Amidst the intricate web of critical infrastructure that shapes our lives, the implications of cyberattacks loom larger than ever before. Our State of Critical Infrastructure Security 2023 delves into the main security challenges faced by today’s equipment manufacturers and sheds light on their priorities. Spanning hundreds of participants employed in key positions such as product security, OT security, cyber security, information security, and cyber compliance, these respondents shared invaluable insights, uncovering the core concerns and obstacles in the ever-changing realm of infrastructure security.
The rising tide of cybersecurity incidents in a software-reliant world
Security incidents involving infrastructure organizations have seen a sharp rise in recent years, with notable cases highlighting the vulnerabilities in our interconnected world. From the Colonial Pipeline ransomware attack in 2021 that crippled fuel distribution, to the 2022 cyberattack on Denso, a vital supplier to Toyota, which led to production line shutdowns, and even the unveiling of the PIPEDREAM malware targeting Industrial Control Systems (ICS), the threat landscape is widespread and dynamic. And while these specific instances have captured headlines, it’s important to recognize that there are many other attacks that have occurred, often without public disclosure.
In this environment, where our reliance on software-driven machinery continues to grow, the stakes have reached unprecedented heights. Our daily lives are intertwined with the operations of software-driven machines, ensuring the food we consume and the products we use are readily available and our critical infrastructure, such as power and water supply, are functioning properly. A successful cyberattack could spell catastrophe, amplifying the urgency of safeguarding these mission-critical networks.
Furthermore, the diversity of software suppliers and supply chains within this landscape widens the attack surface and exposes further vulnerabilities. A prime example is the Log4Shell vulnerability, a prominent case where widely-used open-source software put at risk millions of connected devices, including industrial equipment, globally. Similarly, instances like Ripple20 and Nucleus:13 underscore the risks posed by vulnerabilities in commercial software embedded within countless critical infrastructure assets.
Meanwhile, the convergence of information technology (IT) and operational technology (OT), as well as the trend toward remote maintenance, amplifies the challenge even further. Mission-critical equipment now finds itself more exposed, creating a prime target for ransomware, and a spectrum of cyber threats.
In the face of all of this, it is highly concerning to learn that only 30% of manufacturers believe they possess a mature device security program. We uncovered this insight – and more – in our State of Critical Infrastructure Security 2023. Let’s explore some of the findings further.
There is consensus about the importance of device security
The survey findings unveiled a notable trend in attitudes toward device security within equipment manufacturing companies. A significant majority of survey respondents (82%) firmly believed that device security serves as a competitive advantage, with a substantial number (88%) holding that the proper product security measures take priority over time to market.
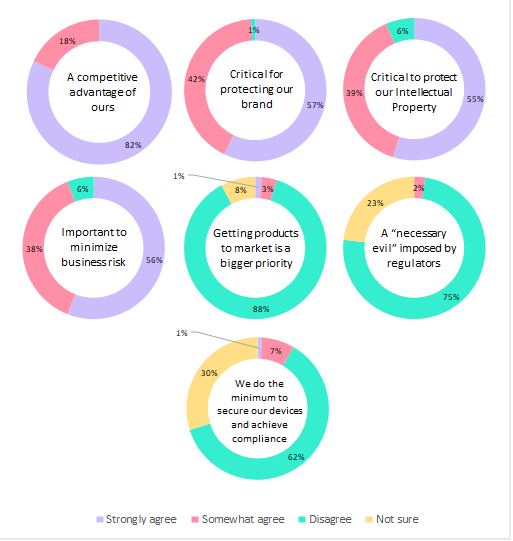
Additionally, all respondents acknowledged the multi-faceted benefits of product security, including safeguarding their brand reputation (99%), minimizing business risks (94%), and gaining a competitive edge (100%).
There was also a consensus that device security plays a crucial role in protecting intellectual property rights (94%), with the EU and APAC regions exhibiting even stronger agreement compared to the US. These results not only reflect responsible attitudes towards device security but also emphasize its vital role from a business perspective.
The survey also highlighted that an overwhelming majority of respondents (98%) recognized the paramount importance of device security for OT (Operational Technology) network security.
Read our blog The Role of Device Security in Overall Industrial Network Security to learn more about the critical importance of device security.
However, a critical question arises regarding the translation of this understanding into actionable measures. Does the recognition of the problem ultimately lead to effective implementation?
Infrastructure product security programs are still immature
One of the key findings of the survey regarding the immaturity of device security programs in infrastructure equipment manufacturers indicates that an understanding of the importance of device security does not yet translate into action. As mentioned in the introduction, only 30% of the surveyed organizations believe they possess a mature device security program, indicating that the majority still have a long way to go in terms of their cybersecurity capabilities.
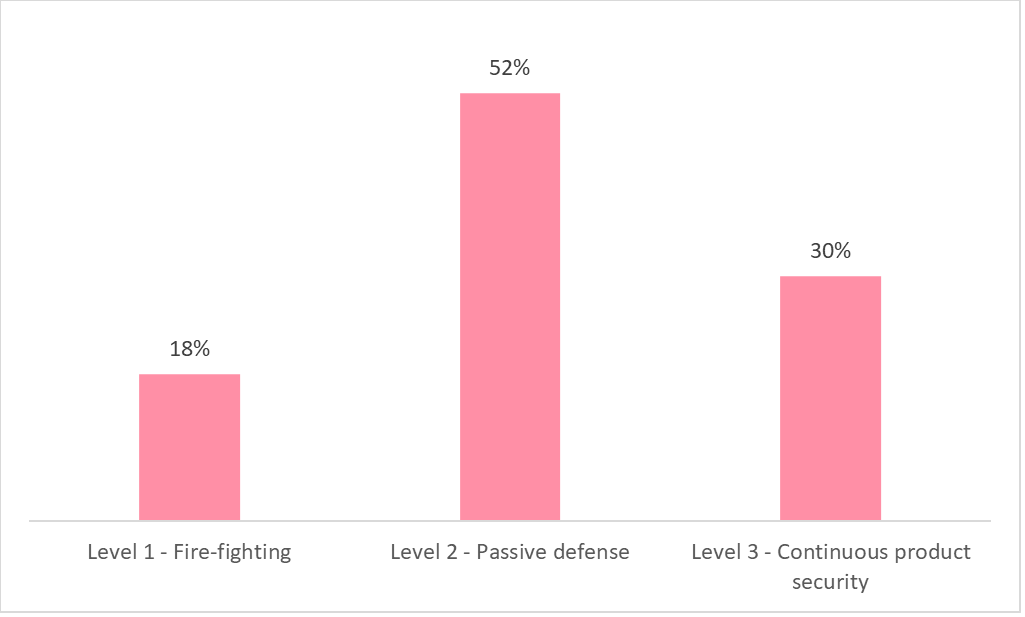
The levels of program maturity were defined as follows:
- Level 1 – Fire-fighting: Product security processes are unorganized, security scans performed just only at the end of development, highly manual work, major compliance gaps, no threat or device monitoring post production. Success relies on individual efforts, and isn’t repeatable. TTM suffers.
- Level 2 – Passive defense: Partially defined processes with few assigned resources. Basic product security practices are implemented periodically using disconnected generic or homegrown tools, with plenty of manual work. Compliance improves, but is inconsistent. TTM is at risk and there are security gaps post production.
- Level 3 – Continuous product security: Resources are available at the executive and practitioner level. A dedicated process is in place with high-degree of automation for both product security and compliance activities, covering the entire product portfolio from design to post production. Products get to market much faster and stay there, while minimizing risk.
The immaturity of device security programs may be related to the lack of a dedicated device security function within the organizational structures of many industrial organizations, something we explore further in our full report.
Furthermore, when examining device security budget changes in 2022 and 2023, the survey found a lack of financial investment in device security, uncovering an overall lack of intention to increase product security budgets in 2023.
Altogether, these findings indicate a lack of focus on device security and a conservative stance on resource allocation, surprising in the face of a general agreement on the importance of device security.
Uncovering product security challenges and priorities
Next, we sought to explore the specific challenges that infrastructure organizations face with device security. Overall, we found that there are many different challenges that companies are grappling with, each having a varying impact on smaller and larger companies. We discuss these challenges, as well as how they can be addressed through the adoption of a comprehensive platform designed for device security, in our blog Challenges in Keeping Industrial Devices Continuously Secure.
When examining the top priorities for organizations’ 2023 device security roadmap, compliance with regulations and standards came out on top. Our survey delved deeper into which regulations respondents are already in compliance with, which they plan to comply with in 2023, and which they have no plans for, including differences in responses between the US, EU, and APAC regions.
An additional finding that may surprise readers is the discovery that survey respondents put a relatively low priority on supply chain security, even in light of surging cyber attacks originating from the software supply chain. This indicates the urgent need for industrial equipment manufacturers to prioritize and enhance their software supply chain security measures. For more on our findings and best practices for how to improve supply chain security, read Equipment Manufacturers are Grappling with Software Supply Chain Security.
Unlocking a safer future: delve into the insights of our complete survey report
The above peek into the world of device security has only scratched the surface of what our comprehensive survey report has to offer. Within its pages lie valuable insights that can empower your organization to navigate the complex realm of cybersecurity with confidence and clarity.
As you’ve followed our journey through this preview, you’ve caught glimpses of the challenges that infrastructure organizations grapple with, the evolving threat landscape they face, and the critical importance of device security. The full report takes you on a more profound exploration, providing a nuanced understanding of the issues and offering actionable solutions that can reshape your approach to security.
Download the complete State of Critical Infrastructure Security 2023 report now and equip yourself with the knowledge needed to embrace a more secure future.