needed towards adoption won’t be an influential factor on that decision.